To AGM - To AGM/Next - To AGM TeamReports Overview - To AGM Members Reports Overview
Team Reports 2011
Team Leaders are encouraged to present a report for their team.
1.
{g}
2.
{g}
3.
{g}
4.
{g}
5.
{g}
6.
{g}
7.
{g}
8.
{g}
9.
{g}
10.
{g}
11.
{g}
12.
{g}
13.
{r} missing
Policy Group's Year of Conquest!
Links:
Significant Events
p20100710 License root under Root Distribution License
p20100722 License our Policies under CC-BY-SA-3.0-AU
p20100913 TTP Assisted Assurance Subpolicy
p20110108 DRP #3.4 Appeal handled by Arbitrators
p20101009 Changes to CCA for RDL
- has been not voted for with a summary, that CCA needs further updates
- Two tries have been given to walk thru the policy and to update paragraphs.
- This process has not finished yet.
Future Work - Stuff we'll predict we'll do next year
- Review and vote for:
Root Distribution License to POLICY
TTP Assisted Assurance Subpolicy to POLICY
- Older DRAFT policy that needs review and vote to POLICY
Certification Practice Statement (Draft: p20091108)
Policy on Junior Assrurer/Members (Draft: p20100119)
- Updates
Organisation Assurance Policy (Updates)
- An update has been started but not finished yet.
By lack of a Policy Officer role (currently held by board) nobody seems to be responsible for coordination of Policys management (check policy states, reminder for voting from DRAFT to POLICY, WIP to DRAFT) and to manage a Policy repository migration plan.
Ulrich Schroeter
Audit Team Report 2011
Back in June 2009, the former Auditor leaves the Audit trail, to prepare CAcert's Community to become Audit Ready. The board of 2009 2nd half has redefined the goal:
Ask not when your audit is done;
- rather,
ask how you can do your audit?
Back in January 2010, the board decided a motion with a wider impact: Motion m20100117.3 "No new subroots on current root, plan for new root"
What does this means for CAcert - plan for new root ?
Based on the thoughts over the audit related tasks and projects that needs to be done before CAcert becomes Audit Ready a plan evolved and becomes published also under the requirement to present a prospective Audit view within the ATE presentations back in October 2010 with the blog post The Big Masterplan to become Audit Ready. In the meanwhile the plan has undergone some updates upto the current view:
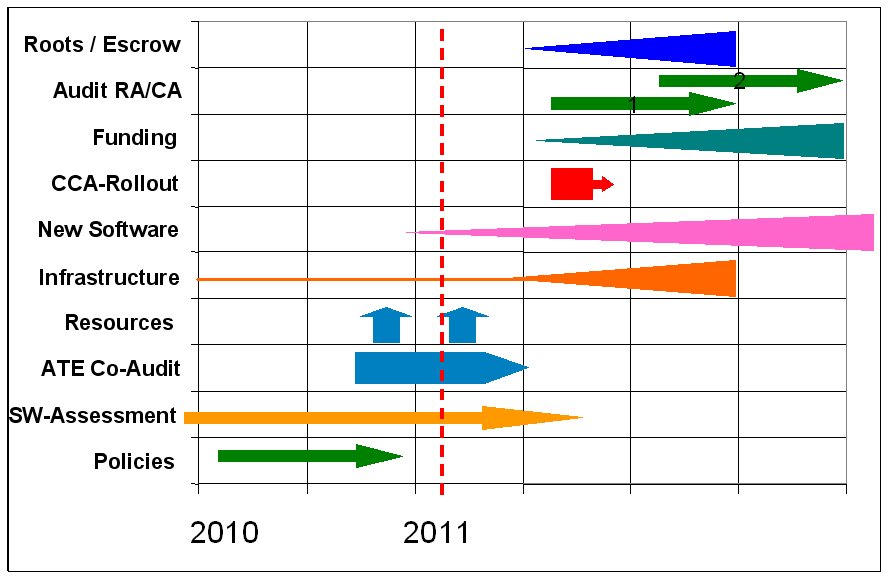
The projects in detail:
Policies
Main policies work has been done by the Policy Group. Some minor work needs to be done like review of Policies in DRAFT state to state POLICY. Also a rework on the CAcert Community Agreement has been started and not yet finished. Another topic is a project within Software-Assessment project team to define and migrate to one single place of Policy Repository.
Software-Assessment
One of the main audit blocking factors is the CCA rollout project. This means, all members needs to be informed about the existence of the CAcert Community Agreement and the members have to accept this agreement.
The preparation is related to the Software-Assessment team, to add some modifications to the critical system, that acceptance to the CCA can be recorded either way. The 2nd topic, that all members can be contacted by a mass mailing.
By end of 2009, we had no working Software-Assessment area that fulfills audit requirements. So this project group has started their work back in December 2009.
 Software-Assessment is related also on a working Software test team. Once the Software-Assessment was build up, had defined a Software update cycle procedure, the software testing becomes more and more a topic to become the software patches tested before it will be applied over the critical system. A Software testteam has been build around August 2010. But activity in this area stalls. So this is a real audit blocker. This has been addressed to board that leads in the May and June 2011 Software Testers Reward Challenge to find more active testers.
Software-Assessment is related also on a working Software test team. Once the Software-Assessment was build up, had defined a Software update cycle procedure, the software testing becomes more and more a topic to become the software patches tested before it will be applied over the critical system. A Software testteam has been build around August 2010. But activity in this area stalls. So this is a real audit blocker. This has been addressed to board that leads in the May and June 2011 Software Testers Reward Challenge to find more active testers.
ATE / Co-Audit
Assurer Training Events (ATE) is the Assurance area answer on the requirement to audit our Assurers regarding Audit over Assurance / Audit over RA (Registration Authority). Together with our former Auditor, the project to audit our Assurers so that it scales the assurers base results in the Co-Audit concept plan. Tested Senior-Assurers to be appointed as Co-auditors doing audits over assurers. The test results to be collected in the Casper system, that can be presented to our future Auditor. Together with the co-audit process to use the ATE concept to distribute an educational assurer training and information events to our assurers base.
The ATE series back in 2009 was the test that the co-audit concept scales over the assurers base. The ATE / co-audit series 2010/2011 that was started in spring 2010 at Cebit 2010 was the real co-audit collection for the Audit over RA. Currently we have about 4% of our Assurers tested. More to test.
From the ATE / co-audit series 2009 results we've expected to also find new resources for helping in the audit related projects and teams eg. Software-Assessment, Software-testteam, Software development BirdShack, Infrastructure sysadmins with experience in system migrations, experts with cryptografic background skills for the New Roots & Escrow project, people who can help on funding. Also people who can help in the existing teams: Support, Arbitration, Critical team. But this didn't worked as expected. In the ATE 2009 series we had mostly experienced- and senior-assurer attendees. In the ATE 2010/2011 we had more and more unexperienced or prospective assurers in our ATEs.
Infrastructure seperation
For the Audit over Systems (Audit over CA) one plan is to split the critical systems from the infrastructure systems, so an audit over the critical system becomes easier and a review over the infrastructure systems does not need to be done. This plan goes back into years 2008/2009, but had not been finished yet.
One of the plans is to move the non-critical systems out of BIT Ede, NL. So in the beginning 2010 the search for hosting providers had a focus. In June 2010 one hosting provider deal died 'caused by other issues. So in the 2nd half of 2010, the plan moves to first seperate the non-critical system from the critical system in the same rack to another hardware, later move the machine to another server room and probably then later to move out the machine from BIT Ede. This project leads on the documentation over systems - critical and non-critical. This has been started in March 2011 and finished in the meanwhile.
New Software / BirdShack
April 2009 review over Software at Software camp Innsbruck presented in the Audit Report 20090426 was:
- A new Software Development team met in Innsbruck last week to review the software and prepare the way forward. Their recommendation: total rewrite.
The result was the New Software project BirdShack.
Since spring 2009 this project did not make much success. There is not much activity in this area. Late 2009, Software-Assessment decided to go a 2-way path, become the current software maintainable and work in parallele on the new software project BirdShack, so audit can pass either way.
No one picked up the task to push the BirdShack project yet. There are some ideas flewing around - eg. starting with software-camps to get developers around to start coding. But all did not happen yet.
CCA Rollout
One of the audit criterias of the written David Ross Criteria, the audit criteria that CAcert has confirmed to, that the CAcert Community Agreement needs to be disclosed to each member and accepted regarding the Riscs, Liablities and Obligations - in short, the R/L/O's needs to be rolled out over the community. Thats in short the CCA rollout.
This project depends on a working Software-Assessment group. The first milestone of this group was reached 2010-07-14 with a running testserver environment and a 2nd milestone reached at beginning October 2010 with a working software update cycle. Since than, several other issues prevents Software-Assessment to move forward with the CCA rollout. So this task is still on the working queue of Software-Assessment.
Funding
For running the New Roots & Escrow project and also to run the new Audit process, funding is needed either way. This has been neglected. Within the last 12 months no activity has been seen in this area. Activities to find people with experience in funding has been made on events and also ATEs but with no success. This topic needs some other channels to be enabled to get this running.
New Roots & Escrow
The last run new roots have been built was back in late 2008. Audit review in spring 2009 revealed a problem with the escrow process so these late 2008 built roots are named audit fail.
So this process has to be done again. But before starting with the create new roots process, CAcert has to work on the roots escrow project:
- select a escrow method that works for CAcert
- check the selected escrow method regaring risc management
The project page lists several potential escrow methods. Back in spring 2010, the escrow discussion was ongoing in the roots mailing list and ended with a presentation to the former board, but this process lacks a completed risc analysis.
Since than, there is some activity in the background, to move forward with this process. Also there are some activities in the Software-Assessment project team after the Class3 re-sign process (later more on this topic) had finished end of June 2011 his work. The topic that is in Software-Assessment project team workqueue is the CRL problem regarding new keys. This project is ongoing. Also the escrow risc analysis project is ongoing. Currently it seems that Software-Assessment project team becomes the working team for the overall New Roots & Escrow project. To coordinate the activities, to move forward with this project.
Audit over RA, Audit over CA
Since Audit has been stopped back in June 2009, there are still activities around to prepare the upcoming audit, but most of these activities are no longer centralized to one person. Tasks are pushed to the teams, to prepare their area to become audit ready.
 Most completion has been reached in the assurance area. Thoughts, if and how a divided audit can work leads to the definition of business areas:
Most completion has been reached in the assurance area. Thoughts, if and how a divided audit can work leads to the definition of business areas:
Audit over Assurance -> Audit over Registration Authority -> Audit over RA
Audit over Systems -> Audit over Certificate Authority -> Audit over CA
This has been prepared by the former Auditor in the Audit until mid of 2009.
The advantage of a divided audit is:
- Audit over RA and Audit over CA is splittable and can be run individual, focus on RA, later focus on CA
- Audit funding for a seperated audit may become easier
- a finished Audit over RA probably can boost an Audit over CA
Audit over RA awaits the CCA rollout (see above), and some software fixes (preparations for CCA rollout). All other requirements for Audit over RA are in a good shape.
CrowdIt
Audit next step is the CrowdIt disclosure system (read AGM - Audit Report 2010 - CrowdIt. CrowdIt, as a sort of wordplay on Crowd-Audit). CrowdIt is an emerging disclosure tool (based on the old DRC browser). This database needs to be filled with reports based on the Audit criterias the so called David Ross Criterias.
This project had been introduced several times, but it still gets no notice from the community as required to move forward with the Audit preparations. This project needs an expert with experience of the Audit terms, who can translate these into practicle reporting steps. So here we did searching for consultancy at the ATEs but didn't found no one as yet.
What has happened to audit in the interim?
Two new risks have to be dealt with in the future.
The affair leading to an SGM in February ??? 2011 created an environment in which a cooperative community-driven audit such as last time is no longer likely. Although the risk of financial misdealings and accusations of same was always present, it was considered to be an acceptable risk given that the audit was an open process and all involved were part of the community. Indeed, the first audit was the primary driver in creating the community based on open governance. As audit always included itself, it was a powerful mitigation for reducing any risk.
