To AGM AGM - To AGM Team Reports - AGM TeamReports Overview - To AGM Members Reports - AGM Members Reports Overview - To AGM Members Report 2010 - AGM Members Report 2010
Team Reports 2010
Team Leaders are encouraged to present a report for their team.
Infrastructure Team Report 2010
Here is the infrastructure report for this year. Please consider that getting new infrastructure is important for getting our current infrastructure in a secure state and allowing for growth. Please find someone to replace me.
 CAcert Infrastructure Report 2010
CAcert Infrastructure Report 2010
The year began slowly. In January/February Brian Henson started and finished some major work to get a puppet centralised management ready for CAcert. Daniel Black did some planning to see what will be needed for CAcert in the foreseeable future. Some testing began with Ksplice as a mitigation for kernel vulnerabilities without having to reboot servers specificity virtual host servers.
February hit and the effects of CVE-2009-3555 SSL renegotiation started to hit as browsers broke a previously permitted behaviour. The previous approach of optional/mandatory client certificate authentication was on a directory basis which would require a SSL renegotiation. Some interim work was done to lists.cacert.org and community.cacert.org to require certificate authentication before a long term solution.
In March Mario Lipinski got restructured text working on the wiki.
 April, Andreas Bürki got a proposal together with a hosting provider that covers our current and future requirements and put it to the board.
April, Andreas Bürki got a proposal together with a hosting provider that covers our current and future requirements and put it to the board.
In May after a 3 month trial of KSplice the board approved to fund it for a year (m20100420.2). Thank you board. The gains of this in terms of uptime, security and lower sysadmin effort is much appreciated.
June saw some internal movements within BIT data centre. Thank you Wytze van der Raay for all the coordination and movement. Thanks also for getting all of our infrastructure services started due to our configuration problem.
Also in June, Jan Dittberner solved the CVE-2009-3555 issue. By packaging up a newer Apache version with SNI, using virtual hosting and certificates with subject alternate names we will be able to provide certificate authentication services, handle the idiosyncrasies of Safari, the poor error messages in Firefox.Jan also prepared a fully client certificate SVN server with client instructions.
June saw a new format of S/MIME message that our list software Sympa broke receiving. Daniel Black spent the time developing a workaround and filing an bug report in to fix this.
July saw the withdrawal of infrastructure offer after no decision was reached by the board before the end of June deadline.
Current state of Infrastructure:
Currently there are far too many VMs on Debian 4.0 Etch that finished security support on February 14 2010. Those that can be easily updated have been. A number of VMs have had adhoc packages installed that make an in-place upgrade is too risky an option with no reasonable blackout plan. The flexibility of the current managed gateway has made it undesirable to create and manage test VMs within the current for upgrading installations.
As indicated by Jan's recent work on SNI testing new opportunities exist for developing better client certificate based infrastructure services. Ideally this should be tested on independent VMs and a migration strategy deployed.
The ability to deploy new testing services is not conducive in BIT which is managed gateway designed around production systems. The hassle with organising accounts with the critical admin team, as helpful as they are, and the delays in Tunix firewall changes make this an unsuitable location for dynamic infrastructure.
In short - new infrastructure is needed to move existing services to a stable, secure and sustainable state.
Regarding specific services:
sun2 - the hosting machine is on Debian Etch and cannot be updated reliably without moving all the VMs.
wiki - on Debian Lenny. Looking for staff effort to migrate to a certificate auth and mitigate some spam.
Blog - on Debian Lenny. Fairly good state.
irc - is a mess of custom installed packages on what appears to be a Debian Etch host.
SVN - currently on Debian Etch - a new Debian Lenny server was prepared with full certificate authentication. Just needs to find a place to deploy to and then migration can happen.
bugs - on Debian Etch - not much effort/interest/investigation has been performed on this server.
lists - on Debian Etch - a number of custom fixes/packages are in place preventing an easy upgrade - particularly due to the criticality of the system. Volunteer effort for migration has been identified.
email - on Debian Etch - has a moderate amount of custom packages and configuration that will not survive and easy upgrade.
webmail/community.cacert.org - on Debian etch. Possibly upgradeable with some extreme care.  test2 - recently upgraded by Philipp
test2 - recently upgraded by Philipp
hashserver.cacert.org - abandoned service
translingo - Etch server of unknown state. Crudely working but internals are unknown.
CATS - Etch server. Class3 authentication is broken. Possibly upgradeable.
issue - Lenny server - working well and serving support teams well
logging - abandoned effort - logging achieved centrally using different mechanism.
forum - abandoned effort.
cod - documentation server - abandoned effort
emailout - working well as automated outbound services for wiki/issue tracking notices.
State of Staffing:
From a bulk recruitment that happened August last year only a few admins still remain. Some have formally resigned and others have faded from existence. While goals were set initially the crux of the problem is that flexible infrastructure is needed to deploy/test and migrate services. Daniel Black also resigned as a sysadmin due to lack of support in this area.
Recently some new volunteers have offered to prepare Sympa6 and Mediawiki services in order to update our existing list and wiki services hopefully correcting a number of outstanding feature request/bugs. Without hosting there will be no place to provide these services.
Of concern is community projects that host important CAcert services like the main CAcert test/development site and co-auditing. These are occurring without the benefit of having CAcert ownership, backup, and monitoring. With no infrastructure hosting to offer these community teams the community assets they build are at risk from technical, relationship and management failures and may eventually be lost to the CAcert community.
So looking to the future the infrastructure team hopes to find a donor of infrastructure services who is willing to work with the CAcert board. The board is urged also seek out new services and form contracts in a more pragmatic way. The need is great and new services will provide reliable hardware and hosting so our aging systems can be migrated, and reinvigorated, new systems can appear, auditing critical systems will become easier (and less hassle for the critical team) and our staffing volunteer effort can be utilised.
