To AGM - To AGM/Next - To AGM TeamReports Overview - To AGM Members Reports Overview
Team Reports 2012
Team Leaders are encouraged to present a report for their team.
1.
{g}
2.
{g}
3.
{g}
4.
{g}
5.
{g}
6.
{g}
7.
{g}
8.
{g}
9.
{g}
10.
{g}
11.
{g}
12.
{g}
13.
{g}
14.
{g}
15.
{g}
Policy Group's Year of Conquest!
Policy Group didn't passed as much as discussed in 2011-2012
Topics of discussions in Policy Group
2011 2nd half
- July 2011
Requesting assistance for a document creation: Donations -> "strict guidelines" please provide reference
- August 2011
- Organisation Assurance Policy: Approval for "Unternehmensregister.de"
- OAP review - 0.Preliminaries
- October 2011 (starting)
- (CPS) bug report # 0000540: No key usage attribute in cacert org certs anymore?
- (CPS) CPS and keysize
- (CPS) Uncontroversial changes to the CPS
- CACert Root Distribution for Fedora
- November 2011
- Fwd: Mozilla Security Blog regarding compromise of 512-bit certs
- Software Freedom Law Center (SFLC) (communication with Red Hat)
- p20111113 CPS #7.1.2 "Certificate Extensions" adjustments
- Key Usage changes and PDF signing
- ios5 bug also handled by these changes ?!? : Key Usage changes and PDF signing (p20111113 CPS #7.1.2 "Certificate Extensions" adjustments)
- Baseline Requirements (BR)
- All Assurances to expire? (followup BR discussion)
- December 2011
- Finding assurers
- 39 Month Rule (followup BR discussion)
- DEPRECATING some older WIPs?
- Assistance request to Policy Group regarding software bug#920 - Join - single name only (eg Indonesian)
- Rework of CPS needed
2012 1st half
- January 2012
- Java Code Signing Inclusion
- Current version of CAP form
- Fedora Licensing Issues
- (RDL) base definitions of certificate activity
- (PoP) by default, move DRAFTs to POLICY after one year
- February 2012
- Outsourcing Assurances
- Fwd: CAcert Root Distribution License vs. NRP-DaL
- Org. Assurance (PL)
- (RDL) Examples of Use Restrictions by Other CA's
- (RDL) Alice and Bob
- (RDL) Re: Governing Law
SubCa certs
- March 2012
- Privacy issue
- Requirements for further development
- expiration of Validated domains
- April 2012
- DRAFT OAP to be moved to POLICY / main site?
- June 2012
- UEFI Secure Boot Signing
Policy Decisions
Despite the fact Policy Group has discussed many aspects only one topic moved into a change of an existing policy
p20111113 CPS #7.1.2 "Certificate Extensions" adjustments
- Motion CARRIED. Consensus of 24:0. Voting closed 20111128
- 24 voters in total
- 24 Ayes
- 0 Abstains
- 0 Nayes
- References
Significant Events
2011-11-16 Baseline Requirements Draft 50 has been published
- that leads to several policy group discussions
2011-11-28 p20111113 CPS #7.1.2 "Certificate Extensions" adjustments
- Motion CARRIED. Consensus of 24:0. Voting closed 20111128
Future Work - Stuff we'll predict we'll do next year
None of the Future Work proposed in 2011 has been picked up, so still open
- Review and vote for:
Root Distribution License to POLICY
TTP Assisted Assurance Subpolicy to POLICY
- Older DRAFT policy that needs review and vote to POLICY
Certification Practice Statement (Draft: p20091108)
Policy on Junior Assrurer/Members (Draft: p20100119)
- Updates
Organisation Assurance Policy (Updates)
- An update has been started but not finished yet.
- continue started update deployment
By lack of a Policy Officer role (currently held by board) nobody seems to be responsible for coordination of Policys management (check policy states, reminder for voting from DRAFT to POLICY, WIP to DRAFT) and to manage a Policy repository migration plan.
Ulrich Schroeter
Audit Team Report 2012
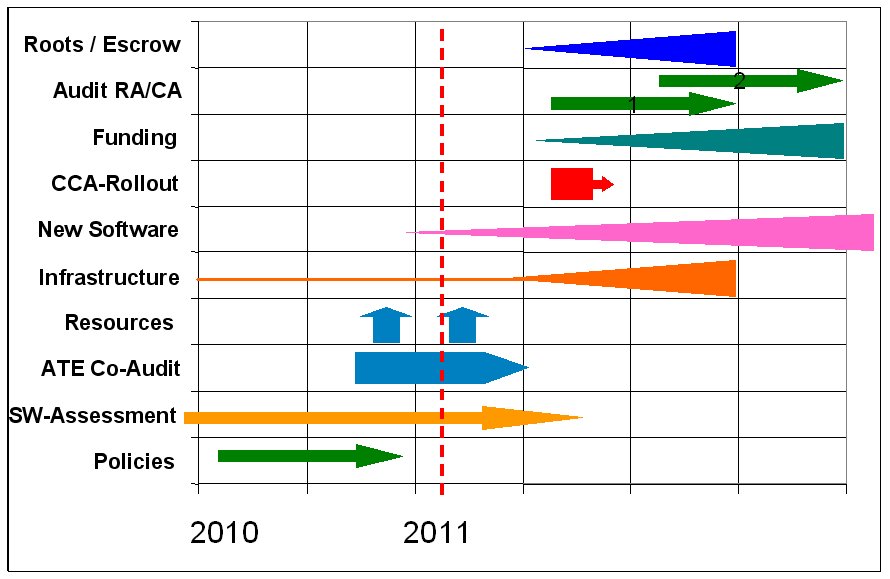 From the 2011 team report the (co)-audit plans continued by following the masterplan as published in October 2010. But in 2011 second half, a couple of disturbing messages received us, that the commercial CAs and Browser vendors are working on a new audit criteria document: Baseline Requirements (BR). The Baseline Requirements Draft 5.0 becomes published in November 2011. This document signals a *significant impact* to CAcert and therefor CAcert's path to an Audit.
From the 2011 team report the (co)-audit plans continued by following the masterplan as published in October 2010. But in 2011 second half, a couple of disturbing messages received us, that the commercial CAs and Browser vendors are working on a new audit criteria document: Baseline Requirements (BR). The Baseline Requirements Draft 5.0 becomes published in November 2011. This document signals a *significant impact* to CAcert and therefor CAcert's path to an Audit.
The quick summary: One side-effect of BR is that there are now multiple audits to pass to become a top-tier CA. Depending on how they are counted, CAcert can now expect to have to deal with 3 different audit processes: BR, WebTrust and EV.
 Read also Boards Strategy
Read also Boards Strategy
For the co-audit team and other teams working on the Big Masterplan to become Audit Ready continued their work, as they'll work for an internal audit. To work on procedures and process following existing policy and deploying not yet existing procedures.
The projects in detail:
Policies
CPS did undergo an update that was caused by a software bug and moved forward to Policy Group to be decided by Policy Group. The p20111113 CPS #7.1.2 "Certificate Extensions" adjustments motion CARRIED on 2011-11-28.
The list of Policies awaiting a decision to move from DRAFT to POLICY (expecting a one year hold time after voted to DRAFT)
Policy
State
Vote to DRAFT
awaiting review and vote to POLICY
RDL
DRAFT
p20100710
since p20110710
DRP
DRAFT
partly p20110108
since p20120108
CPS
DRAFT
partly (1) p20091108, (2) p20111113
(1) p20101108, (2) p20121113
CCS
DRAFT
p20100426
p20110426
PoJAM
DRAFT
p20100119
p20110119
SP
DRAFT
p20100510
p20110510
TTP
DRAFT
p20100913
p20100913
and a long list of OAP subpolicies
One of the causes of Audit stop in mid of 2009 that was adressed as "Because of the long time it takes for getting policies accepted in the far-flung CAcert Community and CAcert Board" didn't make succeess in 2011/2012 too. Despite the fact a couple of topics were presented before the Policy Group, only one gets picked up and has been passed.
Software-Assessment
Software-Assessment passed a couple of patches according to their deployed procedures. One patch that passed end of November 2011 gots the attention from the Community. This was the "New Points Calculation" patch (as an interim patch for the planned audit related Tverify Assurance Points to expire patch). This update has been announced with a prepared scripted mailing, that can be also seen as a pilot for the CCA-Rollout project that relates to the DRC requirement, to notify each member about the CAcert Community Agreement (CCA) and requests acceptance by the member.
So other audit related software patches are still in the working queue that didn't finished until end of reporting period:
- Tverify points to expire (removal of Tverify assurance points)
- PoJAM Assurance subpolicy requirements implementation
- New TTP-assisted-assurance subpolicy requirements implementation
- CCA Rollout
ATE / Co-Audit
 Caused by the Software-Assessment project mailing "Changes at CAcert: New Points Counting" that includes the "Tverify points to expire (removal of Tverify assurance points)" topic and the "New Points Calculation" topic, CAcert received responses from the Community, that results in a couple of requests for an ATE from UK, US, Sweden. So at the end one ATE in the UK, and 4 ATEs in Germany did happen. The running machine to collect co-audit results is currently unavailable. So currently publishing of co-audited assurances results is impossible.
