česky | english
How to generate a new P12 formatted certificate with CAcert's browser application
The web application is located here. It can be used in any browser. The result is a file in the P12 (PFX) format, which can be imported into the same or other web browser or Windows OS.
The procedure is completely straightforward and is described directly in the application.
First, two new RSA keys (private & public) and a Certificate Signing Request (CSR) are generated.
- Then it is necessary to "jump" to the Cacert website to transfer the generated CSR there, add requests (Email addresses, name, and/or other), and wait for the answer - certificate,
- then transfer the new certificate back to the application, where a P12-formatted file will be created.
- That P12 file contains CAcert roots, your new certificate and your new private key that must be encrypted with a password, which you have to create and enter.
- You can then download the finished file to your computer. Then you can import it into a browser or OS (Windows).
|
Detailed procedure
1. Generate CSR, private and public key
After start, the application start page will be shown. There is a resizeable CAcert logo, application name and the progress bar in the header.
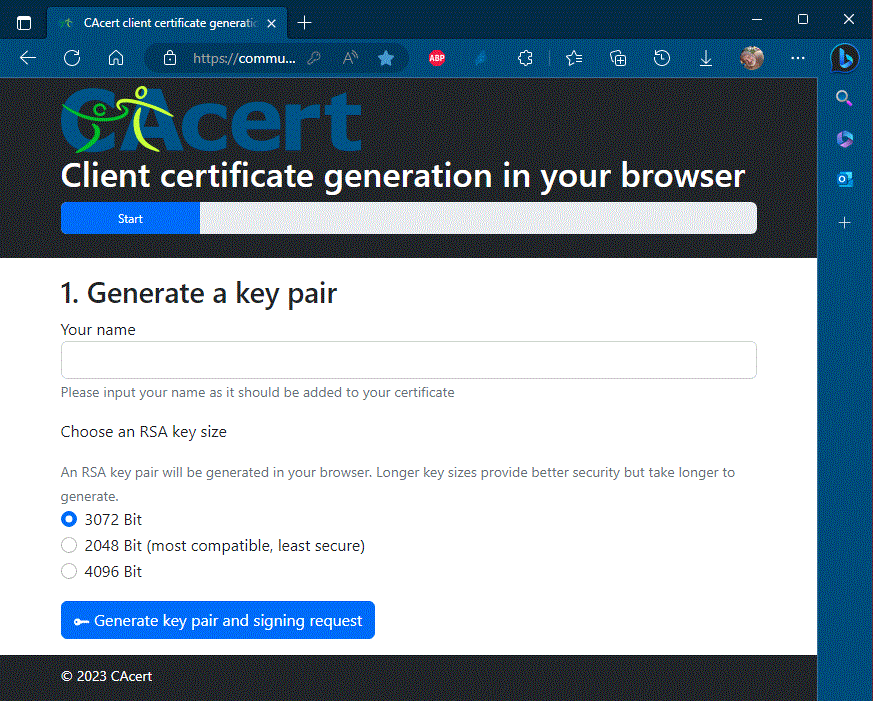
Fill in your name - since it will be completed by the Cacert website, it can be basically any. Select the length of the keys - the power of encryption. The preset value is 3072. The value of 2048 is marked as most compatible but least safe. Press the blue "Generate..." button and wait for the keys to be generated; the progress can be viewed on the bar in the page header.
2. Transfer CSR to Cacert form
After generating, you can see this on the page:
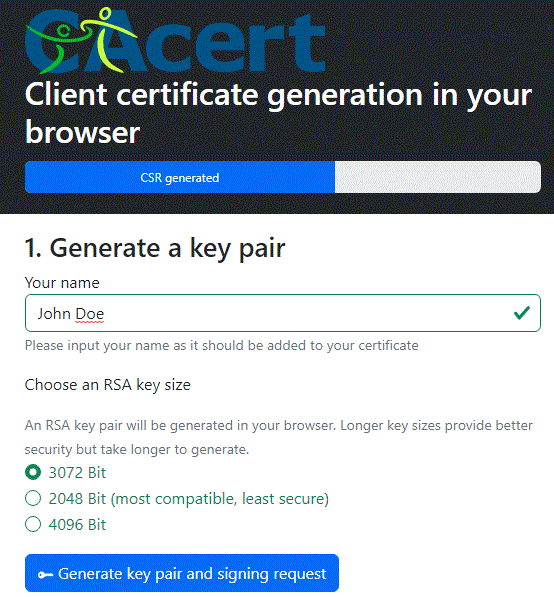
The bar is blue and announces that a CSR is prepared to be submitted to the CAcert's signer. You can see the rest of the page by shifting the page down:

The red button will show the new private key, which you probably won't use. The following is a Base64 CSR listing and a blue button to get the CSR to the Clipboard, which will be useful in the next step.