Daniel Black (former) Infrastructure Team Lead CAcert
Arbitration Team Report 2009-2010
Starting pushing Assurance Policy into the Community in February/March 2009 and the first Assurer Training Events (ATE's) in May/June 2009 starts a Arbitration backlog and sets Arbitration under fire. So summer 2009 there was a run to bring in new Arbitrators into the team:
- New Arbitrators starting August 2009
Thomas Bremer - m20090811.4
A new Dispute Resolution Officer (DRO) was appointed with motion m20090811.1 after Teus Hagen has left the Board and all his roles after SGM 2009-07-25.
Four new Arbitrators picked up the workload but could not prevent that the backlog increases. So a second run for new Arbitrators was started in November 2009:
- New Arbitrators starting November 2009
From the November run, two Arbitrators picked up the challenge to help the team. Ulrich Schroeter assists the new arbitrators in their first steps. The result was a training course for Arbitrators Arbitration Training Course that helps also other Arbitrators doing their work, to get their work structured.
In November 2009 there was a Support / Arbitration crisis. Arbitration could not work w/o Support, as Support is the first entry point of new dispute filings and also handles the ruling of most cases. The Support bottleneck has been identified and fixed in November/December 2009.
At the moment Support again comes to work, an additional backlog of Arbitration cases comes in and the overall backlog increases again.
Also the Dispute Resolution Officers (DRO) work comes under fire at the Boardmeeting 2009-12-20 with the motion "That, given m20090811.1, and today's informal information that some arbitrators are non-working, board requests an immediate update of the state and health of the Arbitration system from DRO, with a view to changing the roles and re-invigorating the process.". Motion m20091220.3 carried. The outcome was the resign of Nick Bebout as DRO at 2009-12-21.
In the Boardmeeting 2010-01-03 Board passed the motion m20100103.2 and appoints Lambert Hofstra as the new DRO. 
With the new Support team in place, one question araises about how to handle Delete My Account dispute filings. A mega IRC meeting with Arbitrators and Case Managers was announced for Monday January 4th. This IRC meeting started about 17:00 CET and ends Tuesday 0:45 CET. This meeting was the trigger for the recuring Arbitration Team Meetings that from now on are held 2 times a month. The meetings helps to identify problems, to exchange news that relates to Arbitration work, to form a team. An ongoing topic was the Arbitration backlog. The Arbitrators have many ideas about that, but not all yet could help to decrease the backlog.
About January / February 2010 Support moved to the ticketing system OTRS. New dispute filings flew in thru the Disputes Channel of OTRS. The Arbitrators team doesn't take much care about this move. So only about 2 Arbitrators could move new dispute filings from OTRS into the Arbitration queue. This first changed in June/July 2010.
In February / March 2010 Arbitration received 45 (!!) new disputes filings (see Statistics by Month below). This was probably too much to handle. The Arbitration work came to succumbs in March. For a period over 3 months no Arbitration cases were picked up, no Arbitration cases gets finished. First activity was seen again in June 2010.
Extensions to DRP

Arbitrators are appointed by Board motion. So the ongoing topic "How to remove inactive Arbitrators" raises the question, if Board is the audience to remove inactive arbitrators. That has been decided by board motion m20091206.2 Provision to remove arbitrators on advice of DRO - "The committee considers it has the authority to remove arbitrators, but resolves to only do so on advice of the Dispute Resolution Officer and after considering any written or oral submissions made by the arbitrator in question."
The next question that flews around the Arbitration team was: how gets DRO informed about inactive Arbitrators ? The Arbitration Team voted in the Arbitration Team Meeting 2010-04-06 for the "Inactive Arbitrators Procedure", so Case Managers, Arbitrators and Arbitration participients can inform DRO about not working Case Managers and Arbitrators. DRO has to contact the inactive Case Manager or Arbitrator and if he cannot find a solution has to report to Board, that Board can remove inactive Case Managers and Arbitrators with a board motion.
As a result of the Support Crisis November 2009, the DRP proposed procedure of picking up Case Managers from the Support Team has been moved to Arbitration Team. So Case Managers are now Arbitration Team members and every Arbitrator can now also be a Case Manager. But a Case Manager cannot be the Arbitrator in a case.
Arbitrated Background Checks
The Arbitrated Background Checks has been deployed within several ABC cases. The trigger was the Support crisis and the new Software-Assessment Project, that needs ABC'ed engineers. As there was no procedure defined before, it needs to be deployed. The basic procedure is outlined in Background Check Procedure. A list of questions circles between Arbitrators.
Forward Looking Statement
 There are plans to replace the OTRS - Mailing lists - Wiki - Email storage - tools with an Arbitration Management System that is under development by Philipp Dunkel to assist Case Managers and Arbitrators in Arbitration filing. by take into account the special requirements for privacy purposes and publishing of essential informations, to get a quick overview on each arbitration case (history log), and also over all arbitration cases (Arbitration queue) and the state of each arbitration case. Also there is a need to store the communications of each case.
There are plans to replace the OTRS - Mailing lists - Wiki - Email storage - tools with an Arbitration Management System that is under development by Philipp Dunkel to assist Case Managers and Arbitrators in Arbitration filing. by take into account the special requirements for privacy purposes and publishing of essential informations, to get a quick overview on each arbitration case (history log), and also over all arbitration cases (Arbitration queue) and the state of each arbitration case. Also there is a need to store the communications of each case.
For handle the arbitration backlog, there are plans to deploy template procedures for recuring administrative dispute filing cases like "Delete My Account", "Name change requests", "DoB errors", to handle such cases in a fast lane by ruling precedent cases.
A 3rd topic is the Appeal process. Currently that process is moved by Dispute Resolution Policy to Board. But this imbalances the forces of the three columns of power: Policy Group (legislative), Board (executive), Arbitration (judiciary). So there are some thoughts to build an "trial court" or "supreme court" with an Appeal procedure. This topic has been started by Ian as an open discussion, but hasn't finalized yet on Policy Group.
 There was some thoughts about a job ladder - to jump into Triage - undergo an ABC for becoming Support-Engineer - and an optional move into the Arbtration Team, starting as Case Manager - becoming Arbitrator, so all Case Managers and Arbitrators are also ABC'ed before becoming Case Manager and Arbitrator.