Caused by the Software-Assessment project mailing "Changes at CAcert: New Points Counting" that includes the "Tverify points to expire (removal of Tverify assurance points)" topic and the "New Points Calculation" topic, CAcert received responses from the Community, that results in a couple of requests for an ATE from UK, US, Sweden. So at the end one ATE in the UK, and 4 ATEs in Germany did happen. The running machine to collect co-audit results is currently unavailable. So currently publishing of co-audited assurances results is impossible.
Infrastructure separation
In the meanwhile the infrastructure team worked on an interim plan to move all infrastructure servers from the critical system out to another machine within BIT, Ede. Plans to move the non-critical infrastructure out of BIT, Ede to another hosting center has been set on hold as current state has fixed one audit wish to separate the non-critical systems from the critical systems.
New Software / BirdShack
Currently there are no news about this project.
CCA Rollout
The preparation to get a CCA-Rollout passed has been handled by the Software-Assessment project team with the pilot mass mailing to the members. There are other preparations that requires further software development, so the CCA-Rollout can pass. Current state: not yet finished, but one step forward.
New Roots & Escrow
This project has been deferred to a completed risk management analysis. A CAcertRootKeySRA-DRAFT-0.91 DRAFT document has been written. No further work done yet. Current state: project stalls
Audit over RA, Audit over CA
Since the Baseline Requirements Draft 5.0 has been published, plans for an Audit in general stalls. Within the co-audit team the plan is to continue with the "internal audit" but the general audit plans were set on hold. The co-audit over assurance team continued their work with the ATE series and co-audits according to the plans deployed back in 2009 and 2010. But without a strategy plan for an internal audit this work decreased in priority.
CrowdIt
This project did not get any attention from within the Community. The main reason here: the audit plans have stopped. So there is currently no need to continue with this project, to transfer practicle results into an audit documentation. This may change in the future, once an internal audit will be pushed.
What has happened to audit in the interim?
The intro of this report is focused on the Baseline Requirements Draft 5.0 and the *impact to CAcert*. The result of thinking was in summary:
One side-effect of BR is that there are now multiple audits to pass to become a top-tier CA. Depending on how they are counted, CAcert can now expect to have to deal with 3 different audit processes: BR, ?WebTrust and EV.
- For various reasons this process is too expensive.
and did find their final statement in the Boards Strategy statement.
Prospective View
There are two possible ways to go:
- move audit plans to an internal audit only
- rethink the Baseline Requirements and go in distance to them
- cause: DRC has been adopted for a Community based CA. It includes several variations of audit requirements that aren't applicable to a Commercial CA and vss. So Baseline Requirements cannot cover a Community based CA requirements.
- The main reason here: Commercial CAs are closed organisations. The Community CA is a CA of another type, that predicts Openess and Transparency, so thats why the Community based CA receives more and more acceptance in the world of CAs by their consumers and probably by security experts. This has to become subject to an open discussion in the upcoming months.
Ian Grigg, UlrichSchroeter
Infrastructure Team Report 2012
 The remaining non-critical infrastructure systems were moved from Sun2 to the new LXC based infrastructure host Infra01 by Mario with assistance from their administrators.
The remaining non-critical infrastructure systems were moved from Sun2 to the new LXC based infrastructure host Infra01 by Mario with assistance from their administrators.
The update status of the infrastructure systems is not in the shape Mario and I would like to have it in. Some systems are still running Debian Lenny (which is without security support since February 2012), others are running the even older Debian Etch release (without security support since January 2010). There are some positive examples though, that are well maintained and running the latest security patched Debian Squeeze release: Infra01, Bugs, Issue, Monitor, Svn, Translations. The two systems intended to replace the current mail infrastructure in future, Ldap and Mail, are already using the next planned Debian release Wheezy, which is in deep freeze now.
 We (Mario and I) urge all admins of the outdated systems to upgrade their software or to ask for help. It is important to know that Debian only supports apt-get dist-upgrade from one release to the next, so the oldest systems have to go from Etch to Lenny to Squeeze and later to Wheezy if the security support for Squeeze ends. The upgrades should be easy in most cases, because only a tiny amount of services is running on each of the systems. If help is required, you can ask at cacert-sysadm@lists.cacert.org or ask me directly via mail or IRC.
We (Mario and I) urge all admins of the outdated systems to upgrade their software or to ask for help. It is important to know that Debian only supports apt-get dist-upgrade from one release to the next, so the oldest systems have to go from Etch to Lenny to Squeeze and later to Wheezy if the security support for Squeeze ends. The upgrades should be easy in most cases, because only a tiny amount of services is running on each of the systems. If help is required, you can ask at cacert-sysadm@lists.cacert.org or ask me directly via mail or IRC.
The infrastructure team is lacking a clear list of tasks for existing and new team members and unfortunatelly we have no good guidelines describing the responsibilities of system administrators. Some new system administrators were recruited. However, it seems that they do not get on track, since no handover of previously orphaned systems was possible and they seem to hesitate with required bigger changes in order to not break currently running systems.
In my role as svn.cacert.org administrator I started an analysis of the existing accounts for the Subversion repository. Some of the account names (and their passwords) are older than my access to the system (before mid 2009) and I can not trace them back to their owners. I would like to disable all accounts that I do not know and that had no commit activity in the Subversion repository for more than two years.
Arbitration Team Report 2011-2012
The year in Arbitration
Arbitration Team Meetings
Arbitration team meetings did not happen in the reporting period.
The Team
 From the 12-13 listed Arbitrators only 1-2 worked continously along the reporting period and counts as active arbitrators. We had continously about 5-8 arbitrators marked busy in this period and continously 5 inactive ones who shows no sign of activity nor any other presence to arbitration. A red flag has raised first documented under Overview Projects Board in May 2011 that arbitration team is in a mess and also continously announced to the board that find its way into the Board Action Items plan, first picked up by Board around September/October 2012 (after this report period)
From the 12-13 listed Arbitrators only 1-2 worked continously along the reporting period and counts as active arbitrators. We had continously about 5-8 arbitrators marked busy in this period and continously 5 inactive ones who shows no sign of activity nor any other presence to arbitration. A red flag has raised first documented under Overview Projects Board in May 2011 that arbitration team is in a mess and also continously announced to the board that find its way into the Board Action Items plan, first picked up by Board around September/October 2012 (after this report period)
Precedent Cases
Within the reporting period two new finished Precedent cases has been ruled that effects
- Account removal, Delete Account cases
- add full middlename to accounts refering to name change request cases
The first one is the first attempt to get rid of the increasing "Delete my Account" requests, that flooded arbitration queue in the past two years, that gives authority to a Support-Engineer, to process the Delete Account procedure if the member has no remaining active certificates and did not give one assurance. This precedent ruling closed 12 similar cases by time of ruling and 35 further tickets have been handled by Support following the precedent ruling. So this means, this precedent ruling prevented Arbitration to be filled with 35 addtl. "Delete my Account" cases.
Precedent Cases Overview
Arbitration Precedent Case
Handled following precedent by Support or Critical team
7
6
name change with precedent case (several different precedent cases)
21
30
a20100210.2 Revoke assurance 24 hours / 3 days / 7 days after an event
17
a20111001.1 Dispute misssing points after applying bug fix 827 (new point calculation)
18
47
1
Total
147
Documentation of Name changes precedent cases is under Support authority within Supports ticket system so therefor here the count of cases is derived from Support report.
Decreasing Arbitration Backlog
 The work on decreasing arbitration backlog was unsuccessful.
The work on decreasing arbitration backlog was unsuccessful.
89 new cases within report period relates to 56 closed cases. This is (again) an increase of 33 cases.
New Arbitrators
In 2012 first half the team has been increased by 1 arbitrator. A 2nd returning arbitrator has been nominated after the reporting period.
Arbitration future prospects
The situation in Arbitration didn't changed much related to previous year Arbitration team report.
With 1-2 active arbitrators, fast processing of cases was reduced to emergency cases handling upto an intermediate ruling.
 So the first change becomes possible after the reporting period finished by the arbitration team meeting scheduled by board action. In the meeting a modification to DRP was proposed to change the default arbitration process to a 2 tears level (beside the appeal process under DRP 3.4).
So the first change becomes possible after the reporting period finished by the arbitration team meeting scheduled by board action. In the meeting a modification to DRP was proposed to change the default arbitration process to a 2 tears level (beside the appeal process under DRP 3.4).
- Tear 1:
- unexperienced arbitrators helping to rule on simple cases
- Tear 2:
- experienced arbitrators to pick up heavy cases
A DRP update proposal has been suggested, needs to be written and proposed to Policy Group
Beside this, the search for experienced assurers who can actively increase the active team is still running.
