česky | english
Glossary of terms for validation, derived from Mozilla's Glossary
Validations in Relationship
Rough relationship:
Old Class |
|
Individual |
Organisation |
Check conducted |
III |
|
? |
EV |
"Extended" |
II |
|
IV |
OV |
Basic Identity |
I |
|
AV |
DV |
Simple control |
Purpose |
S/Mime, login/auth |
HTTPS, code-signing |
|
|
Notes:
- It is probably unreliable to claim much clear tightness in any relationship as described above.
- the horizontal relationship between Classes 1,2,3 and the DV/OV/EV concept is not documented, it is just indicative.
The separations reflect many influences from commercial forces, history and structural re-adjustments (c.f., 5 forces) by various players on the supply side.
- As such they may not be desirable to an open, free community CA such as CAcert which is more focussed on demand-side.
Glossary
AV (address validation). Verification of the control of an email address of an email account, only. Intended for certificates issued to individuals (assumption) for use with S/MIME email.
For example, the owner of the "janedoe@example.com" address could obtain an AV certificate for that address based on her demonstrating to a CA that she owned or controlled the email address in question. Typically, this is done by responding to email sent to that address.
- Such certificates may be referred to as address-validated or AV certificates. Note that "AV" is not a common industry term, but is newly-coined by Mozilla as an analogy to the widespread "DV", "IV", etc, terms. Some people use the term "DV" loosely to cover this case, but arguably it deserves a term of its own.
More formally, Mozilla may define: AV certificates as certificates containing an emailAddress attribute or Subject Alternative Name extension with a value (or values) apparently corresponding to an RFC 822 email address, for which the CA makes claims (e.g., in the CPS) that it has in some way validated that the address in question is owned and/or legitimately controlled by the certificate subscriber, and for which the CA makes no claims as to the validity of any individual identity stored in the Common Name attribute of the certificate.
DV (domain validation). Verification of the control of a domain. Intended for certificates for SSL/TLS-enabled sites.
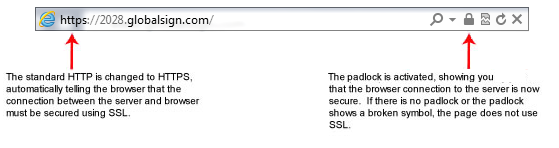
- For example, the owner of the "example.com" domain could obtain a DV SSL certificate for "www.example.com" based on her demonstrating to a CA that she owned or controlled the domain in question, e.g., by responding to email addresses sent to an email sent to the administrative contact listed in the whois database for that domain.
- Such certificates are informally referred to as domain-validated or DV certificates.
More formally Mozilla may define: DV certificates as certificates containing a Common Name (CN) attribute or Subject Alternative Name extension with a value (or values) apparently corresponding to one or more actual Internet domains, for which the CA makes claims (e.g., in the CPS) that it has in some way validated that the domain(s) in question are owned and/or legitimately controlled by the cert subscriber, and for which the CA makes no claims as to the validity of any organizational identity stored in the Organization attribute of the certificate.
EV (extended validation). EV certificates are certificates that are validated according to the guidelines laid out in "EV SSL Certificate Guidelines" published by the CA/Browser Forum.
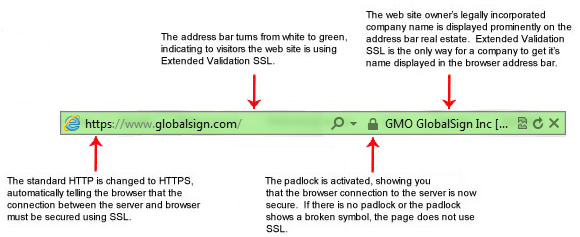
- EV certificates can be considered to be a special subset of OV certificates, but in practice, CA/Browser Forum makes a distinction that OV implies not EV.
IV (individual validation or identity validation). Verification of an individual or an individual's identity. Intended to support issuance of email, SSL/TLS client authentication, and other uses for individuals rather than organisations.
- These are commonly referred to as IV certificates. Note that some people use "IV" as a synonym for "OV" when referring to certificates issued to organizations. However it's arguably more clear to use "IV" to refer only to certificates issued to individuals.
Note that an IV certificate could also contain an email address in addition to the individual identity information. Mozilla policy requires that email address to be validated to the same or greater degree as for an AV certificate. This opens the question as to whether there is a standards difference involved between AV and IV, or just another thing to check.
More formally Mozilla may define: IV certificates as certificates containing a Common Name (CN) attribute with a value apparently corresponding to an actual named individual, for which the CA makes claims (e.g., in the CPS) that it has in some way validated that that value corresponds to the individual identity of the certificate subscriber.
OV (organization validation). Verification of an organisation. Intended to support and provide information for certificates issued to organizations (including corporations, government agencies, NGOs, etc.) for SSL/TLS-enabled sites, code signing, and other uses.

- These are informally referred to as organisation-validated or OV certificates. Note that CAcert also applies this general process to certificates issued to individuals within organisations, a distinction not recognised above.
- Mozilla policy may require as a verification standard that the applicant is required to supply some sort of evidence that they are authorised to act for the organisation in obtaining the certificate.
Note that an OV certificate could also contain one or more domain names. Mozilla policy requires those domain names to be validated to the same (or greater degree) as for a DV certificate. Ditto remarks above on standard.
- Note that EV certificates are a special subset of OV certificates for which the CA performs the validation according to an written standard in the EV Guidelines. However in practice, browsers and CA/Browser Forum attempt to make a distinction between OV and EV certificates, and want to treat them as distinct and separate certificate types. To them, "OV" implies "not-EV".
More formally Mozilla may define: OV certificates as certificates containing an Organization (O) attribute with a value apparently corresponding to an actual organizational entity (i.e., as opposed to a value like "Not validated"), for which the CA makes claims (e.g., in the CPS) that it has in some way validated that that value corresponds to the organizational identity of the certificate subscriber.