There was some thoughts about a job ladder - to jump into Triage - undergo an ABC for becoming Support-Engineer - and an optional move into the Arbtration Team, starting as Case Manager - becoming Arbitrator, so all Case Managers and Arbitrators are also ABC'ed before becoming Case Manager and Arbitrator.
Triage => Support-Engineer (ABC'ed) => Case Manager => Arbitrator
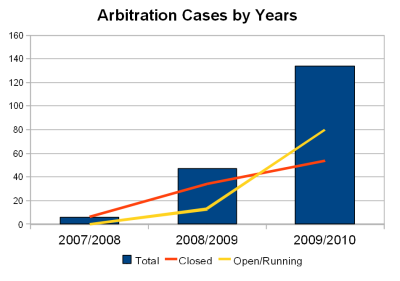
Statistics
- Statistics by Year (FY)
2009/2010
2008/2009
2007/2008
..
Total (2010-07-12)
Total
134
47
6
..
189
closed
54
34
6
..
98
open/running
80
13
0
..
91
- Snapshots total
closed
exec/init/running
total
2009-07-01
44
(?/?/?) 11
55
2009-10-30
50
(5/7/30) 42
92
2009-12-27
64
(4/24/21) 49
113
2010-04-01
85
(4/52/29) 85
170
2010-07-12
98
(4/63/24) 91
189
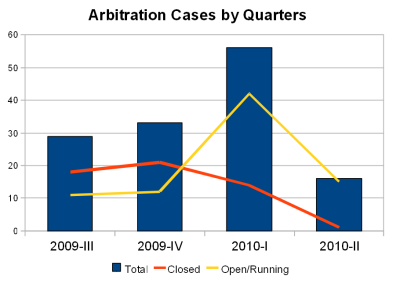
- Statistics by Quarter
2009-III
2009-IV
2010-I
2010-II
Total
29
33
56
16
closed
18
21
14
1
open/running
11
12
42
15
- Statistics by Month
closed
open/running/exec
total
Jul 09
6
7
13
Aug 09
7
2
9
Sep 09
5
2
7
Oct 09
1
0
1
Nov 09
12
10
22
Dec 09
8
2
10
Jan 10
5
6
11
Feb 10
7
16
23
Mar 10
2
20
22
Apr 10
1
5
6
May 10
0
6
6
Jun 10
0
4
4
Total
54
80
134
- compiled 2010-07-17 from
UlrichSchroeter
CARS
Software-Assessment-Project Team Report 2009-2010
In November 2009 the Software-Assessment Project team was formed to bring forward the Software-Assessment within CAcert. The Software-Assessment Project Team has also members that are not members of the Software-Assessment Team, as at this time starting the project, there was only one Software-Assessment Team member.
 The Objectives of the new Software-Assessment Project team is:
The Objectives of the new Software-Assessment Project team is:
- Build Testserver + Repository Server Image(s) (VM)
- Create Repository System
- Create Testserver (Environment)
- Build + Document Software-Patches Flow Process
- Test run: current webdb mirror, test Testserver Mgmt System, documentation
- Test run: current webdb mirror, add patches, document patches
- Test run: test patches, document test results
- Test run: bundle patches for a release for a transfer to critical team, documentation
- Build + Document Path Software-Assessment Team / Critical Team
- Build + Document Emergency Patches Path
The first meeting was the Essen Software MiniTOP 2009-12-16 followed by a second meeting in February Software MiniTOP Offenbach Feb 13th 2010. The project now has two project managers: Andreas Bäß for the technical part, UlrichSchroeter for the communcations part.
 The Software-Assessment Project Team pushed 4 new Software-Assessors Markus, Dirk, Alexander, Bernhard to become Software-Assessors, that results in the Board motion m20091220.2
The Software-Assessment Project Team pushed 4 new Software-Assessors Markus, Dirk, Alexander, Bernhard to become Software-Assessors, that results in the Board motion m20091220.2
Request to propose new Software Assessment team members That, the board is of the opinion that more software assessment members are needed, and, requests the Software Assessment Team Leader to propose new members (Dirk Astrath, Markus Warg, Bernhard Froehlich and Alexander Prinsier) for addition to the Software Assessment Team, and asks that ABCs be requested as soon as possible.
 The ABC's over Markus and Dirk has been finished. Both are nominated by Board motions to become Software-Assessors, so the Software-Assessment Team now has 3 members: Philipp, Markus, Dirk
The ABC's over Markus and Dirk has been finished. Both are nominated by Board motions to become Software-Assessors, so the Software-Assessment Team now has 3 members: Philipp, Markus, Dirk
The Critical Sysadmin Team deployed a mirror system on a discarded server machine that is currently hosted by Andreas Bäß in his office on a VM. This was also a test for the documentation of the production system for recovery purposes to rebuild the system as identical as possible. The deployed server VM will be used for running the new repository and the Testserver. Also a VM copy can be used by developers for installing it on their own machine for development purposes.
To bring the project forward, we held a weekly telco Tuesday evening 20 CEST with a system from the Community member Kees van Eeten. Its the same system that was used in a Board meeting run by Lambert and Bas.
 The next phase in Software-Assessment-Project deployment was to build a Repository. First tests with SVN failed the tests in merging. The alternate choice was to use GIT as the new repository system. Markus Warg deployed the repository with assistance from MichaelTänzer.
The next phase in Software-Assessment-Project deployment was to build a Repository. First tests with SVN failed the tests in merging. The alternate choice was to use GIT as the new repository system. Markus Warg deployed the repository with assistance from MichaelTänzer.
As the running testserver is under Software-Assessment Teams authority, testers needs an Testserver Mgmt System to control their accounts by adding assurances, adding special flags, so they are able to test patches. This needed a deployment of a Testserver Mgmt System. We decided to use a Zend framework with access to the testservers account database. MichaelTänzer wrote most of the scripts. The Testserver Mgmt System has been added to the repository too.
The Software-Assessment procedure deployment and documentation hasn't been finished yet. There exists a Description of Software Development Update Cycle (Proposal) but this needs been tested first. Documentation should be made on the Main Entry Info Page for Software Testers and test reports should be added to the Bug number presented on the overviews page in the existing bugs.cacert.org.