Arbitration Statistics
Statistics by Year (FY)
FY 2011-2012 Cases Closed
Cases closed
from year2011
2012
Still open/
running totalsJul
Aug
Sep
Oct
Nov
Dec
Jan
Feb
Mar
Apr
May
Jun
2009
0
0
0
0
0
0
0
0
0
0
0
0
5 {r}
2010
0
4
1
2
0
0
0
0
0
0
0
0
21 {r}
2011
2
0
7
4
7
5
11
3
2
1
1
0
32
2012
0
0
1
1
3
1
33
Total
2
4
8
6
7
5
11
3
3
2
4
1
91
Total New
0
10
7
10
16
7
8
4
8
6
6
7
89
Active Arbitrators
1
1
1
1
2
2
0
2
2
1
2
0
1
Arbitration table 1
Statistics period July 2011 - June 2012
Arbitrations
2011
2011
2011
2011
2012
2012
2012
2012
Sum
Quarterly snapshot
Jul
Aug
Sep
Q3
Oct
Nov
Dec
Q4
Jan
Feb
Mar
Q1
Apr
May
Jun
Q2
New = Total
0
10
7
17
10
16
7
33
8
4
8
20
6
6
7
19
89
Running
0
8
7
15
2
1
1
4
8
4
8
20
6
4
6
16
55; Ø 4.5/month
Closed new
0
2
0
2
2
1
1
4
0
0
1
1
0
2
1
3
10
Closed total
2
4
8
14
6
7
5
18
11
3
3
17
2
4
1
7
56
Total
0
10
7
17
10
16
7
33
8
4
8
20
6
6
7
19
89
Arbitration table 2: statistics per period (seperated into quarters)
Number Arbitrators
2011
2011
2011
2011
2012
2012
2012
2012
Jul
Aug
Sep
Q3
Oct
Nov
Dec
Q4
Jan
Feb
Mar
Q1
Apr
May
Jun
Q2
on list
12
12
12
12
12
12
12
12
12
12
12
12
12
13
13
13
inactive
5
5
5
5
5
5
5
5
5
5
5
5
5
5
5
5
busy
6
6
6
6
6
5
5
5
7
5
5
6
6
6
8
7
active
1
1
1
1
1
2
2
2
0
2
2
1
1
2
0
1
Arbitration table 3: Arbitrators active/busy/inactive
Long term statistics 2008 - 2012
Arbitration
2007
2008
2008
2009
2009
2010
2010
2011
2011
2012
Total
Cases
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
New = Total
2
2
0
3
1
0
8
38
29
33
56
16
23
17
35
24
17
33
20
19
376
Running
0
0
0
0
0
0
0
1
3
1
10
8
5
5
11
18
15
4
20
16
117
Closed
2
2
0
3
1
0
8
37
26
32
46
8
18
12
24
6
14
18
17
7
281
Total
2
2
0
3
1
0
8
38
29
33
56
16
23
17
35
24
17
33
20
19
376
FY Total
7
47
134
99
89
376
Year Total
4
4
108
112
109
39
376
Arbitration table 4: Long term Arbitration statistics new/running/closed
Arbitrators
2007
2008
2008
2009
2009
2010
2010
2011
2011
2012
Active
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
on list
1
1
1
4
5
5
8
11
13
13
15
14
12
12
12
12
12
12
12
13
inactive
4
4
3
3
3
4
5
5
5
5
busy
7
6
5
5
6
6
6
5
6
7
active
1
1
-
3
1
-
5
9
10
6
5
4
5
5
3
2
1
2
1
1
Arbitration table 5: Long term statistics Arbitrators active/busy/inactive
Software-Assessment-Project Team Report 2011-2012
 Back by end of 2009 the team started working. The team consists of team members from several areas (dependent on current running special projects), so not only from area Software-Assessment, but also Support-Engineers, Arbitrators, Board-members, Critical team members, Software-developers, Software-testers, PR team members.
Back by end of 2009 the team started working. The team consists of team members from several areas (dependent on current running special projects), so not only from area Software-Assessment, but also Support-Engineers, Arbitrators, Board-members, Critical team members, Software-developers, Software-testers, PR team members.
The team has weekly Tuesdays telco meetings via a telco server that is provided from the Community member Kees van Eeten from the Netherlands. The meetings will be minuted under the project wiki page Software/Assessment
The priority of projects given by the team:
- "Thawte points removal patch" aka "New points calculation"
- Critical system fixes
- Support and Organisation-Assurance area fixes
- Policy requirements fixes
- CCA-rollout
The patch processing has been installed in parallele processing way, so emergency patches can be passed beside long running tests patches.
The year in Software-Assessment-Project Team
Emergency Patches Procedure
 An Emergency Patches procedure has been proposed and documented under Emergency Patches.
An Emergency Patches procedure has been proposed and documented under Emergency Patches.
The teams Software-Assessment and Critical team worked and discussed and voted on the proposal.
Thus we have 3 emergency patch strategies in the following order of escalation:
- Emergency patches fast path thru the regular software development update cycle (preferred choice)
- Critical sysadmin applies a patch to the critical system given by a Software-Assessor
- Critical sysadmin gives remote access to a software-assessor or software-engineer with critical admin control
For further details read above linked document.
Thawte Patch, New Points Calculation
The "Thawte" patch (read detailed report from last year) moved forward with the step 1 patch: "New points calculation". So all efforts were made to also start an "all-members notification" by a variation of the known scripted mailing for events procedure (Arbitration case a20090525.1). This "all-members notification" mass mailing to all members can be seen as the pilot to the audit project CCA-Rollout.
The bug #827 patch named "Tverify points to be deprecated" has been installed on 2011-11-16. Other names the patch has circulated: "New points calculation page" -or- "15.php patch"
The mass mailing (notification) to all members (regarding new points calculation) started 2011-11-27 and tooks about 2-3 days to complete ![]()
Teams involved and decisions
- Software-Assessment project team
- to prepare the framework that patch can be applied, members to notify
- Software-Assessment team
to pass bug #827
- Software Test team
to test the bug #827
- Critical sysadmin team
to install the bug #827 patch to the critical system
- Arbitration
(in development period of the patch) Arbitration case a20100822.1 to evaluate special criterias that needs to be catched for the New points calculation patch
(in development period of the patch) 2nd Arbitration case a20101114.1 to evaluate special criterias that needs to be catched for the New points calculation patch
ruling a20100309.1 with instructions to start a mass mailing and further authorizations required
- running/open cases following notifications to all members:
a20111001.1 "Dispute misssing points after applying bug fix 827"
a20111019.1 "Missing points after applying bug fix 827"
a20111129.5 "Dispute - discrimination and victimisation"
- Board
motion m20111016.2 Allow the PR group to send out an email
motion m20111023.2 New Points Counting Newsletter
- Public Relations team
to prepare the "newsletter" and to publish the text on the blog Changes at CAcert: New Points Counting
- Support team
- briefing of Support team and potential members questions regarding new points calculation
Summary:
- 8 teams involved
- 1 bug filed
- 3 pre-project Arbitration cases
- 3 post-project Arbitration cases
- 2 Board motions
Webdb database upgrade
 Another project that has been started under bug #976 "database restructure preparation" one can read as another precedure deployment how a database structure update can be passed to the production system.
Another project that has been started under bug #976 "database restructure preparation" one can read as another precedure deployment how a database structure update can be passed to the production system.
The reason to have such a procedure at hand are feature requests that requires an update to the database structure on the critical system that falls under SP.
With the patch bug #976 installed on 2011-11-25 the Software-Assessment team enters another milestone for auditable procedures under SP
Teams involved and decisions
- Software-Assessment project team
- to prepare the framework that patch can be applied
- Software-Assessment team
to pass bug #976
- Software Test team
to test the bug #976
- Critical sysadmin team
to install the bug #976 patch to the critical system by following the procedures deployed by the Software-Assessment team
Summary:
- 4 teams involved
- 1 bug filed
Translation replaces Translingo
- Move from translingo to pootle (Translation system changed)
- A new server has been installed in the non-critical infrastructure area
- The self developed Translingo system has been replaced by the new Translingo system running on Pootle
Teams involved and decisions
- Non-critical Infrastructure team
- deploy a new virtual machine
- Software-Assessment project team
- to prepare the framework that patch can be applied
- Software-Assessment team
to pass bug #985 "Move from translingo to pootle"
- Software Test team
to test the bug #985
- Critical sysadmin team
to install the bug #985 patch to the critical system by following the procedures deployed by the Software-Assessment team (update procedures)
Summary:
- 5 teams involved
- 1 bug filed
Permissions Review project
- Provide a possibility to regularly review the permissions in the system
- patch submitted: 2011-12-28
- This was a feature request from board. There should be a possibility to have a look at which permissions are held by whom. This could be a recurring mailing initiated by a cron job or a page where those are listed (or both).