Now however we will have to deal with the risk of financial misdealings, and any accusations of same, in the future audit. This likely tips the balance towards requiring a commercial audit with appropriate insurance, and away from a community auditor without any insurance. This has fundings implications.In the last 2 years, CABForum, a group of cooperating CAs, has written a document to standardise basic certificates called Baseline Requirements. This document is proposed to vendors of software as the minimum for all CA-signed certificates. This will likely be accepted by vendors, and will become an additional or replacement set of criteria to which we will have to comply.
Many of the things in the document we already have under control. Some things we lack. By way of example, dditional audits, a high-risk customer monitoring program, HSMs and more are identified as obligatory. These will also have funding and resource implications.
Prospective View
- funding. How much can we allocate an auditor over Assurance? Costs? Brutally cheap -- sleeping on mattresses? Or hotels? Or?
- we need answers to these questions in order to ask -- simply discuss -- options for bringing an auditor in.
Audit is the primary mission of the community. In order to meet the needs of the community, we need answers to these questions. If the attention is not given, or if ambiguous or convenient answers are given to critical questions, then the mission is not served, and big changes will have to be made, including changing the strategic goal away from audit. Time is not an option, and the job has got more difficult over time.
Ian, Ulrich
Infrastructure Team Report 2011
While discussing the Audit related projects, with the new Australien board member Peter Yuill, Peter asks about the audit related Infrastructure seperation task * What are the critical systems? * What are the non-critical systems? From the documentation so far, this question could not be answered.
Peter's question brought the balls rolling to review current systems and infrastructure documentation. This leads to a rework of the systems documentation that had been started by Daniel Black, the former Infrastructure teamleader and now finished by Mario and the team, with assistance by the Critical team with a complete systems definition and documentation, that can be found under the Systems Overview.
 The new infrastructure machine (Infra01) has been setup as LXC host by Jan with input and help from Mario. Jan created implemented Python code (http://svn.cacert.org/CAcert/Sysadm/) to easily setup new LXC containers and to deploy ReStructuredText documentation to MoinMoin wikis.
The new infrastructure machine (Infra01) has been setup as LXC host by Jan with input and help from Mario. Jan created implemented Python code (http://svn.cacert.org/CAcert/Sysadm/) to easily setup new LXC containers and to deploy ReStructuredText documentation to MoinMoin wikis.
 The first LXC container was the Subversion repository machine Svn (http://svn.cacert.org/) that was also upgraded to Debian 6.0 Squeeze and got support for client certificate authentication and SNI. The move of SVN from Sun2 to Infra01 is documented at SystemAdministration/Systems/Svn/Setup and should give an idea for future moves of other instances.
The first LXC container was the Subversion repository machine Svn (http://svn.cacert.org/) that was also upgraded to Debian 6.0 Squeeze and got support for client certificate authentication and SNI. The move of SVN from Sun2 to Infra01 is documented at SystemAdministration/Systems/Svn/Setup and should give an idea for future moves of other instances.
Other containers that are on Infra01 now are Blog (https://blog.cacert.org/), monitor (Nagios) and translations (https://translations.cacert.org).
The other non-critical systems are still on Sun2 and need to be moved to Infra01. The help of the system's administrators is needed to accomplish this task. Some of these non-critical hosts are not upgraded to recent Debian versions yet.
Based on this documentation, the Infrastructure seperation project has been started with the move of non critical systems to a new infrastructure host.
Ulrich Schroeter, jandd
Arbitration Team Report 2010-2011
The year in Arbitration
Arbitration Management Software
 At starting of FY period within Arbitration, the deployment of an Arbitration management system was a topic for several Arbitration team meetings. The introduction of OTRS as the Support's management system was not the favorite as management system for Arbitration. Despite the fact every Arbitrator was encoraged to apply for an OTRS account, only half of the Arbitrators followed the request. This didn't changed until end of the FY period.
At starting of FY period within Arbitration, the deployment of an Arbitration management system was a topic for several Arbitration team meetings. The introduction of OTRS as the Support's management system was not the favorite as management system for Arbitration. Despite the fact every Arbitrator was encoraged to apply for an OTRS account, only half of the Arbitrators followed the request. This didn't changed until end of the FY period.
- split arb filing into a public / private part - private part to be accessible to CM/A's only
In spring 2010 a new arbitration management system was proposed, but did not get finished to a preview state, so Arbitrators decided to use existing tools Wiki, Mailing lists and Email archive for Arbitration work. The wiki system was adjusted with a "private" part for arbitration case files, that can be included in the public files. With about half a year of experience Arbitrators can work on the cases like on a desktop. All informations present, but only those parts public that are considered public.
 The question of reliable storage of arbitration communications was answered with the arbitration-archives mailbox, that has to be cc'd in each Arbitration emailing so each mail is copied to the Arbitration email archive. So if a non-working arbitrator gets replaced by another arbitrator, and an inactive Case Manager gets replaced by a new Case Manager, the complete mailings can be requested from DRO, to open the archive for a specific case.
The question of reliable storage of arbitration communications was answered with the arbitration-archives mailbox, that has to be cc'd in each Arbitration emailing so each mail is copied to the Arbitration email archive. So if a non-working arbitrator gets replaced by another arbitrator, and an inactive Case Manager gets replaced by a new Case Manager, the complete mailings can be requested from DRO, to open the archive for a specific case.
The wiki admins have been pushed for a system migration to client certs only write access. This would give abilities for Arbitration to finegrade the access permissions to arbitration files to arbitration participients. But this project stalls for over one year.
Arbitration Team Meetings
 Regular Arbitration team meetings, that were introduced back in January 2010 still continued over the year until around April 2011. At the end more and more Arbitration team meetings had been defered to the next meeting. The count of attendancies droped from meeting to meeting so in the end only two arbitrators meets together, to adjourn the meeting to the next meeting. The last meeting was scheduled for 2011-05-03 but nobody attended and the recuring meetings droped off.
Regular Arbitration team meetings, that were introduced back in January 2010 still continued over the year until around April 2011. At the end more and more Arbitration team meetings had been defered to the next meeting. The count of attendancies droped from meeting to meeting so in the end only two arbitrators meets together, to adjourn the meeting to the next meeting. The last meeting was scheduled for 2011-05-03 but nobody attended and the recuring meetings droped off.
The Team
One of the topics at the Arbitration team meetings that raised off the agenda again and again was the question:
- How we can encourage new Case Managers and Arbitrators to help in the Arbitration team ?
Arbitration team did many thoughts but still ends in the same conclusion. It lacks resources. Resources of people with enough experience within CAcert. A related definition has been given thru Assurance team. That is the definition for Senior-Asssurer (definition Senior-Assurer in Assurance Handbook). Back in 2009 the run for new Arbitrators was bundled with the ATE series and we found about 8 new Arbitrators. So this was pushed to the Co-Audit team running the ATEs to add the Helping CAcert presentation to the ATE presentation collection with a note we're looking for Case Managers and Arbitrators.
We could not repeat the results in the ATE series of 2010/2011 in the run for new Arbitrators, as the attendencies structure back in 2009 with over 90% of Assurers, familiar with the CAcert structure was not similiar to the attendencies structure in the 2010/2011 ATE series. Many new faces, much more prospective Assurers less "old" experienced Assurers or Senior-Assurers that we expect has enough experience to pickup the task to become Case Managers and Arbitrators. So at the end, we did not get any new Case Manager / Arbitrator candidate to the Arbitration team. One gleam of hope we've received after the ATEs WDC and NY with 2 requests for application.
Another question that araises was about unresponsive arbitrators. At July 2010 we had about 15 Arbitrators on the Arbitratos list. So the first run to remove inactive Arbitrators was started that ends with a removal of 2 Arbitrators from the list of active Arbitrators. One other resigned by himself as of private issues so we now have 12 Arbitrators on the list (see Arbitration statistics table 3). The removal of inactive Arbitrators was backed up by 2 procedures, one defined by the Arbitration team and thru Arbitration "What to do with inactive arbitrators procedures" that was handled under Arbitration case a20091126.2 and by the Board Motion "Provision to remove arbitrators on advice of DRO" motion m20091206.2.
Precedent Cases
With the problem of increasing busy and inactive Arbitrators one answer often heard was:
- Outsourcing of recuring administrative cases to Support
This topic has been taken seriously. Over the year Arbitrators handled cases also under the view to bring the case to precedent so as a result we've at least doubled the precedent cases, where recuring issues can be handled by Support without further action by Arbitration.
The handled cases includes the now well known
- Password Reset Procedure w/ Assurance -and-
- Name Change after Marriage w/ Assurance
procedures, that still gets support by the Assurance area and the Support area.
All other cases has a Name Change issue with small modifications, typo corrections, misleading join form resulting in name mismatch problems, that needs to be handled under Arbitration. Also special chars, UTF-8 incompatibility of our CAcert main website - problems that probably do not occur if the website has been updated to be fully UTF-8 aware to also handle diacritics in names. This needs to be addressed to the Critical team and the Software-Assessment team to prepare a UTF-8 migration plan for the overall critical system.
- A couple of bug# had been added to the overall bugs list, to adjust the join form with field spefic help informations, so the new members joining the CAcert website gets better leaded to enter their names as required (eg. often titles that cannot be found in ID docs are added to one of the name fields) or country specific swaps of Givenname and Surname. With all these minor name changes, the Arbitration list was filled with cases in the past. Now starting 2011 we can see a that the count of new cases drops on name change requests, as many of the recuring cases now can be handled by Support following the precedent rulings.
One name change request case should be named seperately - the hyphen rule precedent case. CAcert is an international organisation and the different handling of hyphens in names in different countries was often the topic for new Arbitration cases. In Germany the local law defines: 2 names combined by a hyphen are considered to be one name (that cannot be split). The common law does not know such a hyphen rule. Its completely unknown. Transfering the German names with hyphens to Common law world systems hyphens in names mostly gets stripped. So the hyphen rule precedent case takes this into account, that CAcert defines his own rule here, to allow names with hyphen to be also handled as there was no hyphen between two names. In summary: the hyphen is either optional in names, no matter from which country the name comes from. So here CAcert has set an international standard.
Precedent cases (with ruled documentation under dispute file) handled in the period 2010-07-01 - 2011-06-30
a20090525.1
Event officer request recurrent notification to assurers near the location of the following ATEs
16
a20100210.2
Revoke my assurance requests
21
a20100407.1
Password Reset Procedure w/ Assurers
30
Documentation of Name changes precedent cases is under Support authority within Supports ticket system so therefor here are no counts know to Arbitration.
Procedures
- Removal of inactive Arbitrators
 Rules have been deployed and ruled thru Arbitration, that allows removal of inactive Arbitrators.
Rules have been deployed and ruled thru Arbitration, that allows removal of inactive Arbitrators.
- The removal of inactive Arbitrators is proposed to DRO
- DRO tries to contact inactive Arbitrator and tries to find a solution
- -or- proposes the removal of inactive Arbitrators before Board, that handles the case thru a board motion
.
- New Initial Case Managers Role
While working with arbitration cases and the backlog, new cases receives the arbitration queue thru OTRS - Supports ticketing system. But only half of the Arbitrators have followed the request to get an OTRS account, so the new cases are only handled by about 1-3 Case Managers/Arbitrators, to be moved out of the OTRS disputes queue into the Disputes mailing list so that new cases can be picked up and to be added to the Arbitration queue in the wiki. Until a Case Manager and Arbitrator is appointed to a case, the handling Arbitrator who moved the case from OTRS into the Arbitration queue is to be named the Initial Case Manager, with no authorization over a case. He only manages the transfer of new cases between the communication channels and to inform the dispute filing parties that the dispute filing has been received in Arbitration and to send information about the assigned case number. Later the Initial Case Manager gets replaced by the Case Manager who takes care about a case as Case Manager.