Currently, in August 2010, there is a run for building a Test team.
Software-Assessment-Project Team documentation website
UlrichSchroeter
CARS
Critical System Administrator Team Report July 2009 - June 2010
Signing server upgrade
 A major step forward in the past reporting year was the migration of the signing server to new hardware (a brand-new Dell rackserver acquired thanks to a financial donation from NLUUG to Oophaga). The new signing server was deployed in September 2009, and has been running flawless since in essence. This migration was motivated by a couple of power fail/reset problems with the old signing server hardware in June 2009. Since, for security reasons, the signing server can only be brought back up by physically visiting the hosting site, running it on long-lasting reliable hardware is essential for keeping the workload in hand for Oophaga Access Engineers and CAcert Critical System Administrators. A feature like dual (redundant) power supplies on the new hardware thus comes in very handy.
A major step forward in the past reporting year was the migration of the signing server to new hardware (a brand-new Dell rackserver acquired thanks to a financial donation from NLUUG to Oophaga). The new signing server was deployed in September 2009, and has been running flawless since in essence. This migration was motivated by a couple of power fail/reset problems with the old signing server hardware in June 2009. Since, for security reasons, the signing server can only be brought back up by physically visiting the hosting site, running it on long-lasting reliable hardware is essential for keeping the workload in hand for Oophaga Access Engineers and CAcert Critical System Administrators. A feature like dual (redundant) power supplies on the new hardware thus comes in very handy.
Relocation of all equipment
Another major physical effort was delivered on June 15, 2010, when we moved ALL CAcert equipment to another hosting room/rack in the hosting facilities in Ede, at the request of our hosting sponsor BIT. This was a concerted effort by two Oophaga Access Engineers and two CAcert Critical Sysadmins, and supported by a BIT engineer. As far as critical systems were concerned, the move went smoothly; however, there were a number of problems with getting the supporting and infrastructure systems all back up and running. A good learning exercise for all ...
Visits to hosting facility
 The log of visits to the hosting facility shows the following "on site" activities:
The log of visits to the hosting facility shows the following "on site" activities:
[10.08.2009] |
recover non-functional signing server (not hw, but sw!) |
[15.08.2009] |
signing server reboot (after power glitch) |
[11.09.2009] |
signing server migration to new hardware |
[18.11.2009] |
investigate condition of primary firewall hardware |
[19.11.2009] |
repair primary firewall hardware (power supply replacement) |
[21.01.2010] |
repair mirror firewall hardware (power supply replacement) |
[02.06.2010] |
inspect equipment in preparation for move |
[15.06.2010] |
move all CAcert equipment from BIT-2A to BIT-2B |
Remote system administration
All other system administration work has been performed remotely. Issues directly affecting the operation of the webdb server have neem logged to the cacert-systemlog@lists.cacert.org mailing list (archived at https://lists.cacert.org/wws/arc/cacert-systemlog ) with heading "configuration change webdb server", "security upgrades webdb server" or "cvs.cacert.org checkin notification".
OCSP server
A lot of work was done to investigate causes of the unreliability of the OCSP server, and some improvements were put in place. A more permanent solution will be implemented in the next months, by setting up a new virtual machine on the critical systems vm host, and deploying a newer version of the OCSP server software.
DNS infrastructure
By order of the CAcert board, the administration of CAcert's domain names and DNS was also brought under control of the Critical System Admin team in January 2010. A new virtual server ns.cacert.org was set up as the primary domain name server for cacert.{org,net,com}. It is supported by a number of CAcert-community-supported secondary servers, with zone transfers between them properly protected by TSIG. Preparations have been made for turning on DNSSEC support for all CAcert domains, the appropriate software has been installed and will be configured and enabled in the coming months.
Non-relocation of infrastructure services
It was hoped that the manageability and auditability of the critical systems could be improved by moving all (non-critical) infrastructure services out of the current hosting center to elsewhere in the latter half of the past reporting year, but it looks now like this is not going to happen any time soon.
Test server
We did invest quite a bit of time to help the Software Assessment Team with setting up a test server (on a virtual machine) which looks as closely as possible as the production webdb server. Scripts and documentation were written to accomplish this. Besides creating a usable test environment, this also served to strengthen our capability for (re-)building a new webdb server from scratch, documenting many hitherto obscure aspects of the current production server (which is essentially inherited from its original author, quirks included).
Forward looking statement
 Plans for the coming year include:
Plans for the coming year include:
- upgrade system software of webdb server to more current level
- move webdb server to better hardware
- setup new critical servers for ocsp and crl services
- deploy DNSSEC on the dns server
- improve database backup procedures
- rebuild the backup server
- expand the sysadmin team
Wytze van der Raay, Mendel Mobach, Stefan Kooman
Education Team Report

Education team has not been very active during the last year, the main activity consisted in maintaining the "CAcert Training System" (CATS).
In June a french translation of CATS has been started, but did not get finished till now.
CATS statistics
CATS is running quite stable. Currently a total of almost 4000 Assurers have passed the test. In 2009 a total of 424 certificates for passing the tests have been requested, including 41 printed certificates.
From July 2009 to June 2010:
- 4624 tests have been made
- 2438 tests had at least 80% correct answers and are therefor counted as passed
- 1804 different users (that is, different certificates used to login) have passed the test at least once
- 326 users tried the test at least once but don't have a successful test recorded
- On the average those who passed the test had about one (more exactly: 0.93) unseccessful tries before passing.
Future Prospects
Per definition education team should review, correct and extend existing education documents, as well as the CATS tests.
Some more specific things which should be done:
- Finish the started translations of CATS to dutch and french.
- Extend and update the pool of questions for the Assurer Challenge, especially in the area of Arbitration
Support the Arbitration Team in creating education materials for new Arbitrators (see the WiKi)
Support Event Organisation in improving and extending the present materials for ATEs (see SVN)
- There are occasional reports that CAcert's class 3 certificates do not work with CATS. This problem should be hunted down and fixed if possible.
- Improve the CATS admin interface so editing questions and answers is a bit more comfortable.