related Arbitration case a20110118.1
- "requests List of Admins, request list of TTPadmin's, identify all organisation administrators that are not CAcert assurer"
Teams involved and decisions
- Software-Assessment project team
- to prepare the framework that patch can be applied
- Software-Assessment team
to pass bug #1003
- Software Test team
to test the bug #1003
- Critical sysadmin team
to install the bug #1003 patch to the critical system
- Arbitration
Arbitration case handled and intermediate ruled a20110118.1
- Support (2011-01-18)
1st dispute filing a20110118.1: List of Admins (Support-Engineers) in the database
- Board (2011-12-28)
filed as bug #1003 (handled under a20110118.1)
- Organisation Assurance (2012-03-26)
2nd dispute filing, case merged a20110118.1: identify all organisation administrators that are not CAcert assurer
Summary:
- 8 teams involved
- 1 Arbitration case
- 1 bug filed
Further projects
- Support, Organisation Assurance area related patches
- Most patches enhanced the Support-Engineer admin console with some specific, addtl. informations to handle eg. Arbitration related Delete my Account cases (count of active/revoked/expired certificates), account state that helps to identify flag problems under an account, enhancement for the new points count calculation
- For Organisation Assurance, enhancements for the OA's admin console have been implemented (sort order of tables, addtl. comment fields, and more)
The Software-Assessors team
Team Development
In 2010/2011 the team got 2 new Software-Assessors with the hope, to increase the count of active Software-Assessors. But in 2011/2012 the count of active Software-Assessors stalls at 1.5 For passing successfuly any software bug fix to the Critical team 2 Software-Assessors are required to review the patches. This burdened the team and the search for addtl. active Software-Assessors still continued (made success in the post-reporting period with Benny Baumann by Board motion m20121017.3)
Michael Taenzer, who moved from Support t/l to Software-Assessment one year ago becomes more and more the team leader. So the Software-Assessment project team proposed Michael to become the Software-Assessment team teamleader as the seat was vacant since spring 2010 (fallback Board).
The nomination of Michael Taenzer has been accepted by Board with the motion m20120623.1 at committee meeting 2012-05-23
The Software-Testteam
The Software testers team is a loose team of individuals who assist in software testing dependent on patches, difficulty of patches, knowledge, and time. eg. for the iOS5 bug, we had other software testers then for the Thawte Points Removal patch. So this makes it difficult to build up a working software testers team.
In the past often we had the problem, that one did some testing and disappeared thereafter 'cause the next patch to test did come weeks later. To restart the Software Testers Reward Challenge 2011 we did run around eastern 2011 results, that we did not got one more software tester into the team. So we are still at the same point here.
Prospective view is, that the team may increase one day, we've found some more Software developers and patches gets passed faster.
Software Developers
In the last 3 years software developers were recruited from the Software-Assessment project team. Now with the fixed bottleneck on active Software-Assessors we now search for Software developers who are able to code in PHP.
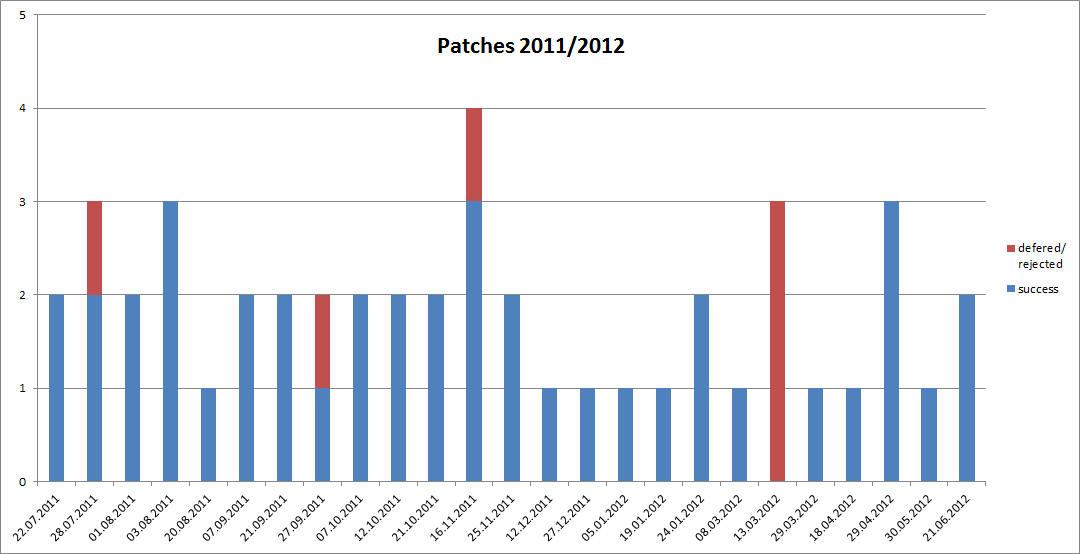
Statistics
07/2011 - 06/2012
#
Date deployed
success
defered/rejected
Remarks
1.
2011-07-22
2
0
2.
2011-07-28
2
1
3.
2011-08-01
2
0
4.
2011-08-03
3
0
5.
2011-08-20
1
0
6.
2011-09-07
2
0
7.
2011-09-21
2
0
8.
2011-09-27
1
1
9.
2011-10-07
2
0
10.
2011-10-12
2
0
11.
2011-10-21
2
0
12.
2011-11-16
3
1
13.
2011-11-25
2
0
14.
2011-12-12
1
0
15.
2011-12-27
1
0
16.
2012-01-05
1
0
17.
2012-01-19
1
0
18.
2012-01-24
2
0
19.
2012-03-08
1
0
20.
2012-03-13
0
3
moving out rejected patches
21.
2012-03-29
1
0
(#1003)
22.
2012-04-18
1
0
(#1027)
23.
2012-04-29
3
0
(#1002), (#1011), (#1033)
24.
2012-05-30
1
0
(#1023)
25.
2012-06-21
2
0
(#1003), (#1038)
25
cyclesTotal 2011/2012
41
6
293%
2 / month
Ø / month
3.42
0.5
7
cyclesTotal 2010/2011
14
2
100%
0.5 / month
Ø / month
1.17
0.17
07/2012 - today
#
Date deployed
success
defered/rejected
Remarks
1.
2012-07-04
1
0
(#967)
2.
2012-07-25
2
0
(#789), (#1075)
3.
2012-07-27
1
0
(#540)
4.
2012-08-10
2
0
(#981), (#1024)
5.
2012-09-17
1
0
(#1019)
6.
2012-10-13
1
0
(#1091)
7.
2012-10-23
1
1
(#835) finished, (#440) rejected
8.
2012-11-01
6
0
(#978), (#922), (#977), (#1080), (#1083), (#860)
8
cyclesTotal 2012/today
15
1
Benny Baumann, Martin Gummi, Marcus Maengel, Ulrich Schroeter
Critical System Administrator Team Report July 2011 - June 2012
Hardware changes
 No major changes were made to the hardware infrastructure for the CAcert servers in the past reporting period. A couple of failing components had to be replaced though: a broken disk on the infrastructure server, a broken disk on the signing server, and two Linksys switches (which were replaced by a single Cisco switch).
No major changes were made to the hardware infrastructure for the CAcert servers in the past reporting period. A couple of failing components had to be replaced though: a broken disk on the infrastructure server, a broken disk on the signing server, and two Linksys switches (which were replaced by a single Cisco switch).
On-site activity
The log of visits to the hosting facility shows the following "on site" activities:
- [15.07.2011] replace broken switch
- [18.10.2011] replace broken disk drive on sun2
- [16.12.2011] install permanent replacement for broken Linksys switches
- [20.04.2012] reconfiguration of sun2
- [24.04.2012] install OpenSSL security update on signer
- [08.05.2012] install another OpenSSL security update on signer,
- install USB-serial power switch for infra01 backup drive
- [28.05.2012] investigate and fix broken signer service (disk problem)
- [22.06.2012] investigate and fix broken signer service (disk problem)
- [26.06.2012] repair signing server (disk replacement)
 The total number of visits (9) was considerably larger again than in the previous year (5), and 5 of these 9 visits could be labelled emergency visits, correlating closely with a number of hardware problems.
The total number of visits (9) was considerably larger again than in the previous year (5), and 5 of these 9 visits could be labelled emergency visits, correlating closely with a number of hardware problems.
Unfortunately, after the visit of 22.06.2012, a piece of paper containing a subset of the critical secrets kept by CAcert critical system admins has been left unattened in the server room for a couple of days. This made it necessary to change all the affected passwords and encryption keys, which was done on 26.06.2012. Our subsequent investigation has revealed that no actual compromise has occurred due to this incident. Howver, the final word about this is still under arbitration (case http://wiki.cacert.org/Arbitrations/a20120626.1 ).