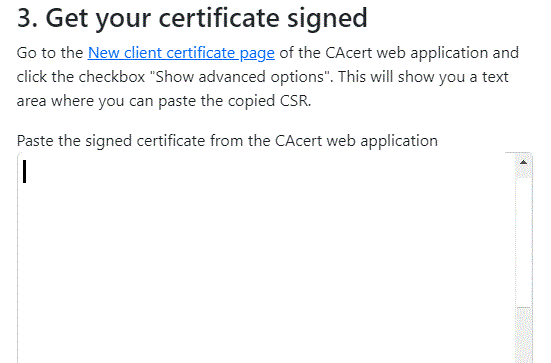
3. Issue the certificate
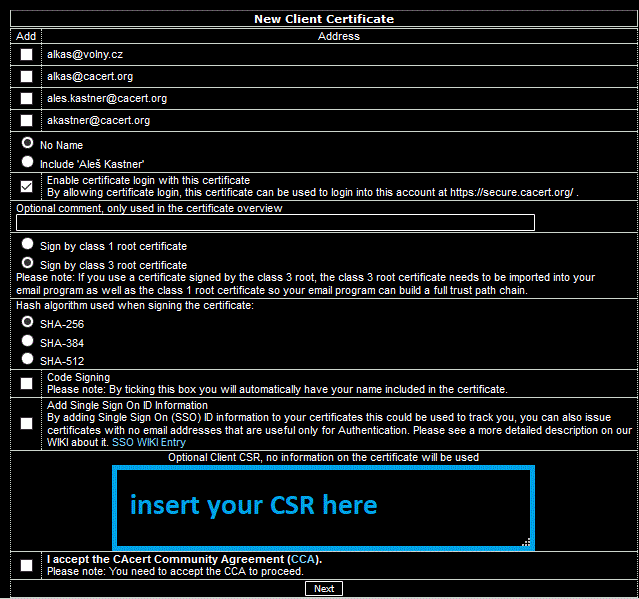
In the next text you can see a link to the Cacert Web. Use it, log in, go to the page "Client Certificates - New". Here, select email addresses for the certificate, and/or inserting your name to the certificate. Put the cursor in the large text box and insert the CSR from the clipboard using the Ctrl-V key combination. With the number of AP points > 49, you can also select code signing and/or SSO. Do not forget to check the confirmation of the CCA agreement. Press "Next".
After the certificate is issued, the page where it is displayed will be shown. Select the whole range e.g. with the mouse, including the initial and final comments and use Ctrl-C to transfer it into the Clipboard.
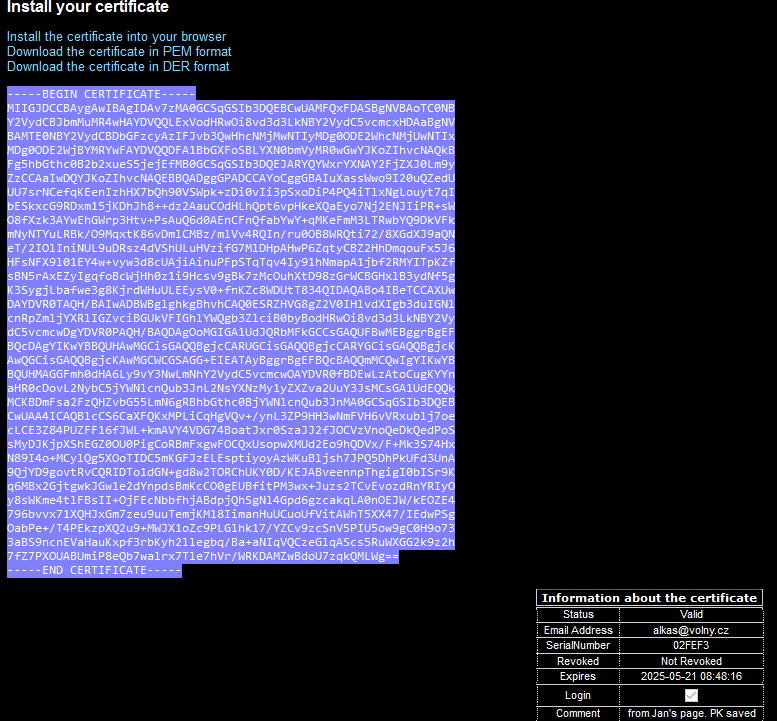
Do not use the links at the top of this page. It is useless, because:
- You have no way how to import the private key, except from a P12 formatted file, which you don't have ready yet.