- Improve the CATS database structure and admin interface to give better support for handling questionaires in different languages
ATE / co-Audit Team Report 2009-2010
The Assurer Training Events (ATE) concept has been introduced Spring 2009. The first ATE ever happened was 2009-04-20 Innsbruck. In season 2009 till 2009-07-09 within 3 months, 14 ATEs takes place in 7 countries (7 DE, 2 NL, 1 AT, 1 CZ, 1 HU, 1 F, 1 UK).
The concept started by the needs of the Audit to audit the Assurers. Getting Assurers together, give them the informations they'll need to do their job with quality, to give informations what is essential about the Audit, is handled within the presentations part. The 2nd half is co-Audit.
From the experiences of these 14 ATEs the plan was to nail down the co-Audit plan (questions to be answered) and a system, to collect the infos from the co-Audits. The first plan was to start an Autumn 2009 tour, but caused by lack of resources this plan was defered to Spring 2010. Back in December 2009 at Assurance-MiniTOP Hamburg we've discussed, that we need documentations and the ATE thing structured. After AGM in January 2010 we've met at Fosdem Brussels with the Assurance-MiniTOP Brussels with defining what is a co-Auditor, what are the checks, how to collect the received infos, who tests the testers?. The results are in the MiniTOP minutes of Assurance MiniTOP Brussels Feb 6th 2010. Ian deployed a system that is hosted in Vienna. In a preview at MiniTOP Brussels we've added some requirements to the system, to allow tests not to complete, adding the level of experience of the test candidate and so on. At Assurance-MiniTOP Hannover at Cebit, we finalized the ATE and Co-Audit concept for this years season. Presentations that have to be added: PoJAM, Privacy. The set of co-Audit questions.
One plan that starts end of 2009 was to spread over Europe - Denmark, Sweden, Poland, Belgium, UK, France, Spain, Italy. All attempts to find contacts and Assurer groups in each of above listed countries failed (except Belgium and Sweden). The proposed ATEs Bilbao (E) (July 2009) did not happen, but another ATE in December 2009 ATE-Goteborg (S) did. The plan was for Fosdem Brussels, to find contacts to these countries. In practice, the result was disillusioning. We've got contacts to individuals but no Assurer groups. So the expected push did not happen and the run for ATEs in Germany and the Netherlands did not happen caused by lack of resources. The only ATE that was held was ATE-Sydney in March 2010. So the complete ATE season was defered to Autumn 2010.
The CAcert Assurer Reliable Statement (CARS) became an essential tool in gathering the evidence over the co-Audit results to present a future Auditor. We've first discussed this tool at Assurance MiniTOP Munich. First Arbitrators used this tool in 2009 to gather the evidence in Arbitration cases from the Assurers in practice. Later, the CARS moved to AssuranceHandbook2 as part of the Assurance process. Each statement an Assurer gives in an Assurance is also a CARS, that signals to the community, my result in the Assurance is a reliable statement you can rely on. The concept of reliance we have with the certificates. You can rely on my statement, if I add my certificate onto my email and I'm bound to the Arbitration system with the Dispute Resolution Policy. So the CARS is similiar to the digital certificates in the electronic world, so the CARS is the analogy to the analog world, where I have to send reports, results over a co-Audit. So therefor each result set that is entered into the co-Audit application is also a CARS statement made by the co-Auditor to the community and probably later to a future auditor. You can rely onto my entered results. These results are verifyable. With this method at hand, the co-Audit results becomes "acceptable" to an Auditor. The evidence over co-Auditor results vs. Auditor results has been checked in the Spring Tour 2009 and presented at Assurance MiniTOP Munich. There was no difference in testings by the Auditor and the co-Auditors so the process of co-Audit has been tested and checked to be useful in the overall Audit plan.
UlrichSchroeter
CARS
Assurance Team Report 2009-2010
The Assurance Team Report covers the time starting May 2009. At Assurance MiniTOP Munich 2009-05-17 the team was built up. The main task: Audit over Assurance. The team prepared together with the Education team the practicle ATE presentations for Assurers.
- 2009-05-17 Assurance MiniTOP Munich - co-Audit results presented
- 2009-04-20 First ATE Innsbruck - push of Assurance Policy to the Community
- 2009-12-14 Assurance MiniTOP Hamburg - proposals PoJAM, TTP-Assisted-Assurance, Nucleus
- 2010-01-03 Assurance Plan for 2010 (ATE's) presented at Board Meeting
- 2010-02-01 p20100119 PoJAM to DRAFT resolved (Policy on Junior Assurers / Members - Subpolicy to Assurance Policy). This is the first policy in a series of subpolicys under AP, that cames back after all special assurance programs becomes frozen.
- 2010-02-06 Assurance MiniTOP Brussels - co-Audit season 2010 prepare: Co-Audit, Defining the Co-Auditor, co-Audit Team, co-Audit preparation
2010-02-21 Sebastian Kueppers resigns as Assurance Officer, UlrichSchroeter appointed as new Assurance Officer.
2010-03-03 Assurance MiniTOP Hannover - Co-Audited Assurances Program finalized and starts at CeBIT 2010
- 2010-03-24 First ATE in 2010 season
- 2010-06-14 New Password Recovery w/ Assurance Procedure has been introduced by an Arbitration case that relates to the Assurance area. In this procedure Assurers assists Support in resolving the Password lost problems with a regular assurance and addtl. tasks to help the Community members to access their accounts again.
Subpolicies work
 After AP cames to DRAFT all special Assurance programs has been frozen. On Events Assurers runs into the problem with Underaged cases, TTP Assurance program was not announced to be frozen. So from within an Arbitration case also this program gots notification to Community, that it is frozen. Also the Super-Assurance program conflicts with the AP. So therefor we've started the Assurance-MiniTOP Hamburg mid of December 2009 to find solutions in prepared subpolicys and thoughts about the special Assurance programs.
After AP cames to DRAFT all special Assurance programs has been frozen. On Events Assurers runs into the problem with Underaged cases, TTP Assurance program was not announced to be frozen. So from within an Arbitration case also this program gots notification to Community, that it is frozen. Also the Super-Assurance program conflicts with the AP. So therefor we've started the Assurance-MiniTOP Hamburg mid of December 2009 to find solutions in prepared subpolicys and thoughts about the special Assurance programs.