Off-site activity
All other (i.e. most!) system administration work has been performed remotely. Issues directly affecting the operation of the webdb server continue to be logged to the cacert-systemlog@lists.cacert.org mailing list (archived at https://lists.cacert.org/wws/arc/cacert-systemlog ) with headings like "configuration change webdb server", "security upgrades webdb server" or "cvs.cacert.org checkin notification". This logging is also used for changes to all other services like DNS, OCSP etc. under critical-admin management.
Webdb server
The software upgrade of the webdb server from the no longer supported Debian "Etch" release to the Debian "Lenny" (oldstable) was completed by propagating the upgrade to the chroot environment in which the web server runs. Other maintenance work on the webdb server during the reporting period involved:
- 27 installations of one or more Debian security updates
- 12 configuration changes
- 2 package set install/purge operations
- 1 database upgrade
- 60 application software patch installations
thus making a total of 102 critical admin interventions for this server.
DNS service
The DNS service has been continued in the same configuration as the previous year. Maintenance activities for this server boiled down to:
- 6 DNS software version updates
- 1 configuration change
- 6 installations of one or more OpenSuSE security updates
- 1 Key Signing Key rollover (for each of 3 zones)
- 16 zone file changes
thus making a total of 30 critical admin interventions for this server.
OCSP and CRL service
The OCSP service and CRL services have also been continued in the same configuration as the previous year. Maintenance activities for these services boiled down to:
- 2 OCSP software changes
- 5 configuration changes
- 6 installations of one or more OpenSuSE security updates
thus making a total of 13 critical admin interventions for this server.
A plan to improve the availability of the OCSP service by replicating it on a (virtual) server provided by HCC/Hobbynet was killed unfortunately due to incompatibility of our security requirements.
Backup service
The boxbackup server has also been continued unchanged, with maintenance activities limited to installing a number of OS updates:
- 7 installations of one ore more Debian security updates
thus making a total of 7 critical admin interventions for this server.
Infrastructure support
The migration of all (non-critical) infrastructure services to infra01 (formerly known as sun1) as the new infrastructure server was finally completed in March/April 2012 thanks to some tremendous efforts of Mario Lipinski. The critical admin team supported this operation, and has ensured that the new infrastructure server is now able to reliably access its external USB backup drive. The old infrastructure server (sun2) is now available for use as a critical server, and preparation for its use as the new webdb server has been started.
Software Assessment Team support
We continued to support the Software Assessment Team by maintaining a test server (on a virtual machine) which looks as closely as possible to the production webdb server. A second similar test server is also maintained for special critical system tests and preparation of major software upgrades.
The patch process developed by the Software Assessment Team has resulted in a large number of successful patch updates to the production server (60 during the past year!).
Events team support
Feom time to time the events team wants to inform CAcert members about important events like Assurer Training Events and the like. These mailings are performed by adding a custom script to the webdb server and running it against the current database. Based on arbitration http://wiki.cacert.org/Arbitrations/a20090525.1, such scripts are prepared by the events team and handed over to the critical admin team for installation and execution. 11 cases were handled in the past year.
Team changes
After losing Stefan Kooman as member of the critical sysadmin team last year, we have been looking for a replacement. We were lucky to find Martin Simons as a suitable candidate in March 2012, but unfortunately, the ABC required in the enrollment process has taken a long time to complete. It completed finally on November 1, 2012 (well beyond the end of the reporting period), but at least we know now that we'll have a 3-person team again.
Plans
Plans for the coming year include:
- integrate Martin Simons into the sysadmin team
- upgrade webdb server to Debian Squeeze *and* better hardware (sun2)
- deploy improved database backup procedures
- prepare system software upgrades (Debian Squeeze, OpenSuSE 12.2)
- improve system monitoring
- expand and improve server documentation
- look into replication of OCSP and CRL services on external servers
- look for expansion of the sysadmin team
Wytze van der Raay, Mendel Mobach
Education Team Report
Management of CATS and the Assurer Challenge
 During the last year the french User Interface translation has been finished and reviewed and should be installed until the AGM. Dutch is almost ready to deploy Spanish translation has been finished but still needs a review.
During the last year the french User Interface translation has been finished and reviewed and should be installed until the AGM. Dutch is almost ready to deploy Spanish translation has been finished but still needs a review.
Translation of the tests made less progress. Only the french Org Assurer Test is ready to review, no significant progress on the other languages.
The Org Assurer Test has been initiated as a new test, but still is not ready to deploy.
The CATS system has turned out quite stable during the last year. There's one minor bug still reported in the bugtracker, though there are lots of extension requests (mostly by myself).
The development system for CATS has been moved from the old location at cacert.at to https://cats1.it-sls.de/.
During 2011 (numbers only available per calendar year), 114 PDF certificates and 19 printed certificates for passed Assurer Challenges have been issued.
Since the beginning of 2012 it is not possible any more to find out if an account has already 100 Assurance Points by using the standard "Assure Someone" interface, so the process of creating a certificate has become a bit more complicated. Support has to be asked to confirm that 100 Assurance Points have already been reached for an account.
Some statistics for the time July 2011 to June 2012:
- 2403 test have been made, 1216 english Assurer Challenges, 1087 german ones and 99 Triage Challenges
- 1219 of the Assurer Challenges has at least 80% correct answers and are therefor counted as passed
- 872 different users (that is, different certificates used to login) have passed the test at least once
- 174 users tried the test at least once but don't have a successful test recorded
- On the average those who passed the test had about one (more exactly: 0.91, compared to last year's 0.94) unseccessful tries before passing.
Supporting ATEs
No requests to support ATEs have been received during the last year. ![]()
Prospects for the next year
The same as last year:
- Finish the started translations of CATS test and user interface.
- Extend and update the pool of questions for the Assurer Challenge, especially in the area of Arbitration
- Support Event Organisation in improving and extending the present materials for ATEs (see SVN)
- Improve the CATS admin interface so editing questions and answers is a bit more comfortable.
- Improve the CATS database structure and admin interface to give better support for handling questionaires in different languages
Events Team Report 2011-2012
Assurance and Training Events Statistics
Year
Months
Count
ATEs
did not happen
ATEs not happened
Reports rcvd
2012
01-06
16 (+1)
6 (-1)
0
1
6 (-2)
2011
07-12
16 (-5)
0 (-5)
2
0
1 (-7)
Total
2011-2012
32 (-4)
6 (-6)
2
1
7 (-9)
- 2012: in total 32 (36 in last year) registered Events takes place with 7 Event reports received (22% (-22%)).
2011
Year
Months
Count
ATEs
did not happen
ATEs not happened
Reports rcvd
2011
01-06
15 (-5)
7 (+6)
1
2
8 (+4)
2010
07-12
21 (-11)
5 (+2)
3 (?)
0
8 (+2)
Total
2010-2011
36 (-16)
12 (+8)
4
2
16 (+6)
- 2011: in total 36 Assurance Events takes place with 16 Event reports received (44%).
2010
Year
Months
Count
ATEs
did not happen
ATEs not happened
Reports rcvd
2010
01-06
20
1
0
0
4
2009
07-12
32
3
7
1
6
Total
2009-2010
52
4
7
1
10
- 2010: in total 45 Assurance Events takes place with 10 Event reports received (20-25%).
Assurance Events by Countries
Country
2012
2011
2011
2010
2010
2009
DE
9
8
6
15
12
20
ES
1
2
2
NL
2
2
2
2
5
US
1
3
1
2
1
AU
1
1
2
1
BE
1
1
1
AT
1
1
UK
1
1
CZ
1
1
FR
1
1
SE
1
1
CA
1
CH
1
1
2
DK
1
JP
1
Total
15
15
15
21
20
32
Events scripted mailing
 With the Arbitration precedents case a20090525.1 "Event officer request recurrent notification to assurers near the location of the following ATEs" a scripted maiiling procedure has been implemented back in spring 2009 that assists Event Organizers to contact Assurers near their location. This scripted mailing has been used several times:
With the Arbitration precedents case a20090525.1 "Event officer request recurrent notification to assurers near the location of the following ATEs" a scripted maiiling procedure has been implemented back in spring 2009 that assists Event Organizers to contact Assurers near their location. This scripted mailing has been used several times:
- 2012 1st half: 6 mailings sent to 7183 recipients (2011: 8, 2010: 4)
- 2011 2nd half: 1 mailing sent to 1254 recipients (2010: 8, 2009: 6)
for event organizing or for event announcement.
A total of 7 mailings with 8437 recipients (approx 1205 recipients per mailing) within the last period.
The overall result was a success as Event Organizers found assistance by Assurers or people comes to the Events.
ATE / co-Audit Team Report 2011-2012
Two events did effect the ATE and Co-Audit team.
- The mass mailing notification script to all our members about "Changes at CAcert: New Points Counting" and "Tverify points to be deprecated"
The Baseline Requirements Draft 5.0 that signals a *significant impact* to CAcert and therefor CAcert's path to an Audit.