- Delete Account procedure for Arbitrators / Support-Engineers
 By mid of Oct 2010, there was still about 30 open "Delete my Account" requests on the Arbitration queue. We've started a deployment of a standardized procedure for Arbitrators, that Arbitrators can walk thru in handling default "delete my account" requests that includes the results taken from the Arbitration team meeting back in January 2010 about the "Delete Accounts" topic. Further it includes the yet deployed "Delete Account procedure for Support-Engineers" that gets adjusted to manual steps in deleting accounts. Within a few working sessions and meetings the procedure had been deployed and added to the Arbitration lessons with two proposed workflows for Delete Account Requests. The procedure takes into account, that the given Dispute Resolution Policy (DRP) requires the acceptance of all arbitration participients before a case can be started, but in a delete account request case, a user has first to accept CCA to become CCA terminated in the ruling. So therefor the requirement to request for acceptance of CCA before the Arbitration case can start has been changed with a deadline procedure. The user receives a request if he accepts CCA and confirms the Delete Account request. If no response received within a 14 days period, the case starts without users confirmation to be considered an administrative delete account procedure w/o users confirmation. This allows the Arbitrator to continue delete account request cases without written confirmation by the user to block off the blocking issue in processing delete account cases.
By mid of Oct 2010, there was still about 30 open "Delete my Account" requests on the Arbitration queue. We've started a deployment of a standardized procedure for Arbitrators, that Arbitrators can walk thru in handling default "delete my account" requests that includes the results taken from the Arbitration team meeting back in January 2010 about the "Delete Accounts" topic. Further it includes the yet deployed "Delete Account procedure for Support-Engineers" that gets adjusted to manual steps in deleting accounts. Within a few working sessions and meetings the procedure had been deployed and added to the Arbitration lessons with two proposed workflows for Delete Account Requests. The procedure takes into account, that the given Dispute Resolution Policy (DRP) requires the acceptance of all arbitration participients before a case can be started, but in a delete account request case, a user has first to accept CCA to become CCA terminated in the ruling. So therefor the requirement to request for acceptance of CCA before the Arbitration case can start has been changed with a deadline procedure. The user receives a request if he accepts CCA and confirms the Delete Account request. If no response received within a 14 days period, the case starts without users confirmation to be considered an administrative delete account procedure w/o users confirmation. This allows the Arbitrator to continue delete account request cases without written confirmation by the user to block off the blocking issue in processing delete account cases.
End of Oct 2010 we started a run on bulk handling of 30 Delete Account cases, 3 sets of 10 cases each with a pair of a Case Manager and an Arbitrator. 3 Case Managers and 3 Arbitrators works on that run. Currently 23 cases are now closed and 7 of these 30 cases are still running.
Policy
- An appeal did happen with a special "Delete my Account" case where a member deceased, that required action to be taken by Policy Group to rethink about the appeal process - that had defined, that an appeal to be handled by board if once re-opened by an Arbitrator. If board is an arbitration case participient this raises a Conflict of Interests (CoI).
DRP gots an update back in January 2011 with policy group resolution p20110108 "DRP #3.4 Appeal handled by Arbitrators"
- This means, appeals are no longer handled by Board (as written in initial DRP). Following the new policy text change in full:
3.4 Re-opening the Case or Appeal In the event of clear injustices, egregious behaviour or unconscionable Rulings, a review may be requested by filing a dispute. The new Arbitrator reviews the new dispute, re-examines and reviews the entire case, then rules on whether the case may be re-opened or not. If the Review Arbitrator rules the case be re-opened, then the Review Arbitrator refers the case to an Appeal Panel of 3. The Appeal Panel is led by a Senior Arbitrator, and is formed according to procedures established by the DRO from time to time. The Appeal Panel hears the case and delivers a final and binding Ruling.
- This blocked off a potential conflict of interests if board is a party in a case file that gets appealed.
But this also takes a burden to the Arbitration team, as this requires at least 4 working Arbitrators + 1 Case Manager + the Arbitrator the appeal is against. So if the count of active Arbitration team members falls below 6 the appeal process is blocked

Currently we have 2 appeals in the Arbitration queue that didn't get picked up yet and if one of remaining active Arbitrators decides to accept the appeal to be re-opened needs to be passed to an Appeal Panel of 3. The last two months in the FY period the count of active Arbitrators was 1

- Wiki notifications about modifications on Arbitration files only shows sign of life by max 2 Arbitrators.
Delete Account Cases - Part II
The a20100131.1 impact
The discovery process of this arbitration case revealed a potential problem that privacy related data of closed accounts is still kept in the database. The topic data retention has been moved to another case a20110221.1. This case is still running.
- The a20110502.1 case and the appeal a20110511.1 impact
- The a20110502.1 case handles a Delete my Account case that includes adjustments to the Delete my Account procedures for Support-Engineers
- The appeal a20110511.1 (see section Policy above) now blocks handling of all other Delete my Account cases
- Delete my Account cases is not only an Arbitration issue. Several other areas are involved.
- Policy group
- When and how a member can request to resign and what happens with the users data
- A definition is given by the CCA, that all Delete my Account requests have to go thru Arbitration
- A rework of CCA is undergoing discussion in Policy group
- PII data retention topic has not been covered yet
- Arbitration
- Arbitration has to rule over each individual Delete my Account request and to define the CCA termination date.
- The goal here: to define a precedent ruling that before it can be ruled needs Software adjustments
- One of the adjustments is to find a method, to handle several delete account cases under one arbitration case #. A solution has been proposed by Software-Assessment. A generic ruling has been given in the intermediate ruling of case a20110502.1 (see above).
- Support has to handle the Arbitration ruling of Delete my Account requests
- As of software limitations Support-Engineers currently have to walk thru a manualy defined step by step procedure to delete user accounts under arbitration authorisation
- Software-Assessment
- In the bug list of Software-Assessment there are several bugs listed to adjust the Delete my Account procedure with either adjustments in information pages for the Support-Engineers and also an automatic Delete Account procedure, that handles all the manualy steps that has been found in the Supports manualy delete account procedure
- Audit group
- One of the Audit related project tasks is the CCA rollout. The information to all members about the existence of a CAcert Community Agreement and the request to the members about their acceptance to the CCA.
- It can be assumed, that the CCA rollout leads into mass administrative Delete Account cases
- Policy group
- Some of the work has been started. Not all has been finished.
Decreasing Arbitration Backlog
 Since starting with the ATE series back in spring 2009, Arbitration built up an Arbitration backlog that didn't get rid yet. Two forced pushes have been started to drop the backlog. Also one run to prevent increasing of the backlog again:
Since starting with the ATE series back in spring 2009, Arbitration built up an Arbitration backlog that didn't get rid yet. Two forced pushes have been started to drop the backlog. Also one run to prevent increasing of the backlog again:
- Autumn 2010
- 30 Delete Account cases to be handled
- February 2011
- Review on Open/Running 2009 cases
- Feb 2011 - 13 open/running arb cases left from year 2009
- Apr 2011 - 4 running, 1 init arb cases left from year 2009
- Review on Open/Running 2009 cases
- January - April 2011
- 1 Arbitrator - 2 Case Managers who picked up each new case
- 1 Arbitrator - 2 Case Managers who picked up all open cases from 1st half of 2010
- As there was no support by additional arbitrators to pickup the rest of less then 20 open cases from March, October and December 2010 (6 cases) + new cases from 2011 that cannot be picked up by the working arbitrator as he is an involved party in some of this cases and to be the only one active Arbitrator this run has stopped.
By end of June 2011 the overall backlog could be droped from 80 to 62 cases.
One more problem discovered relates to Arbitration backlog and Logging capabilities on critical system. Logging is limited to a range of 6-12 months, so Arbitrators has to assume, that after 6 months evidence gathering thru logfiles is impossible. This pushes Arbitration to handle open cases before a 6 months deadline.
Arbitration future prospects
- With 1-2 active Arbitrators Arbitration team is currently in a mess. The situation for Case Managers is less a problem with about 2-3 working Case Managers. The Arbitrator situation impacts Arbitration:
- Arbitration is currently incapable of action to handle appeals.
- Arbitration is currently incapable of action to handle cases where the 1-2 active arbitrators are involved either way.
- Arbitration is currently incapable of action to work on cases within a temporally acceptable framework
- Potential solutions to amend the situation are:
- search for new arbitrators
- reactivate arbitrators on the list
The search for new arbitrators at ATEs still continues. Reactivation of arbitrators still on the list is questionable as the year in Arbitration has 12 Arbitrators continously on the list, but only about 5 active arbitrators in quarter III and IV of 2010, that droped to 3, then 2 in the last two quarters of 2011. So no one of the remaining Arbitrators (thats at least 7 (9)) did not take care about the Arbitrators job (see Arbitration statistics table 3).
- DRP writes "The Appeal Panel is led by a Senior Arbitrator". The definition of "Senior Arbitrator" is still open and needs to be defined:
- What is a "Senior Arbitrator"?
- What defines a "Senior Arbitrator"?
- Back in 2010 with recuring Arbitration meetings the Arbitration team had a chance to find an answer. As the Arbitration team meetings falled asleep, the chance to get this discussed becomes unlikely.
Arbitration Statistics
Statistics by Year (FY)
2010/2011
2009/2010
2008/2009
2007/2008
..
Total (2010-07-12)
Total (2011-07-04)
Total new
99
134
47
7
..
188
287
Total closed
60 (130)
112 (54) ↑58
46 (34) ↑12
6 (0) →0
..
98
225
Still open/running
39 (62)
22 (80) ↓58
1 (13) ↓12
0 (0) →0
..
91
62
Total handled
130 (60+58+12)
..
189
287
Table 1: Total statistic by Year (FY)
Statistics period July 2010 - June 2011
Arbitrations
2010
2010
2010
2010
2011
2011
2011
2011
Sum
Quarterly snapshot
Jul
Aug
Sep
Q3
Oct
Nov
Dec
Q4
Jan
Feb
Mar
Q1
Apr
May
Jun
Q2
New = Total
8
9
6
23
7
3
7
17
11
10
14
35
7
6
11
24
99
Running
8
7
5
20
3
1
7
11
3
2
9
14
3
1
0
4
Ø 4/month
Closed
0
2
1
3
4
2
0
6
8
8
5
21
4
1
1
6
36
Total
8
9
6
23
7
3
7
17
11
10
14
35
7
6
11
24
99
Table 2: statistics per period (seperated into quarters)
sample: from Aug 2010 we've received 9 new cases. At end of the period (2011-10-01), 7 cases from Aug are still open/running, and 2 cases from Aug are closed. In February 2011, we've received 10 new cases, where end of the period (2011-04-01) 8 cases from Feb was closed and still 2 cases from Feb are in open/running state. By end of the FY period we've received 99 new cases in total, where 36 cases had been closed within a 3 months period (this doesn't cover all closed cases. About all closed cases have a look into table 1). The values of running cases gives an indication how effective/ineffective Arbitration worked in the period and how many Arbitration cases didn't picked up or had not been finished.