PoJAM
Assurers who passes the CATS test remember about the question, if Juniors can be assured. The correct answer: Yes, if they'll can be verified with an official ID document. After AP was pushed into the Community beginning 2009, at each event at least one Junior asks for an Assurance. So here Assurers are in a conflict: CATS test says, yes, you can assure Juniors, AP says, member has to agree to the CCA and to be bound into Arbitration. So this may conflict with local laws. An attempt was made with a PoJAM proposal at Assurance MiniTOP Munich May 2009. But this WIP had a disadvantage regarding parental consent. A guardian has no legal rights in a dispute filing case nor can he fully take the liablity over a Junior member. So this concept was void. With the new PoJAM proposal release, the liability is focused onto the parental consent. The trick in this new concept is: if once parental consent is established, this can be presented to all other Assurers with a parental consent form. Assurer has to make a note on the CAP form, that parental consent has been verified. Problem solved.
PoJAM subpolicy has been pushed to DRAFT end of January 2010. So its now binding to the Community.
TTP-Assisted-Assurance
With AP to DRAFT CAcert looses all special Assurance programs, to bring in new members from CAcert deserts. CAcert's grow is in danger. So the run has started to write new subpolicys to make the old special Assurance programs AP conform, With Policies in effect, these special assurance programs may be re-opened.
The first attempt is the TTP-Assisted-Assurance program. The proposal was written at Assurance-MiniTOP Hamburg, December 14th, 2009. The discussion in Policy Group started February 2010, after PoJAM has been pushed to DRAFT. The first results are included into the proposal. But this concept had one disadvantage: With two TTP-Assisted-Assurances a new member can gain 70 Assurance Points. But cannot become an Assurer by his own. This forces a new concept: The TOPUP. This allows members in the deserts to become potential new Assurers, as they have now an option to reach the 100 points level barrier.
Also new in the TTP-Assisted-Assurance subpolicy is that the task verifying TTP-Assisted-Assurances has been moved back into the Community by defining Senior Assurers as TTP-Admins. A definition of Senior-Assurer has been added onto Assurance Handbook.
By writing this report, TTP-Assisted-Assurance subpolicy has been pushed for call for vote into Policy Group. So probably this subpolicy become DRAFT end of September 2010.
Nucleus Assurance Program
The Super-Assurance program conflicts AP in full. AP limits the Assurance points to a level of 35 pts (50 pts max). All special Assurance programs are bound to this limitation. Also the Super-Assurance program.
This raises the question, how we can bring in new members easily, w/o Super-Assurers program ? From the experiences with Assurer groups, together with a mathematical experience, a group of potential Assurer candidates needs at least 10-12 candidates, who are interested in becoming Assurer.
With experiences of the training concept we've made in ATE's, we can push a group of members upto Assurer level in an area. This concept honors the AP limitation of 35 (50) Assurance points. So it can be seen as a replacement for the old Super-Assurance program. At the end of the process, a group of Assurers with at least 20 experience points each can seed a CAcert desert area with enough Assurers at this area. To find new potential Assurer candidates will be the most intersting question. So the focus is to find other OpenSource communities in an area that we can ask running this program.
Also thoughts about combining TTP-Assisted-Assurance program with the Nucleus program were made, but has been stopped, to allow at least one of these special Assurance programs to pass Policy Group.
The Nucleus Assurance program needs to be written as a subpolicy first. As it is a concept to replace the old Super-Assurance program it is included in this report, to signal to the Community, yes, there is progress in this area in finding replacements of the old special Assurance programs.
Updates on Handbook, Practice documents
With new subpolicies at hand, with rulings from Arbitration group regarding Assurance specials, my task was to implement the new details into Assurance Handbook, review the PracticeOnNames, PracticeOnIdChecking documents. A parental info package has been deployed regarding new PoJAM subpolicy. All you can find in Assurance Handbook.
Starting pushing AP to the Community, Assurers takes care about name mismatches in accounts. This raises dispute filings to the Arbitration group after the ATE series 2009 by stricter name rules. This also raises the Dutch short givenname variation problem. Arbitration ruled, that the Dutch short givenname variation has to be categorized as a country variation as defined under AP 2.2. So this opened a new variation to the strict rules as known and presented in the ATE 2009 series. This ruling has been added into PracticeOnNames. The new ATE series presentations needs to add this as a new section to push this info to the Community. At time of writing, the ATE series 2010 presentations are under preparations.
The Arbitration group has introduced new Assurance practice procedures to assist Support and Arbitration with procedures w/ Assurance like the Name Change Request w/ Assurance or Password Recovery w/ Assurance. These procedures are enhancements to the Assurance process at a Face-2-Face meeting to collect additional infos from the Assurers and Assuree, so that the original request by Support or Arbitration can be passed easily. As these procedures are quiet new, they had not been added to Assurance Handbook yet. Documentation to the new procedures can be found in the Wiki on Password Recovery or Arbitration precedents cases.
I've reviewed PracticeOnIdChecking (PoIDC) against AP. The old tool with 100 points conflicts with the Assurance Points concept as it totaly confuses Assurers who read that concept. So therefor this has been removed and PracticeOnIdChecking has been rewritten. There is an ongoing discussion wether confidence in an Assurance statement is a black/white or a grey view. AP states the grey view: less points if less confidence, ZERO points if ZERO confidence, If Negative Confidence then collect the evidence, file a dispute.
Assurance Events
 Many of Assurance events that were announced thru Upcoming Events wiki page, signals lacks report. As I'm attended many of these events, I can confirm for these events, that the Assurances made on these events were conducted by Assurance Policy. In problem cases disputes were filed. The shift from old CAcert days to the new CAcert days has finished, starting with the ATEs, Assurers becomes trained, the CAP forms from CAcert's website now are AP conform, Assurance Handbook and the Practice documents now becomes living documents that are read by the Assurers. Co-Audits at regular Assurance Events the first half of 2010 shows a significant count of Assurers not attended an ATE before. The co-Audit results have a significant higher error rate in comparison to Assurers that attended an ATE before (see table 1). So this leads to the conclusion, that the ATE program is an essential program in the Audit process, to get the Audit passed over the RA part.