The P12 formatted file is the best backup of your new certificate & private key, thus there is no need to save the only certificate in other formats.
Now return to the application. There, put the cursor in the big text box below under the link to Cacert Web. Use Ctrl-V to insert the certificate from the clipboard to that text box.
4. Create a P12 formatted file containing the new certificate and the new private key
The application has both a certificate and a private key (which hasn't been sent anywhere) available now. It asks for a password for the security encryption of the private key. Create a password and enter it. You can see it by holding the mouse on the icon on the right. Then, press the blue "Prepare download" button.
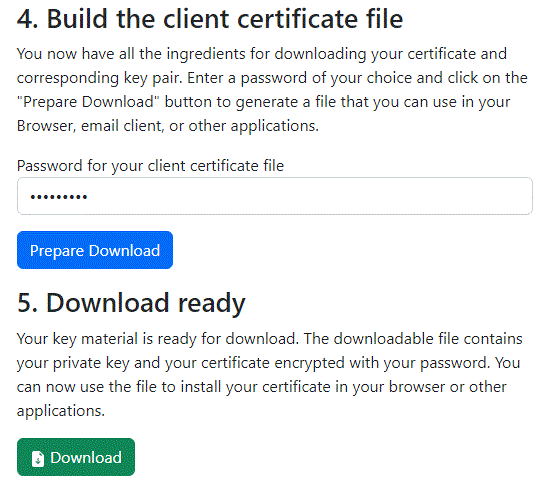
5. P12 file download
Finally, the text appears that the P12 file is ready. You can download it now, and then import it into browsers, Windows OS, and/or other software. Press the green button "Download", name the file (preserving the suffix .p12) and save it.
6. Import a P12 file into a browser or operating system
Principles
You can import the P12 file (.p12 or .pfx extension):
- to the Windows OS using the MMC-Certificates utility,
- to Windows OS via the Certificate Manager in Edge, Chrome, Opera, Vivaldi, Brave (and other browsers using Windows certificate store),
- to the browser's own certificate store (Firefox, Basilisk, Seamonkey, Palemoon and others),
- to a custom store on Linux systems (Firefox, Chromium and other browsers used here).
How to open Certificate Manager for the most commonly used browsers:
- (Unless otherwise noted, you can access Settings using the "3 horizontal bars" icon, called a "hamburger", in the upper right corner of the window.)
- Edge ver. 114.0.1823.51: Settings - Privacy,... - In the right pane of the window, scroll down to the Security heading - the Manage Certificates link will bring up the Windows Personal Certificate Management system window
- Chrome ver. 114.0.5735.134: Settings - Privacy and Security - in the right pane of the window, scroll down to the Security link - scroll down and use the "Manage Device Certificates" link - the Windows Personal Certificate Management system window will appear
Opera ver. 99.0.4788.47: Icon top left corner of the window - Settings - Privacy & Security - in the right pane, use the Security link - use the "Manage Device Certificates" link, which again displays the Windows Personal Certificate Management system window