Number Arbitrators
2010
2010
2010
2010
2011
2011
2011
2011
Jul
Aug
Sep
Q3
Oct
Nov
Dec
Q4
Jan
Feb
Mar
Q1
Apr
May
Jun
Q2
on list
12
12
12
12
12
12
12
12
12
12
inactive
3
3
3
3
3
3
3
5
5
4
busy
5
5
6
6
6
6
6
6
6
6
active
5
5
3
3
3
3
3
1
1
2
Table 3: Arbitrators active/busy/inactive
x1) fine graded statistic starts back in Jan 2011
Long term statistics 2008 - 2011
Arbitration
2007
2008
2008
2009
2009
2010
2010
2010
2011
2011
Total
Cases
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
New = Total
2
2
0
3
1
0
8
38
29
33
56
16
23
17
35
24
287
Running
0
0
0
0
0
0
0
1
3
1
10
8
5
5
11
18
62
Closed
2
2
0
3
1
0
8
37
26
32
46
8
18
12
24
6
225
Total
2
2
0
3
1
0
8
38
29
33
56
16
23
17
35
24
287
FY Total
7
47
134
99
287
Year Total
4
4
108
112
59
287
Table 4: Long term Arbitration statistics new/running/closed
Arbitrators
2007
2008
2008
2009
2009
2010
2010
2010
2011
2011
Active
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
Q3
Q4
Q1
Q2
on list
1
1
1
4
5
5
8
11
13
13
15
14
12
12
12
12
inactive
4
4
3
3
3
4
busy
7
6
5
5
6
6
active
1
1
-
3
1
-
5
9
10
6
5
4
5
5
3
2
Table 5: Long term statistics Arbitrators active/busy/inactive
UlrichSchroeter
CARS
Software-Assessment-Project Team Report 2010-2011
By end of 2009, CAcert had no working Software-Assessment team, or better, the team was a one person team that doesn't fulfilled audit requirements. So this project group has started their work back in December 2009.
 The ambitious plans that were made at the Essen Software miniTOP mid Dec 2009, to deploy a testserver environment similiar to the production system the Critical team has deployed around January / February 2010. But this was the starting point of the real hard stuff work. It tooks about half a year, until the system was up and running, so software testers could use this system for testing.
The ambitious plans that were made at the Essen Software miniTOP mid Dec 2009, to deploy a testserver environment similiar to the production system the Critical team has deployed around January / February 2010. But this was the starting point of the real hard stuff work. It tooks about half a year, until the system was up and running, so software testers could use this system for testing.
The milestones
In July 2010 the Software-Assessment project team announced their 1st milestone reached with the running testserver-management-system - short TMS. This was the starting point that patches could be tested without root console access to the testserver, so every community member can help on software testing by using the TMS to set their environment for testing on the testserver.
The second milestone was reached 3 months later beginning October 2010 with the first passed Software-Update-Cycle. A simple patch for testing the Software-Update-Cycle, tested on the testserver, reviewed by 2 Software-Assessors and forwarded to the Critical team for implementation including documentation under bugs.cacert.org.
The "Thawte" patch
 Next on Software-Assessment project team workqueue was the "Thawte patch". November 16th 2010 was the by end of 2009 announced expiry date for Thawte transfered assurance and experience points. The problem with current implementation of Assurance points and Experience points is, that the Assurance- and Experience points are hardcoded into the database. So updates (eg. revoke assurance, removal of points) cannot be handled easily without alter the database. So therefor the developers decided for a plan to turn the points counting order first, last assurances counts. By removal of Thawte points users can receive updates by new assurances and also with experience points. So the patch was proposed to be in at least two steps:
Next on Software-Assessment project team workqueue was the "Thawte patch". November 16th 2010 was the by end of 2009 announced expiry date for Thawte transfered assurance and experience points. The problem with current implementation of Assurance points and Experience points is, that the Assurance- and Experience points are hardcoded into the database. So updates (eg. revoke assurance, removal of points) cannot be handled easily without alter the database. So therefor the developers decided for a plan to turn the points counting order first, last assurances counts. By removal of Thawte points users can receive updates by new assurances and also with experience points. So the patch was proposed to be in at least two steps:
- Step 1: display "my points" with the new calculation (incl. removal of "Thawte" points) so that users can react to search for assurances to not loose points, to do assurances to not loose experience points
- Step 2: the production switch with "Thawte" points removal and the turned points counting order
The November 16th deadline passed without further activities - Software-Assessment hasn't finished the "Thawte" patches.
Until today the step 1 patch didn't it onto production. By end of June 2011 we now have an updated patch on the testserver under testing that revealed another problem in the "old" software points assignment procedure, that needs a fix first. So all to say here: the "Thawte" and "turn-Points-order" patch is still under testing and the "Thawte" project is still delayed.
Software testing
Software-Assessment is related also on a working Software test team. Once the Software-Assessment was build up, once Software-Assessment has defined a Software update cycle procedure, the software testing becomes a topic to test the software patches before it becomes applied over the critical system.
A Software testteam has been build around August 2010 for either test the testserver and the testserver-management-system. If the testserver is usable for testing, if the testserver is comparable to the production system. After finishing these tests, it tooks a while to bring in the first real patch - the "Thawte" patch. The deployment of the "Thawte" patch was defered week by week. In the meanwhile the Software-Assessors added other patches to the testserver for testing.
But activity in the software testing area stalls. The "Thawte" patch was  probably a hard big bang, so the testers was swamped. So we've added easier patches to the testserver. But again, no response from the testers. With regular announcements to the Software testers, no one patch becomes tested. At eastern 2011 we've started the Software-Testing Easter Egg Challenge also to find more active testers. But 0 response so far.
probably a hard big bang, so the testers was swamped. So we've added easier patches to the testserver. But again, no response from the testers. With regular announcements to the Software testers, no one patch becomes tested. At eastern 2011 we've started the Software-Testing Easter Egg Challenge also to find more active testers. But 0 response so far.
This situation is a real audit blocker. So this has been addressed to board that leads in the May and June 2011 Software Testers Reward Challenge to find more active testers. But the May results finishes with 3 reported tests by 2 software testers and June finished with 3 well known to the community software testers with a total of 5 reports by 6-9 still running added bug fixes to the testserver. The Software-Testers Reward Challenge was announced thru CAcert's blog, CAcert's wiki and also in the CAcert's public general mailing list. These channels did not bring one more software testers into the team.
Some ideas that are not new flying around to start with Software camps for Software development and also Software testing. Bring in as many developers and users into a camp for starting hacking. So this is a plan for the next period.
Class3 Re-sign project
The Class3 Re-sign project evolved to a great success story for the Software-Assessment project team and so also to other teams with fresh ideas and resources.
Back in January 2010 (see also Audit team report), the board decided a motion with a wider impact: Motion m20100117.3 "No new subroots on current root, plan for new root". From this plan evolved the Big Masterplan to become Audit Ready including the New Roots & Escrow project. Some thoughts was, to pass the New Roots project till end of 2010 or beginning 2011.
The Policy group activities stopped mid 2010. The Audit team is too small to pickup such task. Next time this becomes a topic was January 2011, with another withdrawn board motion m20110212.1 "Discontinue issuing certificates from Class 3 root". This motion can be seen as a starting signal to put this topic to the recuring Software-Assessment project team meetings to the agenda.
Mozilla's announcement Dates for Phasing out MD5-based signatures and 1024-bit moduli has set a deadline to June 30th 2011. One of the Software-Assessment project team topics on the teams tasks was to get the signer up and running on the testserver machine. Andreas Bäß and Markus Warg who worked since spring 2010 on this project gets support by the new Software-Assessor Michael Tänzer so at the end Markus and Michael got the signer up and running. Also to name the Critical team here, who did a backup of the current two running scripts on the production server on their between Christmas and New Year maintenance visit. Andreas created a testRoot and testSubRoot. So the testteam could begin testing with client and server certificates on the testserver.
In April Michael presented an idea for a smooth Class3 upgrade procedure in the Software-Assessment project team meeting. A call to the Software Testteam goes unheard. So the project team scheduled a workshop sesson close before the next starting May Board meeting. Within this 3 hours workshop sesson Michael deployed the Class3 subroot Re-sign procedure. 3 other project team members started testing with the new Re-signed class3 Test-subroot that revealed, that no problems occures. This was the signal to present the Class3 Subroot Re-sign procedure to the Board to push forward this project.
Board decided in their 2011-05-15 meeting with the motion m20110515.2 that CAcert upgrades their class-3 subroot. As current PR officers seat is vacant, this role currently is held by the Board. So Board asks the community to assist in the preparation of a press release with the board motion m20110515.3.
The task to write a press release has been picked up by Alexander Bahlo, who also helped in the past to write the Call for Papers for event applications like Cebit 2010, Linuxtag Berlin, BLIT Potsdam, Fosdem 2010 and Fosdem 2011 and much more. With experience in this area, we found a longterm member to assist this project from the Public Relations side.
The Software-Assessment project team meeting moved to the Class3 subroot Re-sign project meetings. The meetings are running thru a telco server that is provided by the Dutch CAcert Assurer Kees van Eeten.
A timetable has been deployed. The procedure has been sent to the Critical team. The press release has been prepared. A working page for the text updates (Class3 fingerprint updates) and a list for press release distribution has been prepared, so on the day X, all was prepared to push the Class3 Re-sign project. Some patches was prepared by the Software-Assessors and also sent to the Critical team for applying to the critical system at the GO.
At May 23th 2011 the Critical team executed the Class3 subroot Re-sign procedure, so the new subroot was present for the GO.
A Support FAQ page has been prepared to support Support about user questions.
 At June 5th Board gaves the GO for distribution with the motion m20110605.2 approval of press release, blog post and members notifications.
At June 5th Board gaves the GO for distribution with the motion m20110605.2 approval of press release, blog post and members notifications.
The proposed rollout day was set for the period between 2011-06-15 - 2011-06-20. A request for translations of press release was sent out to the community so at the rollout day we have a German - Dutch - French - Spanish - Russian translation of the English press release. A dispute filing has been started for mailing Organisations under the Organisation Assurance program, that contacts can be informed about changes that effects Organisations (Class3 subroot software rollout within Organisations, update of webservers under Organisations control)
Based on the upcoming holidays, the rollout day has been altered. The final date set: Friday, June 10th 2011.
The coordinated replace of the new re-signed Class3 subroot, the replace of the affected software by the Critical team, the press release distribution, the blog post by the PR group, the changes of the wiki pages, documents within the SVN, the mailing in the mailing lists by the Software-Assessment project team members started Friday afternoon June 10th 2011.
Until today we did not receive any major nor minor problem reports regarding the Class3 Subroot Re-Sign. The started dispute file is currently running. The ruling will not help for the Class3 Re-sign information as the deadline did pass, but for the upcoming New Roots & Escrow project a precedent ruling will help. Also to fill the gap in communication within Organisation Assurance area to contact all assured Organisations.
Summary: The successful finished Class3 Subroot Re-sign project can be seen as a test for the upcoming New Roots & Escrow project rollout. The project team identified the key areas that needs to be contacted. The documentation of this project is also an instruction list for the New Roots rollout.
Thanks to all the members who helped to get this project running and that we've finished successfuly.
Weak Keys / Weak Passwords Arbitration cases
March 11th CAcert received an email from a member reporting a security issue, with the announcement, to publish a weak keys problem soon, giving CAcert the chance to prepare and install fixes on their systems. This case has been refered to Arbitration to be handled under:
a20110312.1 Weak CAcert certificates found in EFF SSL Observatory data
The Arbitrator works hand in hand with Software-Assessment and the Critical team. This case can be seen as a project with involvement by several CAcert teams too. The weak keys problem resulting in revocation of a couple of certificates, that falls under one of the following criterias:
- Cause: Small Key Size
- Cause: Exponent is too small
- Cause: Debian Vulnerability
Details can be found under the wiki page WeakKeys.
A roadmap of further actions has been deployed. First issue was to find the weak certificates/keys, notify their owners and then revoke them. The second issue was to modify the software that weak keys are not accepted any more in the future.
 The process in handling these problems started with a global systems check over all CAcert issued certificates with
The process in handling these problems started with a global systems check over all CAcert issued certificates with
openssl-vulnkey => 879
DumpWeakCerts.pl => 1679
affected certificates. This Arbitration case has been finished with a final ruling in July 2011. The complete process has been disclosed by the Arbitration file.
A second security issue effects weak passphrases that were used to secure user accounts. The problem started with the bug report that users using the sample password "Fred Smith" from the enter password pages. This case als has been refered to Arbitration:
a20110419.1 Weak Passwords Problem
The roadmap was similar to the Weak keys issue roadmap, first to identify the effected count of accounts and a second step to fix the issues.
A fix has been implemented August 1st, 2011 but the arbitration case is not yet closed. So details will be disclosed later by closing the arbitration case under the arbitration file.