Many of Assurance events that were announced thru Upcoming Events wiki page, signals lacks report. As I'm attended many of these events, I can confirm for these events, that the Assurances made on these events were conducted by Assurance Policy. In problem cases disputes were filed. The shift from old CAcert days to the new CAcert days has finished, starting with the ATEs, Assurers becomes trained, the CAP forms from CAcert's website now are AP conform, Assurance Handbook and the Practice documents now becomes living documents that are read by the Assurers. Co-Audits at regular Assurance Events the first half of 2010 shows a significant count of Assurers not attended an ATE before. The co-Audit results have a significant higher error rate in comparison to Assurers that attended an ATE before (see table 1). So this leads to the conclusion, that the ATE program is an essential program in the Audit process, to get the Audit passed over the RA part.
Table 1: Result from 54 co-Audits (2010)
country |
# errors |
ATE |
EP |
|
|
% att. |
0-50 |
DE |
1.4 |
26 |
32 |
NL |
1 |
0 |
29 |
FR |
4.2 |
20 |
16 |
BE |
4.5 |
0 |
7 |
AU |
0.8 |
100 |
22 |
 Table 2: Results from Audit presentation at Assurance MiniTOP - Munich 20090517
Table 2: Results from Audit presentation at Assurance MiniTOP - Munich 20090517
country |
# errors |
ATE |
EP |
|
|
% att. |
0-50 |
AT |
0.44 |
? |
|
CZ |
1.00 |
100 |
|
DE |
0.88 |
100 |
|
FR |
1.63 |
? |
|
HU |
1.67 |
? |
|
NL |
1.88 |
0 |
|
UK |
1.78 |
? |
|
The core Assurance Team: Ulrich, Joost, Ian, Dirk, Ted and Sebastian
UlrichSchroeter
CARS
Events Team Report 2009-2010
In the FY 2009-2010 we had 52 Assurance Events in total, 4 of them were announced as ATEs.
Year
Months
Count
ATEs
did not happen
ATEs not happened
Reports rcvd
2009
07-12
32
3
7
1
6
2010
01-06
20
1
0
0
4
Total
2009-2010
52
4
7
1
10
So in total 45 Assurance Events takes place with 10 Event reports received (20-25%).
 Assurance Events by Countries:
Assurance Events by Countries:
Country
2009
2010
DE
20
12
NL
5
2
CH
2
1
US
1
2
E
2
F
1
S
1
AU
1
B
1
DK
1
Total
32
20
Event Reports
The Events Reports problem ... Starting Audit over Assurance back in Spring 2009, Auditor requested to bring in an Event report for each event that takes place with a statement from the Events Organizer, that all assurances conducted by Assurance Policy. Me as Events Team Leader, I've requested the Events report for every passed events. Sent reminders over reminders ... nothing happened. So here, the support from Community wasn't that great as expected. Andreas Buerki created a Events Report template, that I've sent around by requesting the Events report. But also this doesn't helps to get in more event reports. I've introduced the signaling of received event reports to the Past Events wiki site, but it doesn't helps to bring one more event report in. Probably a minimalistic Events report - request for a statement that all Assurances were conducted by AP from the Events Organizers - will help to get better results.
Cross Community Work
Autumn 2009 a push on Cross Community Work started with other groups from with the OpenSource Community.
Invitations for events are shared as on OpenSource events, often the same people, the same communities attends.
- CAcert presentations were organized on demand.
Other Community Groups with relations to CAcert: OpenSource-Treffen, OpenOffice, Unix distributions like Sidux only to name some.
With the relation to other OpenSource groups we can share the work on booths, we can bundle the resources. E.g. if we have not enough Assurers for a booth we can build a network of Assurers at an event like Linuxtag. "Sorry, we can't give you currently the full 100 points, but you can visit the booths of Sidux, OpenOffice and Ubuntu, and you'll find more Assurers there"
With the Client Certs presentation, we've started a Cross Community push to other OpenSource communities, to think about Client Certs usage in their software.
Support on Events
There is a big support from the Community for Events.
- Wiki pages assists Event Organizers in managing events and to find Assurers who helps on the booth.
- Often Events were announced also thru blog posts.
With the Arbitration precedents case a20090525.1 "Event officer request recurrent notification to assurers near the location of the following ATEs" a scripted maiiling procedure has been implemented, that assists Event Organizers to contact Assurers near their location. This scripted mailing has been used several times (6x 2009, 4x 2010) for event organizing or for event announcement (2540 recipients sent emails out, approx 254 per mailing). The overall result was a success as Event Organizers found assistance by Assurers or people comes to the Events.
- The usage of Event templates assists Event Organizers with a checklist, what they'll need on a booth.
Big Events
FOSDEM and Cebit planning started Autumn 2009.
FOSDEM 2010
For FOSDEM we've tried to find contacts all around Europe 'cause Fosdem is a European conference. We got some contacts, but it was far behind what we've expected. The Event by itself was a great success. Ian presented a talk about Client Certs - The Old New Thing. This presentation we've presented also on other Events in Germany (DA-Treff, Linuxtag, mrmcd). The goal to find Assurer groups in other countries did not happen. We've met individual Assurers, but did not find any bigger group.
At Fosdem 2010 the Assurance core team held Assurance MiniTOPs about co-Audit to prepare the co-Audit season 2010.
Cebit 2010
Cebit 2010 attendance was tried to get a sponsored booth thru Linux-New-Media. Alexander Bahlo assists us in the paperwork, to write a Call-4-Participation with success. Linux-New-Media offered OpenSource projects a sponsored booth for 12 projects. 65 projects sends their application. A jury selected the best 12 projects. CAcert was one of the 12 selected.