Vivaldi ver. 6.1.3035.75: Icon top left corner of the window - Settings - Privacy & Security - in the right pane, scroll down to SECURITY - click "Manage Certificates" to display the Windows Personal Certificate Management system window
Brave ver. 1.52.126: Settings - Privacy & Security - in the right pane, scroll down to Security - use the "Manage Device Certificates" link to display the Windows Personal Certificate Management system window again
Firefox ver. 114.0.1: Settings - Privacy & Security - in the right pane of the window, scroll down to the Certificates heading - click the "View Certificates..." button
- Basilisk ver. 2023.05.17: Preferences - Advanced - in the right pane at the top select Certificates - button "View certificates"
Seamonkey ver. 2.53.16: Edit menu - Preferences - expand Privacy & Security - in the right pane, click "Manage Certificates" button
Palemoon ver. 32.2.0: blue PaleMoon rectangle on top left - Preferences, or menu Tools - Preferences - new dialog box, top right Advancsd - View Certificates button
Chromium ver. 114.0.5735.106: Settings - Privacy & Security - in the right pane of the window, go to the Security link - scroll down to the Manage Certificates link - go to the
Certificate Manager Firefox/Basilisk/Palemoon/Seamonkey
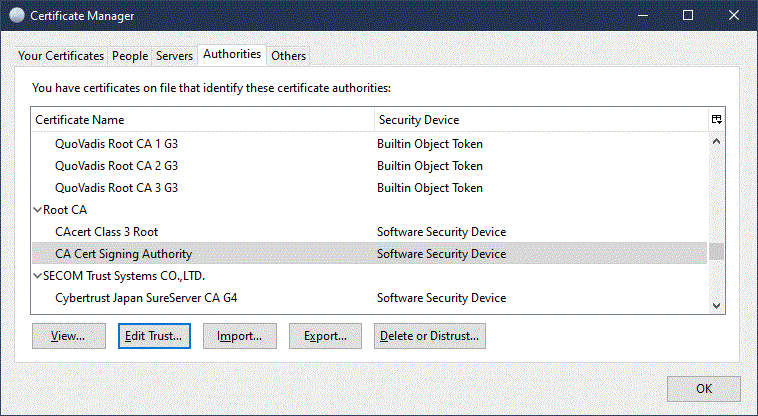
The CAcert root certificate can be found in the Authorities tab under "R" (Root CA). Use the highlighted button to check your machine's trust in the CAcert root certificate. In the next dialog, all options for "Root CA" - "CA Cert Signing Authority" must be checked.
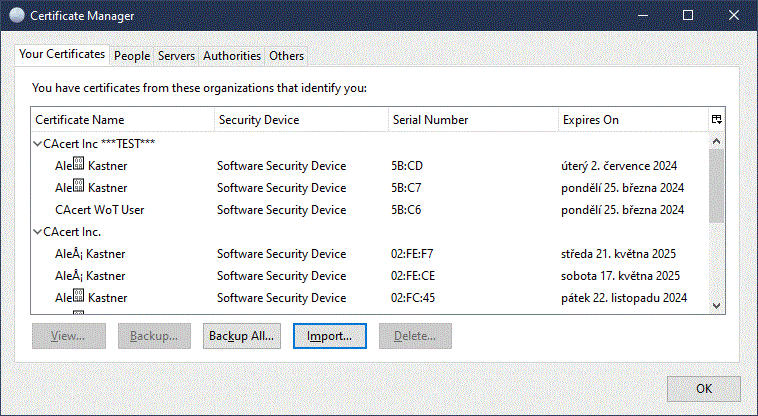
Import the created keys and certificate from the P12 file on the "Your Certificates" tab by clicking the "Import..." button. Enter the name of the created P12 file and the password you set when creating the file. The Certificate Manager should report success and after pressing OK the imported certificate will appear in his window.
Chrome Certificate Manager
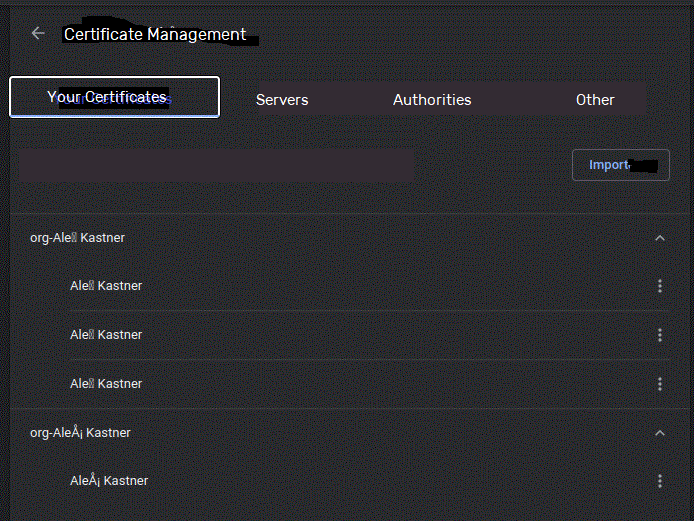
In the Chrome Certificate Manager on Linux, the "Your Certificates" tab just says "org-" and the name of the certificate. When expanded, you can then see the names of your certificates and view their contents, where you can only see which authority issued them. To add a new certificate from the P12 file, click the "Import" button. Again, you need to enter the private key password.