 The first results in a couple of requests for an ATE from United Kingdom, United States of America, Sweden and Australia. So at the end one ATE in the UK, and 4 ATEs in Germany did happen. The ATE in Australia at linux.conf.au ballarat has been downgraded to a regular assurance event with some ATE slides with a view to find new AU CAcert Inc members.
The first results in a couple of requests for an ATE from United Kingdom, United States of America, Sweden and Australia. So at the end one ATE in the UK, and 4 ATEs in Germany did happen. The ATE in Australia at linux.conf.au ballarat has been downgraded to a regular assurance event with some ATE slides with a view to find new AU CAcert Inc members.
The 2nd slowed down the activities in ATE and Co-Audit area. ATE's requested where it was easily to arrange and man with co-auditors did happen.
The running machine to collect co-audit results is currently unavailable. Co-audited assurances results are backed up.
Prospective View
Moving forward depends on a new vision, that CAcert will move forward with an internal audit or other decisions. Also some work is required to do to bring the Co-audit results machine back online. So here the question goes to sysadmins of non-critical infrastructure to assist in this area.
To form a new vision and get it finalized is a common task to all community members.
PR Team Report 2011-2012
 We have had the following bigger articles in the german freeX (IT professional) magazine:
We have had the following bigger articles in the german freeX (IT professional) magazine:
2011-04 freeX Edition 2/2011 - Topic: Certificates and their field of application (see also: http://blog.cacert.org/2011/04/508.html)
- 2012-08 freeX Edition 4/2012 - Topic: Handling and safety of digital certificates vs. De-Mail (german's new secure e-mail system) and ePostbrief (a similar relatively new system in Germany)
2012-03 We have created a press release for the Organisation Assurance of a regional branch of the german Pirate Party.
Not directly connected to Public Relations, yet performed mostly by Head of PR team between last quarter 2011 and mid-of-second quarter 2012:
Application of CAcert for a free booth at CeBIT 2012
Application, Planning and Organisation for CAcert at Chemnitzer Linux-Tage
Application, Planning, Organisation and event presentation for CAcert at LinuxTag Berlin.
The care for events has been so big that it is not advisable to do it in the same depth in the future. Also it is not the main focus of a "PR" team. Instead more time could be invested to initiate connections to other people and organizations. This was started in the desired way in October 2012 at T-Dose 2012 in the Netherlands.
For many events we have written quite a number of blog posts on blog.cacert.org, as well as on XING, LinkedIn and on our new site on Google+ which is followed by quite some people now. Several events, and especially ATEs were also announced on our Twitter account CAcert_ATE. Someone else holds a Twitter account named CAcert. We would still need to figure out who is he and hopefully to gain control over this account, too.
There are also external blogs who are willing to spread informations on some CAcert news. We have found supporters who are willing to translate our news to british, spanish and italian. Still, these connections have to be made stronger and stable, and we are still looking for further supporters who are willing to translate our news into their native languages. For 2013, we're also looking on how to celebrate CAcert's 10 years' market presence.
Alexander Bahlo
Assurance Team Report 2011-2012
Events effecting Assurance Area - Overview
Date(s)
Event, Description
Scripted
mailing2011-07-11 - 2011-07-14
Booth and assurance event at RMLL Strasbourg, FR
2011-07-24
Arbitration precedent case: a20110608.1 Scripted Mailing in OA area
2011-08-10 - 2011-08-14
Assurance event at CCC-Camp, near Berlin, DE
2011-08-16
Assurance event: Locales de CNT, Madrid, ES
2011-08-20 & 2011-08-21
Booth, Presentations at FrOSCon, St. Augustin, DE
2011-09-17
Booth, Assurance event: SFD Hamburg, DE
2011-10-14
Assurance events: Medialab Prado, Madrid, ES
2011-10-20
Assurance events at NLUUG Fall Conference, Ede, NL
2011-10-26 - 2011-10-28
Assurance events at Linuxcon Europe, Prague, CZ
2011-11-05
Booth, Assurance event at BLIT, Potsdam, DE
+
2011-11-04
Booth, Assurance event at Open-Xchange Partner Summit, Köln, DE
2011-11-05 & 2011-11-06
Booth, Assurance event at T-Dose, Eindhoven, NL
2011-11-12 & 2011-11-13
Booth, Assurance event at Open-Rhein-Ruhr, Oberhausen, DE
2011-11-16
Baseline Requirements Draft 50 (CABforum (BR)) has been published
2011-11-27 - 2011-11-30
Proposed New Points Counting, Tverify points to depricate project, Mass Mailing to Members
+++
2011-12-15
Signing Party and Assurance event, Stockholm, SE
2011-12-27 - 2011-12-30
Booth, Assurance event, Presentation at 28c3, Berlin, DE
2012-01-06
Arbitration precedent case: a20111128.3 Delete my Account, CCA-termination
2012-01-13 - 2012-01-15
Booth, Assurance event, FUDCon Blacksburg, VA, USA
+
2012-01-14
ATE-Manchester, UK
+
2012-01-16 - 2012-01-20
Assurance event, linux.conf.au ballarat, AU
2012-01-25
Assurance event, Vienna, AT
2012-02-04 & 2012-02-05
Booth, Assurance event, Presentation, at FOSDEM, Bruexelles, BE
2012-02-14
ATE-Hamburg, DE
+
2012-02-25 & 2012-02-26
Assurance event, Presentation at Drupal Camp, Essen, DE
2012-03-06 - 2012-03-11
Booth (day 5), Assurance event, Presentation, CeBIT, Hannover, DE
2012-03-17 & 2012-03-18
Booth, Assurance event at Chemnitzer Linuxtage, Chemnitz, DE
2012-03-26
Assurance event at Clarinux, Madrid, ES
2012-03-29
ATE-Jena, DE
+
2012-04-10
ATE-Leipzig, DE
+
2012-05-15
ATE-Karlsruhe, DE
+
2012-05-18 - 2012-05-20
Assurance event, SIGINT, Köln, DE
2012-05-23 - 2012-05-26
Booth, Assurance event, Presentation at LinuxTag, Berlin, DE
Event Reports and Audit over Assurance
 Our last Auditor instructs Events and Assurance Officer to request delivery of Events reports of each Assurance event with a statement by the Events organizer with at least two basic informations:
Our last Auditor instructs Events and Assurance Officer to request delivery of Events reports of each Assurance event with a statement by the Events organizer with at least two basic informations:
- How many Assurances were made?
- Were all assurances given conducted by Assurance Policy?
The instructions given by the last Auditor back in 2009 relates to Audit and Co-audit. Without delivered event reports the audit over assurance becomes difficult and expensive. The last auditor prepared the framework to cover the Audit over Assurance area. But this only works if all event organizers will send their event reports to the Events team and Assurance Officer.
The statistics from Events team signals a heavy decrease in delivered event reports. That is no good signal in moving forward with Audit over Assurance plans.
With a statement delivered by the Event organizers, that all assurances made were conducted following Assurance Policy, Audit area receives an evidence that Assurances given followed Policy. Without received Event reports -> no evidence, so this becomes a potential Audit fail!
To the Community and Event-Organizers
The request When comes the roots into the browsers? requires a passed Audit.
Audit requires evidence that Policies has been followed.
This requires that Event Organizers delivers Event reports.
So its all up to you, that an Audit will pass or will fail
Supporting ATE processes
Board continued supporting ATE processes
- (from the Board report)
- Board continued supporting ATE processes
in AU by Iang for the purposes of boosting the Australian Membership by motion m20110717.6
In Manchester by Alexander Bahlo and Ulrich Schroeter by motion m20111220.3
https://lists.cacert.org/wws/arc/cacert-board/2010-12/msg00031.html Events report ATE-Melbourne gives some hint about expenses, that are required to travel along AU.
ATE Manchester
The ATE Manchester/Crewe events report can probably seen as a precedent for expenses paid that comes outside an ATE event along Europe with traveling fees, accomodation costs and other expenses, that a potential Auditor will add to a bill (once audit plans will move forward).
Current agreement is, that both Board and the Community have to pay ATE expenses to move forward with the internal audit. So Board support is a partly support. This to keep in mind for future plans to drive an ATE within Europe.
Regional Supporters
Another option is that a local or regional supporter who supports CAcert ATEs in their country like Secure-U did for ATE-Munich (2011-04-02)
But also here, support by the local Community is required. eg. the local Community in a country spends money to the local incorporation and the local incorporation can support CAcert projects.
For the Netherlands, the local supporter is Oophaga. In Austria its Sonance and in Germany its Secure-U
Baseline Requirements Draft 50 - CABforum (BR)
In autumn 2011 the Assurance team discussed the Audit state, that
Assurance area is probably Audit ready
In November 2011 then, the Baseline Requirements Draft 50 of CABforum (BR) has been published.
So pride did come close before fall.
In policy group much discussions started. Within the co-audit team the vision of an internal audit did survive. So also in 2012 ATE's did happen. But this also shows, that a public visible vision is needed to move forward either way.