Each of these "Weak" issues affected 3 bug numbers each:
a20110312.1 Weak Keys => bug #918, bug #954, bug #964
a20110419.1 Weak Passwords => bug #637, bug #953, bug #963
Software-Assessment and Software Testteam works thru hand in hand with Arbitration and the Critical team. The weak keys issue could be handled with the Testserver built including the activated test signer. The impact of these 2 security issues was on a broder basis, not only fixing a bug, but also doing investigations and deep system analyses on the critical systems data that needs assistance from Arbitration to get the issues fixed. So these 2 cases can be also seen as a success story of CAcert teams shared project work.
Testserver deployment / Disaster Recovery test
The testserver deployment can be read as the step towards Audit in the Systems area regarding disaster recovery.
The testserver that was deployed by the Critical team back around January 2010, did undergo the Software-Assessment project team and Software Testteam test in July, August 2010.
The problems found:
missing certificates creation, missing certificates usage (eg. missing Cert login function) (-> signer deployment)
- missing location database does not allow to add locations, some data needs to be added initialy
- missing language pre definitions leads to missing languages support
The signer deployment tooks about 9 months to finish. This was less a problem of a disaster recovery szenario, but a problem of the testserver host, as the running server was up and running and the signer needs to be virtualized to a VM environment and to communicate with the testserver.
Later on, the test signer was also up and running, one more problem has been identified:
- missing data in Table Root_Certs that contains the CN as stored in the live root certificates
Summary: On a complete database restore after a disaster issue, the missing data is already available. On a system buildup from scratch without restore of the "critical data", at least 4 tables needs to be pre-filled that a system can be used from scratch in production. No further problems found.
The testserver host has also become a test platform for OS upgrade and application upgrade tests by the Critical team with a second testserver.
Root access to the testserver machines is limited to the Critical team and the appointed Software-Assessors. This is about to keep the testserver in a state that is as equal as the production system. A VM image of the running testserver cacert1 has been copied for download and local usage by software developers at April 21st 2011.
Currently the testserver host, that also helds the central new software repository under git is hosted in Frankfurt in a server room. The plans here are to move the machine to a new hosting provider. Here the team works together with the (non-critical) Infrastructure team to find a new hosting provider so the non-critical machines and the testserver machine can be moved on to one or two machines in the new hosting provider server room.
Projects in the Software-Assessment project team pipeline
The tasks for the Software-Assessment project team has moved to also taking the leadership in projects that are system related. This has been shown in the Class3 Re-sign project as such a project first needs team building that didn't happen if no one picksup such a task. The Software-Assessment project team is a working team not limited to the Software-Assessors tasks. Its more a communication platform that allows pickup of projects and their deployment. Especialy if multiple teams has to work together (eg Class3 Re-sign project -> Software-Assessment, Board, Critical Team, PR).
The recuring Software-Assessment project team meetings are a fixed schedule, seldom defered. Its open to all who can assist with their experience either way to bring the projects forward that are on the task list:
Policy and Arbitration ruling based Software fixes
Since the Software-Assessment project team starts working the task was focused on the "Thawte" patch. As this patch did not make such progress as expected, other issues evolved like the Weak Keys problem, Weak Password problem. In 2010 two Assurance subpolicies has been voted to DRAFT by Policy group. Several Arbitration rulings results in new bug reports, that Software-Assessment needs to take care about.
 In the meanwhile Software-Assessment deployed a parallele handling of new patches handling, so the the "Thawte" patch no longer blocks other essential bug fixes.
In the meanwhile Software-Assessment deployed a parallele handling of new patches handling, so the the "Thawte" patch no longer blocks other essential bug fixes.
Next in the work queue:
- Patches to assist Policy on Junior Assurer/Member
- Patches to handle new TTP-assisted-assurance subpolicy
- A couple of bug reports that requires to adjust new members join form
CCA rollout
CCA rollout is the audit project to inform all members about existance of a CAcert Community Agreement and to request the acceptance from the members. Before a CCA rollout can be started, it requires system design adjustments, so that CCA acceptance can be auditable documented.
A couple of patches have been applied to the old testserver test1.cacert.at back in mid 2009, and have been removed late 2009 as no testing did happen.
In the meanwhile with the Class3 Re-sign project experience the CCA rollout can be seen as an individual project not limited to Software-Assessment only, but also to other CAcert groups and teams (audit team, board, arbitration, policy group, infrastructure, critical team, support). This project requires a mailing to the members, that needs approval by board and or arbitration to be handled under Critical team and/or Support. The members that cannot be reached by the mailing and also not responding members will result in an unknown count of administrative account removals that needs handling thru Arbitration and Support. This needs to be prepared before the CCA rollout can start with either Arbitration precedent ruling or a similiar prepared procedure, that handles such cases efficiently.
So probably Software-Assessment project team has to pickup the project leader role for this project, to make progress with this audit blocker project.
New Roots & Escrow
The next big audit related task is the New Roots & Escrow project.
Software-Assessment project team picked up the task relating the question how sufficiently the New Roots project can handle CRL's. This is based on the last discussion results in the roots mailing list regarding multi-member escrow method.
The New Roots & Escrow project can be split in three working areas:
- New roots ceremony creation
- this has been tested back in late 2008, the procedure works and can be repeated
- Find a CRL handling procedure and mechanism with the new roots
- To set the Root offline, CRL handling requires a sub infrastructure for CRLs. A potential solution can be the indirect CRL handling as defined under RFC 5280. This needs testing first before this can be implemented
- Find a proper Roots Escrow method, that works for CAcert and CAcerts limited resources.
- The Escrow project is not realy a Software-Assessment project. There is some progress here by some individuals, but infos receives Software-Assessment project team, so that coordination of the sub projects will probably result in a project team leader role for Software-Assessment project team in the future.
 The CRL project is currently under Software-Assessment project team recuring meetings topic, a test lab scenario has been defined but needs further testing.
The CRL project is currently under Software-Assessment project team recuring meetings topic, a test lab scenario has been defined but needs further testing.
Automated Software Testing
Automated Software Testing is a topic of Continous Integration (CI), a method in software development.
Automated Software Testing is a topic that has been on the agenda for Software-Assessment project since the team starts working. But sadly, did not get that much support as expected. So the Software-Assessment project team still continues searching for experts in this area. With the skills and experience to deploy an automated software testing environment that can be used to automate CAcert's software testing.
The Software-Assessors team
Starting July 2010 there were 3 Software-Assessors appointed: Philipp, Markus, Dirk.
By starting the active period for software updates, Software-Assessment project teams comes along, that we need more active Software-Assessors, especialy if one of the Software-Assessor is also an active developer.
This leads in the proposed new Software-Assessor Michael, who had passed his ABC in role as Support-Engineer. Michael accepted his move from Support to Software-Assessment. This process finished with Michaels nomination to become Software-Assessor.
But again, in early 2011, the team is running low on active Software-Assessors again. So Software-Assessment project team searched for candidates to become Software-Assessor. Ted accepted his nomination. After passing his ABC board nominated Ted as 5th Software-Assessor March 2011 with board motion m20110307.1
The Software-Testteam
In the Software-Assessment project deployment, the building of an independent, but Software-Assessment related Software Testteam has been started, to seperate the Software testing from the development and deployment process. An additional independent instance within the deployment process, that checks and tests the proposed fixes before they are deployed to the production system.
 In the meanwhile the Software-Testteam identified a couple of critical system issues related to proposed bug fixes. To give an example:
In the meanwhile the Software-Testteam identified a couple of critical system issues related to proposed bug fixes. To give an example:
With the "Thawte/Points-turn-count-order" patch a software tester found a long running bug, that adds 2 million assurance points over another user acount

This issue has been fixed under the bug #959
Without a running software testteam this problem probably hasn't identified yet and could lead to improper assurance points allocations. But as said, this issue has been fixed.
Without a deployed automated software testing system, the software tests have to be made manualy. This needs resources. But there is no requirement, that software testers have to be Software-Assessors. So therefor everybody can help in the software testteam. Everybody who joined CAcert by creating an account thru the www.cacert.org join page. Software testing is similiar to the working with the production website - except: documentation. Every test step to document in a report, that becomes part of the software deployment process.
A first software test team has been build mid 2010. By starting with continous software patches the software testers were all gone. The Software testteam did not get any new member by the Software Testers Reward Challenge so now the team is working with 2 main software testers and about 2-3 addtl. supporters. An overview of the current Software-Testteam can be found on the wiki page Software Test Team and availability.
Software-Assessment Documentation
The Software-Assessment project team documents their activities under the wiki page Software/Assessment including their weekly meetings with agendas and minutes.
The central documentation database is the mantis bugtracker bugs.cacert.org. The bugtracker is also the documentation site for the software tests reports.
The bugtracker has been customized by the Software-Assessors so the system now allows the listing of reviewed bugs. The system will be used to report new bugs, to document the roadmap for a patch, the review states by Software Assessors, the software testing reports and the deployment to the critical system. So this system will be used by at least 5 groups/teams:
- users/members reporting bugs
- software developers picking up new bugs for development
- Software-Assessors reviewing the patches
- Software-Testteam to test and report the patches testing
- the critical team, to document the system implementation
The process of Software-Updates has been documented under the wiki page Software/Assessment/Documentation and the documentation for the bugtracker under the bugtracker documentation. Both can be used now for a review of the Security Policy and the Security Manual regarding Software-Assessment.
Statistics
07/2010 - 06/2011
Date deployed
success
defered/rejected
2010-09-14
7
1
2010-09-27
3
0
2010-11-29
1
0
2011-02-16
0
1
2011-03-16
1
0
2011-06-10
1
0
2011-06-15
1
0
Total
14
2
07/2011 - today
Date deployed
success
defered/rejected
2011-07-22
2
0
2011-07-28
2
1
2011-08-01
2
0
Total
6
1
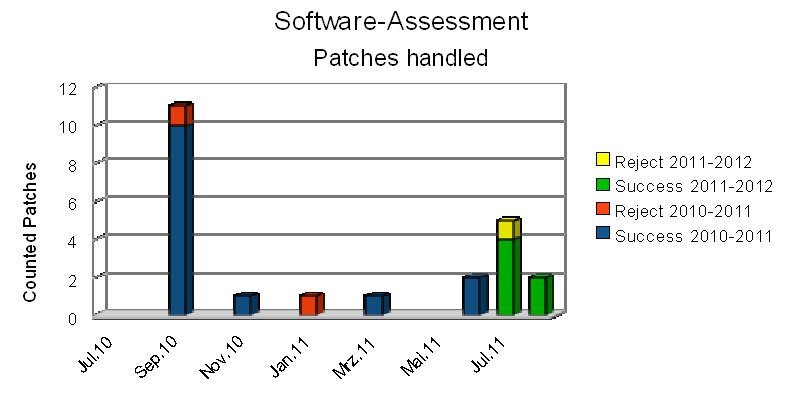
Summary
 The work of Software-Assessment project team that has started back in Dec 2009 was first focused on the big patches: "Thawte patch", "CCA rollout". The focus moved in the first half of 2011 to a parallele work, adding more patches into the working queue, to be handled by Software-Assessors and Software-Testers. With the deployed update process, that allows parallel processing of patches, the team becomes active in the 2nd quarter of 2011. The result can be seen also by statistics with a couple of patches fixed starting June 2011, July, August 2011. All these patches added into the queue as a side effect of the Software Testers Reward Challenge. So we have now about continously 10 patches in parallele in the pipeline.
The work of Software-Assessment project team that has started back in Dec 2009 was first focused on the big patches: "Thawte patch", "CCA rollout". The focus moved in the first half of 2011 to a parallele work, adding more patches into the working queue, to be handled by Software-Assessors and Software-Testers. With the deployed update process, that allows parallel processing of patches, the team becomes active in the 2nd quarter of 2011. The result can be seen also by statistics with a couple of patches fixed starting June 2011, July, August 2011. All these patches added into the queue as a side effect of the Software Testers Reward Challenge. So we have now about continously 10 patches in parallele in the pipeline.