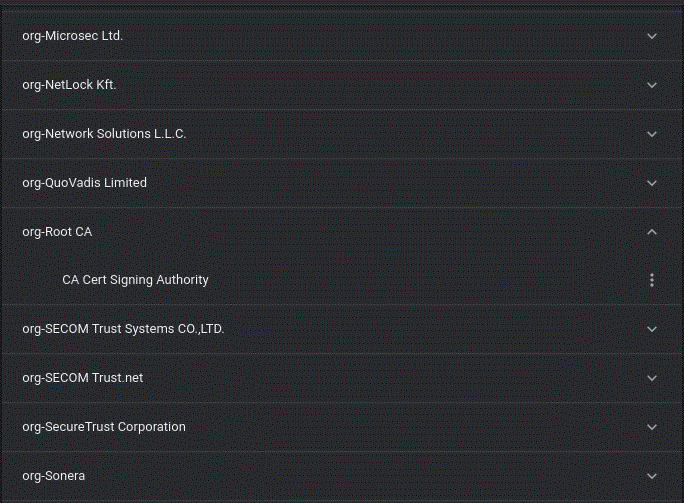
If you want to check the trust in a certification authority, you can find it on the Authorities tab. The name starts with org-Root CA, which can be expanded as indicated. The trust can then be edited by selecting "Edit" from the menu on the right (3 dots). Check all options if they are not already selected.
Windows certificate management available from browsers
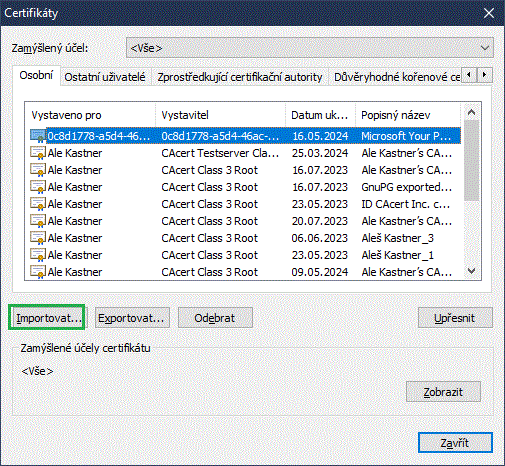
- Labels:
- Osobní - Personal (Your Certificates)
- Ostatní uživatelé - Other Users
- Zprostředkující... - Intermediate CA's
- Důvěryhodné... - Trusted Root CA's
- Vystaveno pro - Issued for
- Vystavitel - Issuer
- Datum uk... - Date of Expiration
- Popisný název - Descriptive Name
- Importovat - Import
- Odebrat - Remove
- Zobrazit - Display
- Zavřít - Close
Zamýšlený účel: <Vše> - Purpose: <All>
If you are running a browser on Windows, using the system storage, then you will see this window as the Certificate Manager window. It is actually part of the MMC-Certificates utility view of the system store. What is missing here is the left - tree - pane where we would see that these are the personal certificates of the current user. Here we can import the created P12 file using the highlighted button. This will launch the Certificate Import Wizard, where you select the P12 file (with the .p12 extension) to import.
 Note that the following file selection defaults to .crt/.cer files; you need to select "Personal Information Exchange" files with .pfx/.p12 extensions.
Note that the following file selection defaults to .crt/.cer files; you need to select "Personal Information Exchange" files with .pfx/.p12 extensions. 
The wizard will walk you through the entire import process. Once it is complete, you can check the imported certificate by opening it. At the bottom of the certificate window, you should see a key icon and the text "You have a private key that matches this certificate".
On the other hand, it is not necessary to check the trust to the CAcert root certificate (class 1), because it has to be confirmed when importing it into Windows.
Note: Using P12 files, it is possible to have a scenario where the CAcert root certificates are not yet installed on the device where you want to install the certificate and private key. You can also install these from the P12 file at the same time, but you must follow certain rules: |
1. When importing with Windows as the target, you must leave the automatic storage selection in the Wizard so that the different parts of the P12 file fit into the correct storage locations. |
2. When importing targeting a custom browser/Linux repository, you need to check/set the trust to the class 1 root certificate after importing. |