Tverify points to depricate project
The Tverify points to depricate project that started back in 2009 with two board motions, has been picked up by the Software-Assessment project team based on ideas by dirk of a new points counting schema (more in next section).
The project moved forward, so by end of 2011, an announcement has been made to the Community that the day of Tverify points removal comes closer.
For Assurance area the Tverify program has been stopped by end of 2009 but the Tverify Assurance points still counts. Software-Assessment now comes to ground to pass the required software-patches (after first establish a working software-update procedure to the critical system) to incorporate the changes that are needed according to policies.
The special assurance program Tverify has been stopped by audit purposes as we have no evidences over these assurances. So therefor the call to all ex-Thawte assurers has been pushed out since 2009 - bring your account in compliance with AP. So to get assured and to give assurances under AP.
Proposed New Points Counting Schema
Assurance Policy's definition is:
- - that you can assure someone only once
- - that countable assurance points is limited to 100 Assurance points
Back in 2009 dirk comes along with the idea, that only the last entered assurance points will count by turning the points count order.
- Currently the software counts assurance points at the moment, someone enters an assurance to the online form into a static table.
pros
system performance, calculation is made once at time of transfer the assurance to the online form
cons
updates (revocations) needs to be processed manualy by remoke a couple of assurance to reenter the assurance to the system, so the assurance points count becomes repaired
the Tverify points revocation needs to be made by hard removing points from the users records (not auditable)
- The new idea is, to calculate points whenever the points count is needed. Eg. by entering an assurance, by revoking assurances.
pros
update process is easy, easy revocation of assurances and points count will be repaired automaticly
the annoying "you've issued 35 points, rounded down to 0" drops, less questions by newbies
all points counts!
with the newly introduced advanced assurance procedures
a. Password reset w/ Assurance
b. Name change request w/ Assurance
it may become a requirement, that an assurer who assured someone before needs to assure the user again.
Stop thinking!
AP definition says, that you can only assure someone once. Correct. This means, that the points counting only counts once. So an assurer who can give 35 APs cannot assure one assuree 3 times to reach 100 assurance points.
All what is required to fulfill this requirement is that in a re-assurance, the old counting points are no longer counts by hiding them or round them down to 0
x1)Tverify revocation will be made by no longer count the Tverify transfered points. The points are still in the database (no database modification) but will no longer be counted by new calculation
- x1)
Example: Living in an area with small counts of assurers someone changes his name, and requests a re-assurance Why can the assurer cannot re-assure someone? This sometimes happens by Assurers who have assured many members on big events and coming to another big event and assuring someone again. - The assurer gots more experience in the meanwhile, so a re-assurance will help CAcert to get a strong WoT - A reassurance probably covers newer and better Id documents with more security features. - advanced assurers procedures (Password reset/Name change) can be covered with a re-assurance allowed rule but only one assurance counts - the better, the latest assurance counts
cons
system performance will probably increase as more calculations of assurance points needs to be made in total. every access to your points counting level will produce a re-calculation (but there aren't that much points in the software that requires the exact points count, so to be recalculated)
Tverify points to depricate
As Software-Assessment makes progress, the day of the final cut of Tverify points comes closer and closer. Currently software developers and software testers prepares the software for the second step.
The first step has been made by end of 2011 by introducing the New Points counting schema. That is available though your accounts - my details - my points - new points counting page Under this page you receive a sneak preview how your points will be counted once step 2 of the project has finished. If this page lists, that you fall below a certain level (eg below 50 assurance points, below 100 assurance points, below 50 experience points, you should be warned to bring your points count up in a good working order by receiving and giving assurances.
The prospective view is, that step 2 will become active in spring or summer 2013
Scripted and Mass Mailing to Members
The Tverify points to depricate project also results in a subproject to inform our members regarding new points counting schema and also that Tverify points will expire soon.
Mass Mailings to Members
Based on the scripted mailings introduced by the Events Officer back in 2009 and precedent ruled under arbitration, the script to mass mail around 200.000 recipients has been slightly modified and the script has been executed between 2012-11-27 and 2012-11-30. So this was also a test run for the CCA rollout program still in the pipeline to process for audit reasons.
With a 3 days run, the practice has shown that it is possible to run such a mass mailing to all members through scripted mailing, but it should be prevented to a minimum of events if there is no other option possible to get all members informed.
So this also affects Assurance area, as we cannot use this path on a regular basis (eg weekly newsletters, weekly updates)
Scripted Mailing in OA area
Similar to the scripted mailing for events to inform members in a certain area about events, OA area has got their own scripted mailing procedure ruled by precedent under arbitration.
So now, OAO is able to start a process to inform Organisations about OA specific topics.
CCA Termination
One topic that also covers Assurance area are member request for CCA termination. As long no assurances has been given terminations of members do not effect the WoT. But if one member who wants to terminate has given assurances, the Assurance paperwork needs a safe storage or the members acceptance over the remaining 7 years to answer arbitration request. This means, the user is still bound to the Risks/Liabilities/Obligations of the CCA.
Procedures under Arbitration have been established, to return the CAP forms of members who wants to terminate to the Arbitrator processing the case. So WoT is secured.
So a precedent ruling under Arbitration has passed that covers all such simple cases, where members didn't gave an assurance.
Other Assurance Programs/Assurance Subpolicies
PoJAM and TTP-assisted-assurance subpolicy has passed Policy group in 2010.
PoJAM
With the Policy on Junior Assurers/Members we now have some experience for a while. It is subject of the ATE presentations, so therefor known to the active assurers who still have attended an ATE. We currently have no counts how many Assurees and Assurers falling under this rule (below 18). An Adhoc query has been started before the subpolicy passed policy group.
The result has been published 2009-12-23 in policy group mailing list.
- (all counts references back to current date Dec 2009)
- Description: counts total, unique assured users (count base)
- 22193
- How many assured members at present are below 18 years of age.
- 119
- How many members have been below age of 18 at the time of their first assurance.
- 427
- How many assurers are or have been below age of 18 years.
- 40
However, Software had not been updated to reflect PoJAM cases as its required by the subpolicy.
So current practice is to add a note under the locations field
+PoJAM
for a PoJAM case -and- a handwritten note on the CAP from:
Parental consent established
- signed by one parent -or-
- signed by the assurer with his CARS statement
TTP-assisted-assurance
Since all special assurance programs were frozen since at least 2009 the deployment of policies and procedures started end of 2009 and hasn't yet been finished. One of these special assurance programs is the TTP-assisted-assurance program.
The TTP-assisted-assurance subpolicy passed policy group in 2010. The TTP subpolicy defines 2 TTP assisted assurances and an addtl. TOPUP assurance. Until today, the latter hasn't been deployed and implemented in a sufficient way into the software, so it cannot be passed currently.
Discussions within the TTP deployment team, comes to the conclusion to no longer wait to get the TTP-assisted-assurance subpolicy requirements implemented into the software. This states, that TTP assurances to be defined as TTP assurances into the system and the TOPUP assurance to be defined as a TOPUP assurance in the online system. By default, current available assurance method by Polciy is limited to Face-to-Face assurance only.
To move forward with the TTP-assisted-assurance program, we've decided to reuse the old "TTP" assurance method in the online system so we can start deploying the new TTP program for the first countries USA and AU where we have some background infos about TTP's
Then a software bug with the old assurance method "TTP" blocks moving forward with the reuse of the old assurance method "TTP". This software bug should have been fixed by now, but awaits a verification by software testers with a current software revision state as our production system (testserver has also other fixes installed, that may interfere with this bugfix)
The permissions review project that has been started this year by Board disclosed the current state of the old special assurance programs flags and accounts with permissions to do so. All permission flags now have been reset.
So the next step will become to process the nominations by Board for the first 4 TTP assurers into the production system and further deployment of the TTP-assisted-assurance processes. Documentation have been made in the wiki by now under the topic TTP.
Deployment of TTP specific CAP forms moved forward but currently automatic processing is impossible caused by missing Software implementation. This is also the reason why TTP CAP forms aren't available to the public.
Overall state: work-in-progress
Nucleus
Back in 2009 an alternate to the Super-Assurers program has been introduced, named Nucleus. Until today, no one picked up these ideas to transfer it into a assurance subpolicy.
The ideas are similar to the TTP-assisted-assurance subpolicy, to add missing points between 70 and 100 to an account (TOPUP under TTP-assisted-assurance), to pass the requirements upto 100 assurance points for becoming an assurer.
With two experienced assurers who can spread the CAcert Assurance philosophy to CAcert desert areas, the Nucleus program can be a starter to build up local communities also in current CAcert desert areas.
But first requirement is a written subpolicy. This task needs to be picked up by the Community in policy group.
Legacy Policy
The Legacy Policy is a yet unwritten policy too. It shall give an answer to the question what to do with old assurance points given by old assurance programs.
- Tverify
- old TTP program
- Super-Assurers
With the new CABforum (baseline requirements), there is another source of requirements that needs to be answered.