A second side effect of the parallele processing of patches allows a fast processing of emergency patches, to bypass the bundles of patches in the pipeline. So one more of the open topics in the Software-Assessment project tasks can be closed now. The 3rd milestone "Build + Document Emergency Patches Path".
Ulrich Schroeter, Dirk Astrath, Michael Taenzer, Bernhard Froehlich, Martin Gummi, Marcus Maengel, Alexander Bahlo, Marc-Oliver Hofmann
Critical System Administrator Team Report July 2010 - June 2011
Webdb server
No major changes were made to the hardware infrastructure for the CAcert servers in the past reporting period. A major software upgrade step was the switch of the webdb server from the no longer supported Debian "Etch" release to the Debian "Lenny" (oldstable) release in December 2010. The second part of this upgrade (applying the same changes to the chroot environment in which the webserver runs) is still due, and is slated for the summer of 2011.
DNS service
 The DNS service has been raised to a new level of security by adding DNSSEC-based signatures to the CAcert zone files, and installing the OpenDNSSEC software from NLnet Labs to manage the DNS signing keys and signing process. Due to the lack of support for the DNSSEC protocol at go-now.at, which has served CAcert for many years, we had to say goodbye to them. Fortunately we have been able to find four external DNS (slave) servers with full support for DNSSEC in addition to our own (master) server. With SNS@ISC PB Anycast service among these, CAcert's DNS availability is now better than ever before.
The DNS service has been raised to a new level of security by adding DNSSEC-based signatures to the CAcert zone files, and installing the OpenDNSSEC software from NLnet Labs to manage the DNS signing keys and signing process. Due to the lack of support for the DNSSEC protocol at go-now.at, which has served CAcert for many years, we had to say goodbye to them. Fortunately we have been able to find four external DNS (slave) servers with full support for DNSSEC in addition to our own (master) server. With SNS@ISC PB Anycast service among these, CAcert's DNS availability is now better than ever before.
OCSP and CRL service
The OCSP and CRL services were migrated in mid-June 2011 from the shared infrastructure server sun2 to the fully critical-admin controlled server sun4. Much effort has been spent on configuring and patching the OCSP server software (from the OpenCA project) to raise the reliability of the service to an acceptable standard. By switching to the openca-ocspd-1.9.0 software base with a significant number of local patches we have achieved this goal. The service can now essentially run unattended without a recurring need for manual restarts etc. In addition the propagation delay of updates to the certificate revocation lists has been reduced.
Backup service
The boxbackup server was upgraded and reconfigured to provide real-time mirroring of all backed up data over two disk drives. Critical services running on the sun4 server have also been reconfigured with real-time mirroring of their data.
On-site visits
The log of visits to the hosting facility shows the following "on site" activities:
- [10.12.2010] maintenance on sun1, sun4 and signer
- [12.05.2011] adding backup drive to infra01
- [23.05.2011] signer maintenance, password changes
- [10.06.2011] signer disconnect backupdisk, infra01 USB disk test
- [26.06.2011] replace broken Linksys switch
Interesting to note is that the number of visits (5) was considerably smaller than in the previous year (8), and only two of them could be labelled emergency visits.
Logging
All other (i.e. most!) system administration work has been performed remotely. Issues directly affecting the operation of the webdb server continue to be logged to the cacert-systemlog@lists.cacert.org mailing list (archived at https://lists.cacert.org/wws/arc/cacert-systemlog ) with headings like "configuration change webdb server", "security upgrades webdb server" or "cvs.cacert.org checkin notification". This logging is now also used for changes to all other services like DNS, OCSP etc. under critical-admin management.
Interaction with infrastructure services
 In the previous reporting year it was hoped that the manageability and auditability of the critical systems could be improved by moving all (non-critical) infrastructure services out of the current hosting center to elsewhere in 2010. This does not seem realistic anymore. Instead, an effort has been started to setup sun1 as a new infrastructure server, with a more modern and better configured software base, and easily separatable from the critical systems. The critical-admin team has set up the base server and handed it over to the infrastructure team at the start of 2011. Since then the svn and blog services have been migrated successfully to this new setup. Unfortunately, the goal of freeing up sun2 entirely by mid-2011 has not been reached. It is important though that the remaining migration work is sped up, since we need this hardware soon for migration of the critical webdb server which is still running on rather old and aging hardware.
In the previous reporting year it was hoped that the manageability and auditability of the critical systems could be improved by moving all (non-critical) infrastructure services out of the current hosting center to elsewhere in 2010. This does not seem realistic anymore. Instead, an effort has been started to setup sun1 as a new infrastructure server, with a more modern and better configured software base, and easily separatable from the critical systems. The critical-admin team has set up the base server and handed it over to the infrastructure team at the start of 2011. Since then the svn and blog services have been migrated successfully to this new setup. Unfortunately, the goal of freeing up sun2 entirely by mid-2011 has not been reached. It is important though that the remaining migration work is sped up, since we need this hardware soon for migration of the critical webdb server which is still running on rather old and aging hardware.
Cooperation with Software Assessment Team
We continued to support the Software Assessment Team by maintaining a test server (on a virtual machine) which looks as closely as possible to the production webdb server. Signing capability was added to this test facility. A second test server has been set up for preparing the Etch -> Lenny upgrade described above. Besides creating a usable test environment, this also served to strengthen our capability for (re-)building a new webdb server from scratch, documenting many hitherto obscure aspects of the current production server (which is essentially inherited from its original author, quirks included). The patch process developed by the Software Assessment Team has resulted in a number of successful patch updates to the production server.
Team change
Unfortunately, we had to say goodbye to Stefan Kooman as member of the critical sysadmin team. He has started on June 1, 2011 in a new job as Unix Engineer with BIT, the hoster of CAcert's equipment. Due to CAcert's security policy this role is not compatible with a critical sysadmin position. We want to thank Stefan for his contributions over the past two years, and we are also happy that we don't loose him completely, as he has recently joined the Oophaga Access Engineer team! As a side-effect of this team change, all critical passwords (root, grub, file system encrytion etc.) have been changed at the end of May 2011 to ensure that they are only available to the current team members. This change was a good security exercise in itself.
Plans
Plans for the coming year include:
- upgrade chroot environment of webdb server to Debian Lenny
- migrate webdb server to better hardware (sun2)
- improve database backup procedures
- prepare system software upgrades (Debian Squeeze, OpenSuSE 11.4)
- expand and improve server documentation
- look into replication of OCSP and CRL services on external servers
- expand the sysadmin team
Wytze van der Raay, Mendel Mobach, Stefan Kooman (until June 2011)
Education Team Report
Management of CATS and the Assurer Challenge
The CATS user interface has been translated to several new languages: spanisch, french and dutch. Since review of a second native speaker is missing the new languages are still not installed on the productive system.
Also translation of the Assurer Challenge test to french and spanish have been started, but are still in work. Dutch translation did not make progress since last year's report.
 A new kind of test, the Triage Challenge has been created by the support team using the CATS platform.
A new kind of test, the Triage Challenge has been created by the support team using the CATS platform.
The long standing bug when tying CATS with a class 3 certificate has been tracked down and fixed.
During 2010 (numbers only available per calendar year), 166 PDF certificates and 20 printed certificates for passed Assurer Challenges have been issued.
Some statistics for the time July 2010 to June 2011:
- 2888 test have been made, 1317 english Assurer Challenges, 1544 german ones and 27 Triage Challenges
- 1480 of the Assurer Challenges has at least 80% correct answers and are therefor counted as passed
- 1095 different users (that is, different certificates used to login) have passed the test at least once
- 225 users tried the test at least once but don't have a successful test recorded
- On the average those who passed the test had about one (more exactly: 0.94) unseccessful tries before passing.
Supporting ATEs
ATEs have been supported, by providing access to the SVN repository to store presentations updated by the Event Team and by doing some review of those documents.
Consolidation of training documentation
The WiKi page Brain/EducationTraining has been updated to link training and education documents provided by the different teams.
Prospects for the next year
Not many differences compared to last year:
- Finish the started translations of CATS test and user interface.
- Extend and update the pool of questions for the Assurer Challenge, especially in the area of Arbitration
- Support Event Organisation in improving and extending the present materials for ATEs (see SVN)
- Improve the CATS admin interface so editing questions and answers is a bit more comfortable.
- Improve the CATS database structure and admin interface to give better support for handling questionaires in different languages
Events Team Report 2010-2011
In the FY 2009-2010 we had 52 Assurance Events in total, 4 of them were announced as ATEs.
Year
Months
Count
ATEs
did not happen
ATEs not happened
Reports rcvd
2011
01-06
15 (-5)
7 (+6)
1
2
8 (+4)
2010
07-12
21 (-11)
5 (+2)
3 (?)
0
8 (+2)
Total
2010-2011
36 (-16)
12 (+8)
4
2
16 (+6)
2011: in total 36 Assurance Events takes place with 16 Event reports received (44%).
2010
01-06
20
1
0
0
4
2009
07-12
32
3
7
1
6
Total
2009-2010
52
4
7
1
10
2010: in total 45 Assurance Events takes place with 10 Event reports received (20-25%).
 Assurance Events by Countries:
Assurance Events by Countries:
Country
2011
2010
2010
2009
DE
6
15
12
20
NL
2
2
2
5
US
3
1
2
1
AU
1
2
1
CH
1
1
2
JP
1
BE
1
1
CA
1
ES
2
FR
1
SE
1
DK
1
Total
15
21
20
32
Event Reports
 The Events Reports problem did make some progress. Starting Audit over Assurance back in Spring 2009, Auditor requested to bring in an Event report for each passed event with a statement from the Events Organizer, that all assurances conducted by Assurance Policy. The ongoing reminders results in a double of events reports received related to the count of assurance events. But the quantity needs further increase.
The Events Reports problem did make some progress. Starting Audit over Assurance back in Spring 2009, Auditor requested to bring in an Event report for each passed event with a statement from the Events Organizer, that all assurances conducted by Assurance Policy. The ongoing reminders results in a double of events reports received related to the count of assurance events. But the quantity needs further increase.
Event reports are not just for fun. Event reports will help CAcert in passing a future audit as the event reports delivers evidences in the assurance area that assurances given followed the policys. If there is some more info written in an events report this may help also other event organizers in organizing an event. But the main topic is a statement by the event organizer what he has done to prepare the event to become an event that followed AP.
Cross Community Work
 The cross community work that was started in Autumn 2009 continues in last period. A couple of ATEs were sponsored by other groups or rooms were made available. At events CAcert works together with OpenOffice, OpenSource-Treffen and Sidux. secure-u has become a sponsor for the Germany ATEs.
The cross community work that was started in Autumn 2009 continues in last period. A couple of ATEs were sponsored by other groups or rooms were made available. At events CAcert works together with OpenOffice, OpenSource-Treffen and Sidux. secure-u has become a sponsor for the Germany ATEs.
With the relation to other OpenSource groups we can share the work on booths, we can bundle the resources. E.g. if we have not enough Assurers for a booth we built a network of Assurers at an event like Linuxtag or shared our booth with other groups eg OpenOffice at Fosdem.
Support on Events
 Support from the Community for Events did shrink. This also can be read in the count of events (-33%) against previous period. The "human resources problem" that we discover this year has also been discovered in the events area. The "big events" Cebit and Linuxtag Berlin has shown a big problem in activate the assurer base. Without a booth we've managed this years Cebit with an alternate plan to be available at the fairground at noon for an hour with some assurers. The Wednesday and Saturday meetup we've met around 40 assurees (back in 2009 this was the count of assurances in half of a day by an assurer) so an estimate of less then 10% of assurances compared to 2009 or 2010 were given. Linuxtag day #1 started without any CAcert attendance, so an emergency call with a scripted mailing activated at least enough assurers for the day #2 and upcoming days.