Two topics on the Cebit agenda:
- Find contacts to Assurers and Assurer groups - worldwide
- Finishing the co-Audit preperations for season 2010
We've got some contacts from Italy, Spain, South-America, but these were only individuals with no strong CAcert support in their local areas. So the plan to push Assurer groups for a Nucleus didn't happen.
The 2nd topic, the finishing of co-Audit preperations for season 2010 has been successfuly finished. We have the documentations in place. We have a system up and running to collect the co-Audit results and started the first co-Audits.
Assurances were made following PoJAM that moved to DRAFT end of January 2010. So here we had another success in practice with a new subpolicy in effect.
Push AP to Community
The push of AP into the Community could be concluded as a big success, since started early 2009. At all bigger and smaller events Assurance now were conducted by AP. Assurers takes care about the Assurance statement, to not only check identities, also to check the Assurees to be bound to CCA and also bound into Arbitration.
Change in Events Team Leader role
Back in 2009 I took over the Assurance Officers role by pushing several new subpolicies. I've also handled the practice documents. Also active as Arbitrator, we've discussed the role of Events Team Leader and started the search for a new Events Team Leader, we've found in Walter Gueldenberg, who also handles the Events management for the Sidux-EV, a Debian derivate. The change in Events Team Leader role changed 2010-03-27 by board motion m20100327.1 New Events Team Leader
UlrichSchroeter
CARS
Support Team
 After the disruptions from last year Support had pretty smooth operations this year. The Support Team is constantly building up to cope with the daily operations.
After the disruptions from last year Support had pretty smooth operations this year. The Support Team is constantly building up to cope with the daily operations.
Workforce
In the beginning of 2010 Ian Grigg stepped down from his role as Temporary Support Team Leader and Michael Tänzer became new Support Team Leader.
After some nasty incident we lost one of our Support Engineers but have been able to steadily gain more man power. New Support Engineers have been appointed (Joost Steijlen and Dominik George) and even more Triagers have been added to the Team. Although we have been adding up there is a drop out rate and we need to continue recruiting more people to shorten the response times.
 Just recently we had the first of what we hope to be recurring series of meetings to discuss issues that have come up and do a little bit of team building.
Just recently we had the first of what we hope to be recurring series of meetings to discuss issues that have come up and do a little bit of team building.
Operations
We have been getting more and more comfortable with our issue tracking system OTRS and have updated some of our documentation accordingly.
Password recoveries are the lion's share of requests that get to the Support Team (apart from spam ![]() ) and as noted in last year's report they are time consuming, cumbersome, complex and come with risks. In joint effort with our liaison from the arbitration team Ulrich Schroeter we therefore developed the Password Recovery with Assurance which uses our network of Assurers to re-authenticate the user. We hope that some day this will be implemented in software so we can concentrate on the rest of the cases (which is still enough to deal with).
) and as noted in last year's report they are time consuming, cumbersome, complex and come with risks. In joint effort with our liaison from the arbitration team Ulrich Schroeter we therefore developed the Password Recovery with Assurance which uses our network of Assurers to re-authenticate the user. We hope that some day this will be implemented in software so we can concentrate on the rest of the cases (which is still enough to deal with).
 In the last year over 587 issues have been handled by our Support Engineers (that number doesn't include the requests that never made it through Triage or were forwarded to Arbitration) and each issue accounts for the whole conversation between Support and the user on that specific case (thus possibly many replies). There were days where we had a long backlog of more than two weeks but all in all we managed to get by.
In the last year over 587 issues have been handled by our Support Engineers (that number doesn't include the requests that never made it through Triage or were forwarded to Arbitration) and each issue accounts for the whole conversation between Support and the user on that specific case (thus possibly many replies). There were days where we had a long backlog of more than two weeks but all in all we managed to get by.
The Todo List
One can say that we have progressed on all our items on last years todo list and even completed some of them:
- Recruiting obviously remains a major topic for the Support Team
- We have updated parts of the documentation but other parts still need to be refurbished. The idea of the Support Challenge has lacked some attention lately
- Migration to OTRS has been completed. Some issues as enabling client certificate login and S/MIME encryption support still need to be solved though (S/MIME support needs a fix in OTRS which will hopefully be solved next year by the OTRS people).
- Apparently OTRS doesn't seem to be suited for Arbitration and the Organisation Assurers want to keep using their mailing list for the time being
As mentioned the Password Recovery with Assurance has been developed and deployed as a manual procedure, a software implementation would be very feasible.
 New items that are added to our todo list for next year:
New items that are added to our todo list for next year:
- Hand over Team Leadership as I will be more involved in the Software Assessment Team
- Try to get a more constant response time (how we can do that remains an open question – maybe through shifts)
- Do more team building to fight the lone warrior effect
- Work together with Arbitration to get more General Rulings that allow Support Engineers to act without a previous Arbitration when certain conditions are met. This a) gives the user a shorter time to completion b) takes load from the Arbitration Team
Michael Tänzer Support Team Leader
Spirit Team Report
 In the last period of CAcert's 2009/2010 business year, a need for a new team arose and caught the eye of Martin Gummi and Dominik George. In the course of some rather unsatisfying incidents at CeBIT 2010, decisive action was taken by Dominik George in order to re-establish trust in a young assurer who had to face serious problems within the community beforehand-
In the last period of CAcert's 2009/2010 business year, a need for a new team arose and caught the eye of Martin Gummi and Dominik George. In the course of some rather unsatisfying incidents at CeBIT 2010, decisive action was taken by Dominik George in order to re-establish trust in a young assurer who had to face serious problems within the community beforehand-
The aftermath of that brought up the idea of founding a new team dedicated to the entire community aspect of CAcert. A concept was created and board signaled their good-will for letting us run an experiment within the German community.
Points listed in this concept include, but are not limited to, assurer assistance under arbitration (as defined in DRP), general care for fellow community members and organisation and observation of social events.
The team has not started any real work yet, but is planning on compiling a team of volunteers who tend to show a more-than-average interest for the mentioned aspects.
Martin Gummi and Dominik George have instated themselves as temporary team leaders in order to develop the idea and start a vote once the group has grown. Arbitration a20100304.1 mentions the Spirit Team as a potential means for establishing assurer assistance under DRP.