So this topic is still on the ToDo list for policy group.
Organisation Assurance Report
 Statistics by 2012-06-30
Statistics by 2012-06-30
Country |
Total |
Jul 2010 to |
Jul 2011 to |
Since |
AT |
18 |
2 |
|
|
AU |
9 |
|
|
|
Be |
3 |
|
1 |
|
CA |
1 |
|
|
|
CH |
19 |
1 |
1 |
|
DE |
134 |
7 |
17 |
5 |
DK |
1 |
|
|
|
FR |
7 |
|
1 |
|
GB |
1 |
|
|
|
HU |
5 |
|
|
|
IE |
3 |
|
|
|
IN |
1 |
|
|
|
IT |
2 |
1 |
1 |
|
LU |
3 |
|
1 |
|
NE |
1 |
|
|
|
NL |
22 |
1 |
|
|
PL |
1 |
|
|
|
RO |
1 |
|
|
|
SE |
3 |
|
|
|
UK |
2 |
|
1 |
|
US |
30 |
|
|
|
ZA |
1 |
|
|
|
Grand Total |
268 |
12 |
21 |
7 |
During the last fiscal year quite a few Organisation Assurer could be trained. Alexander Bahlo and Marc-Oliver Hofmann were nominated as Orgnaisation Assurer. 4 more were nominated after the end of the fisal year.
Together with the software team a few bug fixes could be installed to improve the usability of the software for the organisation section. There is still a lot to do but we are moving in the right direction.
Marcus Mängel
Support Team
 In August 2011 there was a support team meeting at the FrOSCon 2011 where most team member were able to attend. We decided to move the team leadership from Micheal to Joost.
In August 2011 there was a support team meeting at the FrOSCon 2011 where most team member were able to attend. We decided to move the team leadership from Micheal to Joost.
In autumn 2011 Werner could be reactivated as Support Engineer and he is doing a good job since than.
Marek was trained as new support member and he was nominated as Support Engineer in June 2012.
Over the year support was able to handle 848 tickets, for details see statistcs below. Together with Arbitration a few new precedent cases could be developed an put into place, so that not erverything needs to go to Arbitration any more. eg. name change after marriage. The statiscs shows the tickets that handle special cases inside support.
 Statisics of Support tickets
Statisics of Support tickets
Topic |
Number |
Account delete prescedent case |
59 |
Code signing requests |
46 |
Name change with assurance |
6 |
Name change with precedent case |
21 |
New point calculation |
18 |
Password reset with assurance |
30 |
Passwort reset old style |
65 |
Revoke assurance |
17 |
Support tickets total |
848 |
Joost Steijlen, Marcus Mängel, Werner Dworak

Birdshack Team
 Michael posted Requirements taken from his thesis, entitled “The Influence of the Architectural Style on Security, Using the Example of a Certification Authority”
Michael posted Requirements taken from his thesis, entitled “The Influence of the Architectural Style on Security, Using the Example of a Certification Authority”
Iang led a development effort starting in May of 2012 through to September 2012 to produce a basic template.
Internship involved one student Marie Louise Nesfield building a set of transporting objects, with associated self-test system. Supported by forthcoming article and a presentation at BarCampMelbourne.
- Iang revamped an object database so as to perform the CRUD/REST mission with most facility.
- Progress continues...
Internship
In May of 2012, student intern Marie Louise Nesfield joined us for a (northern) summer of coding. This took place in Australia under the direct supervision of Iang, with Piers Lauder and Kevin Dawson appointed as advisory and guardians of the coffee review.
Marie Louise had yet to do her first serious university-level course (which became Computing 401 at UNC-NC), so she entered at a very junior level. Iang tasked her to write classes to transfer data back and forth between client and server within the overall CRUD and REST client-server design for a new secure Certification Authority server. This Birdshack project had been started 2 years previously in Austria.
This tasking came with a couple of further quirks, being a unique unit-testing pattern developed in prior work, and a set of request/response classes that handled the CRUD pattern within a prior security framework. The set of classes was completed by Marie Louise to a major extent, and came with the self-testing inherent in the pattern, as well as test harnesses that successively entered higher and deeper into the business semantics of CRUD.
The overall tasking was quite challenging for the level of experience, and was only just completed in the last few days! The deliverable consisted of:
Type of Component |
Java Classes |
pure BirdShack API |
AccountHolder Domain Name Rid Assurance Email Profile SDF Controller Member Resource |
Resource |
AbstractResource AbstractResource AssurancePointsResource AssuranceResource DomainResource EmailResource ExperiancePointsResource MemberResource NameResource ProfileResource PromiscuousResource SDFResource TestResource ResourceId |
util |
|
Request/Response Model |
CRUDRequest CRUDReply CreateRequest CreateReply ReadRequest ReadReply UpdateRequest UpdateReply DeleteRequest DeleteReply |
Transactional support |
TransRequest TransReply PromiscuousResource Promiscuous |
testing |
AbstractTestClient TestClient TestClient2 TestClient3 TestClient4 TestClient5 ClientTest |
During the internship, additional focus was put on the curricula for Computing 401 and some additional concepts relevant to the project.
Measurands |
Qty |
source files: |
49 |
hard core code lines, not comments nor { }: |
4021 |
lines including useful comments: |
5865 |
In addition to coding work, Marie Louise participated in other joint activities. Firstly, she co-authored a paper on the above-mentioned technique, which came to be known as the Ouroboros Pattern. Secondly, she presented that technique at BarCampMelbourne, in an impromptu 30 minutes spot. Finally, Marie Louise participated as an Assurer at BarCampMelbourne, making her third so far.
Iang
Affiliate Programme
 In December 2011 we started an affiliate programme with booking.com.
In December 2011 we started an affiliate programme with booking.com.
For each booking that is made over the CAcert relate link at booking.com CAcert gets part of the provision that booking.com gets from the hotels.
Until June 2012 we had 21 bookings with a total of 59.53 EUR that CAcert get. In the following quarter we got 22 bookings with 90.79 EUR fees.
The first share of 115 EUR has been paid in November.
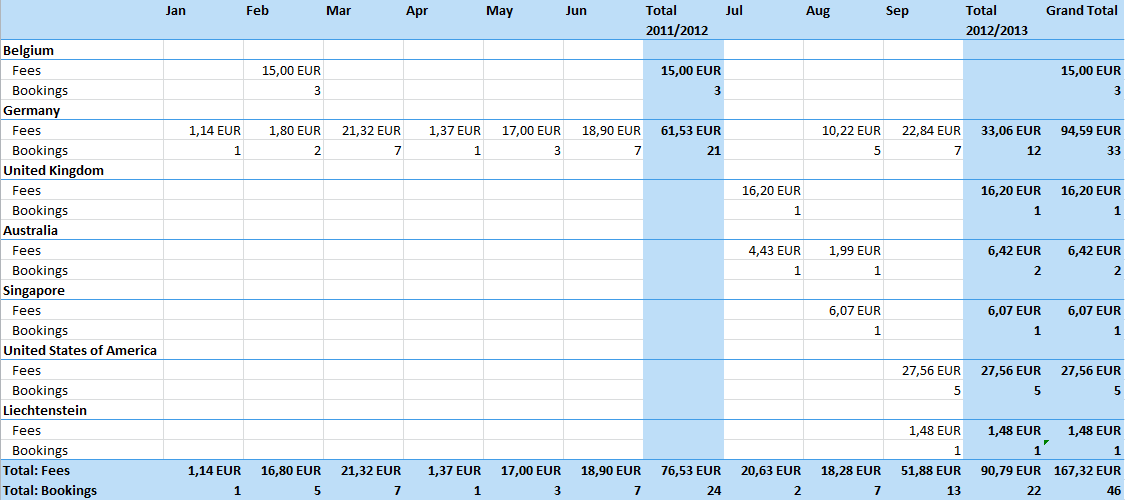
Table: Development of bookings per country where the hotel was used
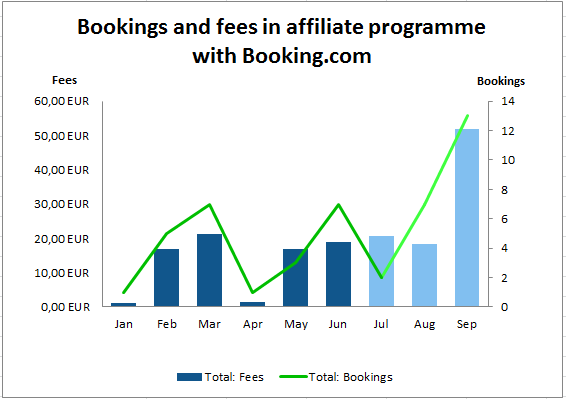
Chart: Development of bookings per month
The bookings came from Australia, Germany, Netherlands and USA.
So I hope many of the Inc and Community Member will support CAcert by using this affilate programme with booking.com.
Marcus Mängel
Board