The basic level of administration in www.cacert.org is called system admin. This is set in your normal member account by the Application Engineer (3rd line support) when a new SE is approved. Once set, additional features become available. You can use them to set some specialist levels as well.
operating
System admin adds an additional menu item, bottom right, with two options Find User and Find Domain.
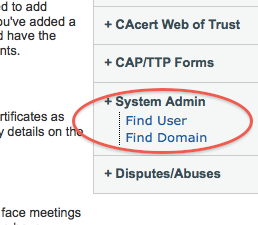
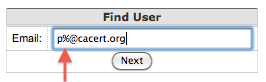
Find User: can search on either email address or on user-id number.
suggest simplify, add Find user-id.
need, add Find Name.
Find Domain: can search on a domain.
- (Others are added optionally, see below.)
Search features systems use % as a wildcard. E.g., %cacert% will find all with cacert in them.
The User Display
Using the Find User interface, SE can open the Details of the user account. This is similar to the details seen by the member herself, but with more system options.
Name. Top block of Name/DoB details are changeable, hit Go. Note that this requires authorisation from Arbitrator, or should be a zero-points account.
Flags:
Is Assurer. The Assurer setting can be overridden, but this is not permanent and will be again overridden when a new calculation is made (new points).
Blocked Assurer. More effectively, the Blocked field will stop a person doing assurances.
Account Locking. This will stop an account from being able to be logged in.
Delete Account. Danger: this does not work as advertised, only use if absolutely sure you know what it does. Deletion of an account needs authority of Arbitrator. More likely, the account will be frozen and name fields set to xXxxxxxXXX. See also the paragraph below.
Password Qs: Clicking this will show you the secret password questions of the member. Only click when engaged in recovery with member. A message of warning will be sent to the member. Record this event, as a user will complain if it is not expected, and we need to figure out who did it and why.
Show Assurances. Two links give two tables at bottom of page.
Show Assurances the user gave. This table has a revoke button. If the assurer notices an mistake, then assurer can immediately request a revocation (24 hours).
Misc
Ad Admin : if set, the member gets an additional menu item, Adverts in the system menu as above.
1: can enter Adverts into the system.
2: can approve adverts entered by the previous role.
Location admin gives access to the location database. This is allocated on an ad hoc basis (use common sense). Warn the member that it is the production database, and to be careful.
- Hovering over one of the digits gives a command that includes the userid but you have to know what you are looking for in the URL.
- The userid is used in some links, some hidden forms, some email pings. Should file a bug.
- Most changes are not immediate, the member has to log-out and log-in again.
- 3rd level support is application engineer (pg).
- Tverify, TTP are both 'off', pending new policies.
Orgs
When approved, the Organisation Assurer button can be turned on for an account. This provides more options to the OA.
Note that domains in ORG accounts need Org Admin as well to see properly.
About Deleting and Deactivating Accounts
D E P R I C A T E D - D E P R I C A T E D - D E P R I C A T E D - D E P R I C A T E D
go instead Delete Account Procedure for Support-Engineers v3
This is written from a theoretical point of view by playing a bit with the testsite. It has to be reviewed by an experienced Support Engineer. Till this is done use with extreme caution, but it looks like someone has to start! BernhardFröhlich
Before deactivating an account, usually it should be made sure that no resources like mail addresses or domains are used (and thereby blocked) by the account. Also certificates might have to be revoked.
The process is in summary this:
- Take a snapshot of the account information and send to the Arbitrator (if the Arbitrator requests this).
- Hijack the account.
- Set the fields to dummy values.
- Set the account as "blocked".
- Report back to the Arbitrator that it is done.
- Forget the password.
Hijacking the Account
Currently this can not be done using the standard admin interface, so the account has to be "hijacked" by the SE. To hijack an account just set the password of the account to a random value (if possible, generated by some true random generator). Then you can use the newly set password to log in to the account and do whatever the rightful owner could have done with it.
Process of Account "removal"
Especially, these steps are done on the account.
This is a massive mutilation of an account, so just make sure that an Arbitrator has authorized you to do so!
 It should be done only with accounts which are intended for deletion or permanent deactivation!
It should be done only with accounts which are intended for deletion or permanent deactivation! 
- after hijacking the account:
- Revoke certificates
Add a new email address like: arbitration_<arb#>@cacert.org and make that the primary email address
- Remove all the other email addresses
- Remove domains
- Fill Secret Questions with junk (answers and questions)
- Fill the Givenname, Middlename, Lastname and Suffix with the arbitration case number (like a20101225.1)
- Set the DoB to 1900-01-01 or 1970-01-01
- reset all flags
- Finally, set the account as "blocked".
Remember that, once you have done this, the rightful owner of the account cannot log in to the account any more, and the account is not usable in any fashion. But the data trail is preserved internally, if it is ever required.
Delete from webinterface
The "Delete Account" link on the web interface does the following:
- Revokes all domain (server) certs
- Marks all domains associated with the account as deleted
- Revokes all email certs
- Marks all associated emails as deleted
Deletes all entries in the Org-Table which refer to the user. Something with OrgAssurance, I have to look up the exact consequences of this
Fills password reset questions & answers with a junk (AK, 20210830)
- Marks the user account as deleted
(N.B.: The revocation timestamps of certificates is set to "1970-01-01 10:00:01". IMHO it should be set to the current timestamp...)
So, strictly speaking the "delete" link does not delete database records, it just marks them as deleted, so they won't show up in the web application. Someone with SQL access to the database may still look up the status of the account at the time when it was "deleted" and may even restore most of the account.
I'm not sure if this satisfies data protection laws if a user requests deletion of his/her personal data...