Support from the Community for Events did shrink. This also can be read in the count of events (-33%) against previous period. The "human resources problem" that we discover this year has also been discovered in the events area. The "big events" Cebit and Linuxtag Berlin has shown a big problem in activate the assurer base. Without a booth we've managed this years Cebit with an alternate plan to be available at the fairground at noon for an hour with some assurers. The Wednesday and Saturday meetup we've met around 40 assurees (back in 2009 this was the count of assurances in half of a day by an assurer) so an estimate of less then 10% of assurances compared to 2009 or 2010 were given. Linuxtag day #1 started without any CAcert attendance, so an emergency call with a scripted mailing activated at least enough assurers for the day #2 and upcoming days.
Events scripted mailing
With the Arbitration precedents case a20090525.1 "Event officer request recurrent notification to assurers near the location of the following ATEs" a scripted maiiling procedure has been implemented back in spring 2009 that assists Event Organizers to contact Assurers near their location. This scripted mailing has been used several times:
- 2011 1st half: 8 mailings sent to 8602 recipients (2010: 4)
- 2010 2nd half: 8 mailings sent to 5643 recipients (2009: 6)
for event organizing or for event announcement.
A total of 16 mailings with 14245 recipients (approx 890 recipients per mailing) within the last period.
The overall result was a success as Event Organizers found assistance by Assurers or people comes to the Events.
Push AP to Community
 The push of AP into the Community could be concluded as a big success, since started early 2009 and can be seen as finished. At all bigger and smaller events Assurance now were conducted by AP. Assurers takes care about the Assurance statement, to not only check identities, also to check the Assurees to be bound to CCA and also bound into Arbitration. The training to our new assurers still continues.
The push of AP into the Community could be concluded as a big success, since started early 2009 and can be seen as finished. At all bigger and smaller events Assurance now were conducted by AP. Assurers takes care about the Assurance statement, to not only check identities, also to check the Assurees to be bound to CCA and also bound into Arbitration. The training to our new assurers still continues.
UlrichSchroeter
CARS
ATE / co-Audit Team Report 2010-2011
 Co-audit team season 2010/2011 work started back in February 2010 at Fosdem Bruexelles with the co-audit definitions and finalize at Cebit 2010 so the co-audit season was launched at Cebit 2010. Since than
Co-audit team season 2010/2011 work started back in February 2010 at Fosdem Bruexelles with the co-audit definitions and finalize at Cebit 2010 so the co-audit season was launched at Cebit 2010. Since than
- 10 ATEs in 3 countries and
- 141 counted co-audits in 6 countries
did happen with
- 8 appointed co-auditors.
ATE tours
Board supported ATE's in Australia mainly to find new board member candidates for the CAcert Inc, to fulfill the new Australien Associaton Act, that requires 3 Australien directors. So this also helps the ATE team to push ATE's in Australia and doing co-audits in Australia.
 Secure-u voted in their December 2010 AGM to support CAcert's ATE tour for Germany.
Secure-u voted in their December 2010 AGM to support CAcert's ATE tour for Germany.
An ATE Tokyo has been prepared and a presentation has been held by Peter Yuill dated 2011-03-05, but the later discussion it has been downgraded to a regular assurance event and the 3 educated assurances given to be seen as a training for doing co-audits for the new prospective co-auditor candidate Peter Yuill. It has been shown, that most of the attendees only wants to receive assurances.
ATEs that did happen in a series of more planned ATEs
- The Australien ATE tour that started with ATE-Sydney 2010-03-24 continued with
- ATE Canberra (2010-10-12) (*)
- ATE Melbourne (2010-12-16) (*)
- ATE Brisbane (2011-01-24) (*)

- Germany ATE's
- ATE Essen (2010-09-25)
- ATE Aachen (2010-10-04)
- ATE Hamburg (2010-11-05)
- ATE Muenchen (2011-04-02)
- ATE Bonn (2011-06-08)
- ATE USA tour
- ATE Washington (2011-06-18)
- ATE New York (2011-06-19)
ATE presentations
 There were some plans to rework the ATE presentations that have been used back in the ATE 2009 tours and the beginning 2010 ATE tour. From Assurance Officer there were a couple of new topics received that needs to be added to the existing ATE presentations and also to update the Audit presentations. In a series of ATEs the presentations gets updated step by step upto current last state v4.6-Bonn. The presentations are available in English and German language and are located in the SVN
There were some plans to rework the ATE presentations that have been used back in the ATE 2009 tours and the beginning 2010 ATE tour. From Assurance Officer there were a couple of new topics received that needs to be added to the existing ATE presentations and also to update the Audit presentations. In a series of ATEs the presentations gets updated step by step upto current last state v4.6-Bonn. The presentations are available in English and German language and are located in the SVN
Co-Auditors documentation
A wiki page has been created to document the co-auditors team and their work. This can be found under:
Co-Audit Season 2010-2011
Co-Audits were pushed for Germany, Australia and the USA.
A co-Audit for Japan that was planned close before the Japan disaster did not happen in a way as expected, so it was downgraded thereafter to a regular assurance event.
Report on 2010 142 coaudits in series 2010

1
2
3
4
5
6
#
errors
ATE
EP
CCA
err
1em
Dox
sig
Priv
% att.
0-50
Summary
37
47
30
7
15
27
142
1.6
69
24
Report on 2010 / by country 142 coaudits in series 2010 / with categories by country
country
1
2
3
4
5
6
#
errors
ATE
EP
CCA
err
1em
Dox
sig
Priv
% att.
0-50
DE
33
42
23
5
10
25
99
1.4
65
26
NL
75
50
50
0
25
25
4
2.3
50
40
BE
50
75
75
25
50
25
4
3
50
17
FR
100
80
100
0
60
80
5
4.2
20
16
AU
36
50
32
5
9
9
22
1.4
95
19
US
25
63
38
38
38
63
8
2.6
100
11
Summary
37
47
30
7
15
27
142
1.6
69
24
Co-Audit Budget
Board has funded ATEs in the AU for the search for new Inc members that may become potential board member candidates to fulfill the Association Act requirements of at least 3 board directors to be NSW AU citizens. So this run's side effect was, that it also supported the ATE tour for AU.
A second sponsoring has been pushed by the Germany Association Secure-u with their December 2010 motion, to actively support ATEs in Germany. So at least the ATE Munich did happen.

AU tour
Canberra
2010-10-12
$0
( 50)
Melbourne
2010-12-16
$400
(400)
Funding provided by m20100912.2
Brisbane
2011-01-24
$650
(650)
Funding provided by m20100912.2
Germany tour
Essen
2010-09-28
$0
(200)
Aachen
2010-10-04
$0
(120)
Room sponsored by sidux e.V.
Hamburg
2010-11-05
$0
(200)
Muenchen
2011-04-02
$136
(200)
Eur 137 Funding provided by Secure-U
Bonn
2011-06-08
$0
(120)
Room sponsored by Org assured Org
US tour
Washington DC
2011-06-18
$50
( 50)
room, covered by Jeff
New York
2011-06-20
$50
( 50)
ride, covered by Ian
Tokyo, JP Tokyo
2011-03-05
$0
(900)
downgraded to regular assurance event
- Co-audit thru regular assurance events: Eur 195 Funding provided by Secure-U
The ATE's with $0 costs was paid for the rides and/or accommodation by the individual co-auditors and speakers. There is no overview for their effective costs present. As an example: ATE Hamburg - 3 co-auditors traveled around 500 + 150 + 250 km's with travel expenses of approx 200 Euro. The room was sponsored by a local group. Approx. effective costs may vary from $50 upto $200 per near local ATE but may break the $500 barrier for long distance ATE's. eg. The planned ATE Tokyo (that has been downgraded to a regular assurance event) costs included at least a long distance flight and also accommodation, but hadn't been presented to the community.
 An optimistic approx rating over the effective costs for the above listed ATEs is approx $3.000, only $1.290 (43%) had been refunded, the rest was paid by the co-auditors, speakers and event organizers.
An optimistic approx rating over the effective costs for the above listed ATEs is approx $3.000, only $1.290 (43%) had been refunded, the rest was paid by the co-auditors, speakers and event organizers.
Co-Audit Summary and Analyse
The result is more than the Audit 2009 score in error rates. With about 37% error rate in missing CCA agreement checks and about 47, thats nearby a 50% error rate in any data checking on the CAP form (upto 3 errors tested) the overall result shows, that Assurance and Education area has a lot more to do, to train our Assurers, to educate them, to check more on at details. CCA agreement check error rate decreases once the Assurers attended an ATE. Non yet ATE attended assurers are more likely fail on the CCA agreement check. Also some relationship in ATE attendance and decreased error rate in data checking can be seen in the co-audits by country overview, that also lists the count of ATE attendance (2nd most right column).
As in the 2009 ATE series many old 35 pts assurers attended ATEs, in count of experienced- and senior assurers attended less the scheduled ATEs. We've more fresh new assurers on our ATEs (this also happened at ATE Tokyo, were from 16 attendees only 3 attendees had assurer state).
The co-audits in Belgium, France and the Netherlands were checks on the fly without an ATE (only 20%-50% attended an ATE yet).
 The high error rate for France can be argued with the language barrier. Most of the essential documents are written in plain English and with the well known resentiment with English language by native speaking French people - this can also be seen in CAcert's community activity by French members, the few that are active in the community are also understand English quite well, Arbitrations with French members often needs translation into French - one outcome maybe a translation campaign for the essential docs like the CCA translation project. But this needs resources by the local communities.
The high error rate for France can be argued with the language barrier. Most of the essential documents are written in plain English and with the well known resentiment with English language by native speaking French people - this can also be seen in CAcert's community activity by French members, the few that are active in the community are also understand English quite well, Arbitrations with French members often needs translation into French - one outcome maybe a translation campaign for the essential docs like the CCA translation project. But this needs resources by the local communities.
The other path to adjust the results is to push more on ATEs, not only in the well seeded countries, also in the less well seeded ones.
UlrichSchroeter
CARS
Assurance Team Report 2010-2011
The Assurance Team report covers the time starting mid 2010, where the co-audit season was opened.
2010-06-09-12
Assurance event at Linuxtag Berlin
2010-07-16
Faster Support Actions on requests by Assurers and Users
on Name Change cases, DoB changes after events Arbitration ruling2010-07-17
PracticeOnNames updated with the NL country variation
Arbitration ruling of a20090618.12.2010-08-21 + 22
CAcert assurance event at FrOSCon 2010
2010-09-27
New TTP-Assisted-Assurance to Draft - one more milestone in Policy!
2010-09-28
ATE-Essen
2010-10-04
ATE Aachen
2010-10-12
ATE Canberra
2010-10-01
The Big Masterplan to become Audit Ready
One of the essential topics that effects assurance:
co-audited assurances2010-10-31
Licensing our Documentation under CC-by-sa+DRP
This also relates to all policy documents2010-11-05
ATE Hamburg
2010-12-16
ATE Melbourne
2010-12-27 - 30
27c3 assurance event Berlin
2011-01-24
ATE Brisbane
2011-02-05 + 06
Assurance event at Fosdem 2011
2011-03-05
Assurances at Cebit 2011 without a booth
2011-03-05
Assurance event Tokyo (planned as ATE)
2011-03-26
Assurance event at Linux Infotag Augsburg
2011-04-02
ATE Munich
2011-04-09
New procedure for Name Change after Marriage w/ Assurance
Arbitration ruling2011-04-15
New Default Hyphen Rule - Arbitration ruling
2011-05-12
Assurance event at NLUUG at Ede, NL
2011-06-08
ATE Bonn
2011-06-18
ATE Washington
2011-06-20
ATE New York
2011-06-22
Assurance & Key Signing Party Stuttgart
Subpolicies work
TTP-assisted-assurance program
TTP-assisted-assurance policy has been voted to Draft 2010-09-13 by policy group vote p20100913. The following deployment that is needed to bring this policy start working started slowly and continues slowly: Documentation has started under TTP in the wiki. The deployment has been splitted into several tasks:
- - TTP users
- - TTP's
- - TTP Assurer (TTP-admin)
- - TTP TOPUP Assurer
- - Administrative tasks
One of the blockers is the ongoing discussion: "What is a by CAcert acceptable TTP?" and the 2nd essential blocker - the system implementation. As long the bugs bug #863, bug #864 and bug #888 are not fixed as long the TTP assisted assurance program cannot go online. The bug fixes is under the Software-Assessment project team task and is still in the work queue.
Find informations about acceptable TTPs for each country relates to the OA area, so therefor OA area is also involved into the TTP assisted assurance program deployment.
In current report period 0 TTP-assisted-assurances were made.
PoJAM assurances
The assurance subpolicy PoJAM has been voted to DRAFT 2010-01-19 in p20100119. PoJAM has been deployed with documentations in the wiki under PoJAM and with a section in the Assurance Handbook A parental kit has been deployed with an additional parental consent form that looks similiar to a CAP form that can be used by a Junior member to present the assurer in an assurance.
The topic "PoJAM" has been added to the ATE presentations to train our assurers.
Despite the fact PoJAM has now been deployed in practice, several reports received Assurance officer that this special assurance program has been used in practice, but there is no exact count of PoJAM assurances done available.
No reports received about Junior assurers until now.
From a couple of assurances from several events by different assurers the response is that this special assurance program works in practice. We've observed some Junior members at events who came with the signed parental consent form and we've also discovered that the assurers followed the procedure outlined in the documentation and presented in the ATE presentations. So to summarize: PoJAM has been deployed and is still working at least for the members part. My recommendation to policy group is to vote PoJAM to Policy.
The expectations to push the CAcert assurances program into schools and to encourage new young members hasn't been fulfilled right now. In the meanwhile there are some issues that moves this topic to organisation assurance area to do an OrgAssurance with schools and handle all assurances under the Organisation Assurance program.
Assurance: A Wider Purpose
 The Assurance program that follows AP has been advanced by AP to check also for the acceptance of the CAcert Community Agreement. the Assurance Policy therefor includes "A Wider Purpose!"
The Assurance program that follows AP has been advanced by AP to check also for the acceptance of the CAcert Community Agreement. the Assurance Policy therefor includes "A Wider Purpose!"
But this is not the only one issue.
The advanced "Assurance" also enhances CAcert Support by adding verification in a Password Recovery process or Name change after marriage. These processes have been ruled thru arbitration that assurers may assist Support in standard support issues by doing an assurance and gathering additional facts. This has been named "evidence gathering".
These cases have been announced thru blog and have been added to the ATE presentations.
Advancing Rules and Practices, Documentation
We have received several new updates on name issues that were documented under the PracticeOnNames that now has been incorporated under the Assurance Handbook.
A seashift has been reached by the new Hyphen-rule ruled by arbitration that simplifies the international handling of hyphens in names. Instead of handle each local hyphen rule individualy CAcert now has an international standard that assurers can follow:
- A hyphen in given names is to be treated as optional
In short: CAcert can not enforce every aspects of national laws and customs.
The 2009 Audit spotted a problem area in assurances with dates. 50% error rate in assuring dates has been picked up by the Assurance team, the Co-auditors team and the Education team, to find procedures to shrink this error rate. Within the ATE series of 2009 the training has discovered a decreased error rate down to approx 20% error rate. The 2010/2011 ATE series with a 3rd check on dates results in a reduction below 10% The result can be counted in reduced Arbitration cases with this issue regarding false DoB issues and also discovered in the latest co-audits.
This issue also shows the quality of service control mechanism that co-audits helps to make our services better, identifying problem areas, put these issues to the aganda of the Assurance, Co-audit and Education team, find a solution and rollout the solution in the ATE series.
Now, 2 years after AP has been rolled out to the community we observing an increase of country variations. One country variation that we've received thru a bug report is bug #920
- "error 'First and/or last names were blank.' conflicts with International Requirements (eg Indonesian Names (Givenname only))"
that clashes with current system implementation (system checks and requires both: givenname + surname)
With the Assurance event Tokyo beginning March 2011 an increase of non-EU seeding can be seen but its far behind the expectations. The TTP assisted assurance might be an option here, but this program is behind the schedule.
Assurer Training
Changes in the Assurance area has been announced thru blog posts and has been documented in Assurance Handbook.
ATE presentations have been updated with the new topics. The ATE presentations can be read in the SVN under https://svn.cacert.org/CAcert/Education/Material/ that follows a revision number.
New assurers gets trained by experienced assurers thru the "educated assurance" program. This program is not new, but gets named and documented: Assurance/Procedures/EducatedAssurance
The question wether educated assurances follows the co-audited assurances -or- the co-audited assurances follows educated assurances cannot be answered exactly, as educated assurances has been made before co-audited assurances started in spring 2009 and the wider purpose check in assurances started with AP and the AP rollout, but to conclude: the process is now documented by following our Principles of the Community
- We train our users. We train our users to train other users.
This concept has also found its way into the TTP assisted assurance subpolicy thru the TOPUP process. This process had been tested once thru a remote interview in a prospective co-auditors training.
Individual Assurances followed AP
From all the received events reports all assurances given followed Assurance Policy. All problem issues that have been reported in assurances had been transfered into arbitration.
So from AO's point of view, the Assurance Program follows all given policys. The AP rollout can be declared as finished so far.
Organisation-Assurance (Part 1)
OA administrative
The Organisation-Assurance program was in a mess starting mid of 2010. A few working Organisation Assurers worked under their existing policys but seeding new countries stalled. One question that blocked the OA's was the policy definition that new OAs needs a supervised training from 2 existing OAs before they might become OA. A request to become OA for Belgium started the discussion if the supervising OA must be from the country where the request comes from, or if other experienced OAs can supervise the prospective OA. The process to pass new Organisation Assurers can be answered in short:
- a prospective Organisation Assurer needs training thru 2 supervised Organisation assurances before he can be nominated by board motion
- the two supervising OAs does not need to be from the same country as the prospective OA. This means: all OAs also from other countries can do the supervising OA
Seeding Organisation Assurance in not yet seeded countries needs some more time as in this process also a OA country specific deployment needs to be started. This process may result in a new country specific OA subpolicy, but this process doesn't block any prospective Organisation Assurers in becoming OA in a new country.
By mid of 2010 the responsibility for the Organisation Assurance area was unclear. By default: all vacant officers roles are held by board. Organisation Assurance policy defines under 2.1 the "Assurance Officer" to be responsible for the OA program. In discussions with the Organisation Assurers an Organisation-Assurance-Officer has been proposed. So this open question was unhandled until May 2011.
Despite the fact this question was open till May 2011 AP referes under 0.3. Related Documentation - See also Organisation Assurance Policy (OAP) so that OA area is to be read that it is under AP control. In the discussion between Board, Organisation Assurers and Assurance Officer the Organisation Assurance Officers role has been defined to be responsible for the Organisation Assurance area. If this position is vacant it is filled temporarely by the Assurance Officer. This process finished in the nomination of Marcus Maengel as Organisation Assurance Officer with board motion m20110501.4
OA documentation
Starting with OA documentation review, I've discovered that there are several OA policy revisions around. The OA policy located under the main policy repository www.cacert.org/policy that is http://www.cacert.org/policy/OrganisationAssurancePolicy.php has been updated to https://svn.cacert.org/CAcert/Policies/OrganisationAssurancePolicy/OrganisationAssurancePolicy.html The policy decision p20080401.1 referes to the SVN revision to be the official OA POLICY that clashes with current revision under www.cacert.org/policy This needs to be handled by the new appointed OAO Marcus Maengel.
UlrichSchroeter
CARS
Organisation Assurance Report (Part 2)
Statistics by 2011-06-30

Country |
Total |
Jul 2010 to |
Running on |
AT |
18 |
2 |
|
AU |
9 |
|
|
BE |
2 |
|
|
CH |
18 |
1 |
|
DE |
112 |
7 |
8 |
DK |
1 |
|
|
FR |
6 |
|
1 |
HU |
5 |
|
|
IE |
3 |
|
|
IN |
1 |
|
|
IT |
1 |
1 |
|
LU |
1 |
|
|
NE |
1 |
|
|
NL |
22 |
1 |
|
PL |
1 |
|
|
RO |
1 |
|
|
SE |
1 |
|
1 |
UK |
2 |
|
|
US |
31 |
|
|
ZA |
1 |
|
|
Grand Total |
237 |
12 |
10 |
In the last reporting period, three new Organisation Assurers were appointed by the board: Andreas Albrecht, Andreas Bäß, and Marcus Mängel. Marcus Mängel was appointed as Organisation Assurer Officer in May.
12 organisations were successfully assured, 10 assurances were ongoing by the end of the period.
In June was a telephone conference of the German Organisation Assurers as preparation for a larger meeting in the next period to see how the organisation assurance can be managed in the future and assist to develop bootstrapping strategies in other countries.
As the Organisation Assurers should support the development of the TTP programme, there were many discussions with the Assurance Officer and Organisation Assurers to start the bootstrap for the US. It is aimed to finish the process during the next period so that the TTP programme can be enrolled step by step to CAcert deserts.
CARS Marcus Mängel (Organisation Assurance Officer)
Support Team

 The Support Team basically continued it's stabilised operations as reported in the beginning of the year
The Support Team basically continued it's stabilised operations as reported in the beginning of the year
Workforce
We had some more new additions to the Triage team, namely Fabian Knopf (who is now on the road to SE), Richard Trabing and Marc-Oliver Hofmann. Former Triage Team member Marcus Mängel has been appointed as Support Engineer and has done quite some work since then.
Team Meetings were held less often than we would have hoped for but posed a good opportunity to talk about issues that weren't immediate enough to be discussed on the mailing list but nevertheless needed discussion. The last meeting took place just a few days ago at the FrOSCon (in real life, yay).
As my personal focus has been shifting towards software development lately, I have sought to hand over team leadership of the Support Team. Joost Steijlen has volunteered to take over but that has not happened yet due to real life intervention. We hope to get this sorted out soon.

Operations
Our experience with the Password Recovery with Assurance has been very good. So good that on the last meeting the whole team expressed that we want to get rid of the old password reset procedure in favour of this more secure and overall improved procedure. The lost password questions will still be available but the procedure that was triggered when those failed, which involved relying on PayPal, some other dark magic, smoke and mirrors will be fully replaced by the Password Recovery with Assurance which relies on our network of Assurers to re-authenticate the user.
Since the end of last year the Support Engineers have handled 512 tickets. In addition to that there were more than 2738 emails classified as spam, 8051 non-delivery notices, out of office notices etc. (most of them handled automatically) and 639 tickets otherwise already handled by the Triage team. Unfortunately there were also some cases where things went wrong but the reaction was always very quick and transparent so not much harm was done.
We managed to keep response times pretty low. Most often under 24 hours until the users got the first reply.
The Todo List
 Here's a short review of the items of last report's todo list:
Here's a short review of the items of last report's todo list:
- Recruiting still stays on-topic
Marcus has worked on the documentation and worked with Bernhard Fröhlich from the Education Team to work out a "Triage Challenge" which is now available at https://cats.cacert.org and is intended to check the knowledge of Triage members after the initial training period
- Organisation Assurers have switched to OTRS
A software implementation of the Password Recovery with Assurance would still be very nice to have

- Handover of team leadership is still ongoing as mentioned above
- Response time has significantly improved
- It was very nice meeting most of the team on FrOSCon last week and also helped to resolved some social issues that faced
We managed to get some general rulings regarding name changes which allow support to act on their own if certain strict requirements are met, which takes some load from Arbitration and decreases the time until a issue can be resolved (the often proclaimed win-win situation)
Future to-do items will be determined by the upcoming Support Team Leader.
Michael Tänzer Support Team Leader
Spirit Team Report
