česky | english
CAcert Public-Root-Certificates manual import on Windows
By Stefan Thode
Reasons to import the CAcert Public-Root-Certificates manual:
- You use Windows 8/8.1/10 Technology (incl. Server 2012/2016/2019) at that the EXE-Installer does not work.
- You want to have them available for all users using this computer
- You want to have them available for services running on Windows like Outlook, Internet Explorer/Edge, Google Chrome, Operah, MS-Exchange, MS Internet-Information-Server or any other software that uses the windows certificate storage.
Preparing
Download the CAcert Public-Root-Certificates from https://www.cacert.org/index.php?id=3 in PEM Format. This results in downloading the Files "root_X0F.crt" and "class3_x14E228.crt" by using Mozilla Firefox.
Go to CAcert's webpage with root certificates and their fingerprints.
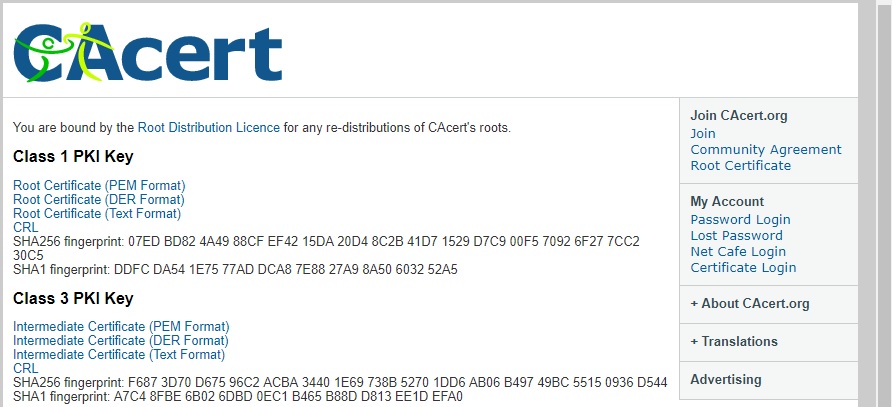
The link "Root certificate (PEM format)" corresponds to root_X0F.crt etc.:
Link |
Corresponding filename |
Class 1 PKI key |
|
Root certificate (PEM format) |
root_X0F.crt |
Root certificate (DER format) |
root_X0F.der |
Root certificate (Text format) |
root_X0F.txt |
Class 3 PKI key |
|
Intermediate certificate (PEM format) |
class3_x14E228.crt |
Intermediate certificate (DER format) |
class3_x14E228.der |
Intermediate certificate (Text format) |
class3_x14E228.txt |
Start "Microsoft Management Console" and prepare it for organize certificates. Start "MMC.EXE" as Administrator
![]() Note: If you are using a Windows Domain and are a Domain Administrator you can install the certificate for all computers of the domain at once! See the paragraph #Installation_in_Windows_Domain below.
Note: If you are using a Windows Domain and are a Domain Administrator you can install the certificate for all computers of the domain at once! See the paragraph #Installation_in_Windows_Domain below.
Add Snap-In for Certificates
In the File menu, you can find the function "Add/Remove Snap-In"
Add Snap-In "Certificates" for the "Computer Account" and in the next screen for the "Local Computer".
![]() Note: To install the certificate for the computer you'll need administrative rights on the computer. If you are not an administrator MMC.EXE automatically selects "Current User" instead of "Local Computer". Unless the administrators have explicitly forbidden this, you can still install the root certificate following the same procesure as described here. In this case the certificate is only installed for your personal user account. If someone else logs in to the same computer, the certificate will not be installed for him/her.
Note: To install the certificate for the computer you'll need administrative rights on the computer. If you are not an administrator MMC.EXE automatically selects "Current User" instead of "Local Computer". Unless the administrators have explicitly forbidden this, you can still install the root certificate following the same procesure as described here. In this case the certificate is only installed for your personal user account. If someone else logs in to the same computer, the certificate will not be installed for him/her.
You can see the Certificates Organization for the Computer Certificates Store. Expand the certificates folder.
Import "root" into "Trusted Root Certification Authorities"
The Import Wizard starts, now. Use "Local Machine" and "Next".
Browse for file "root_X0F.crt"
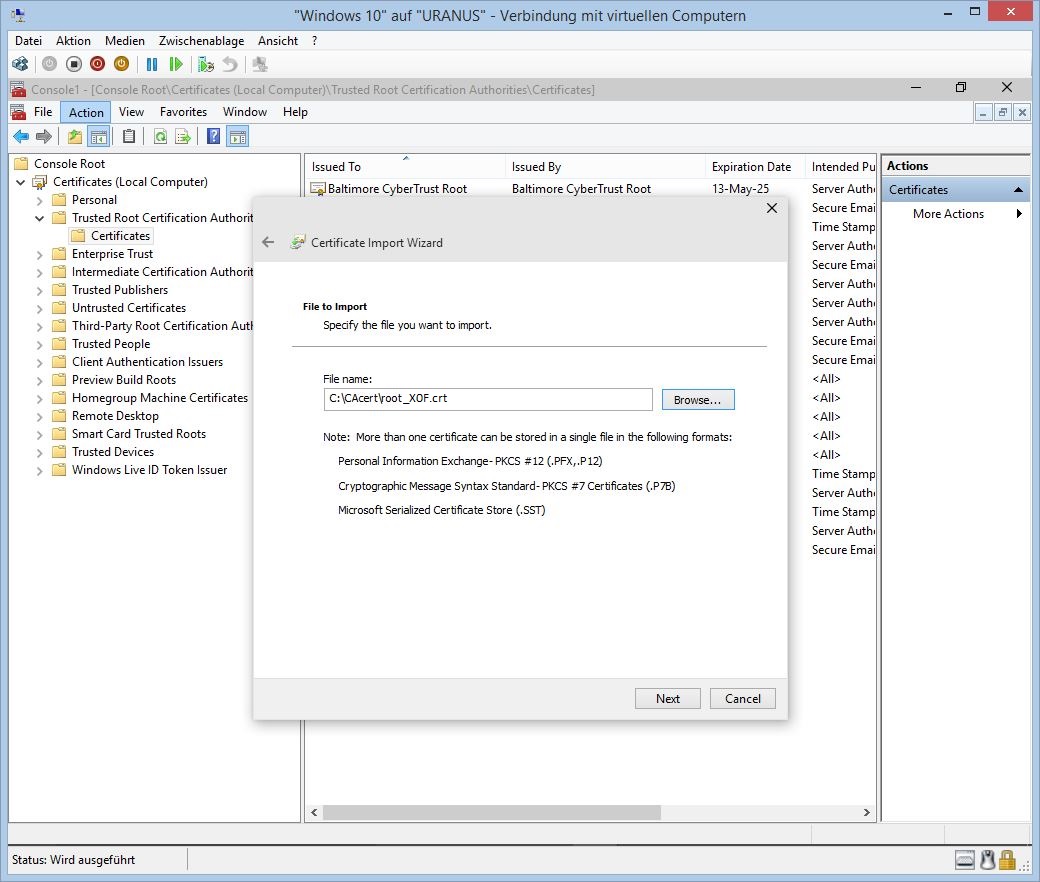
Browse for the correct Certificate Location for "root" (Trusted Root Certification Authorities)
Finish the import of "root"
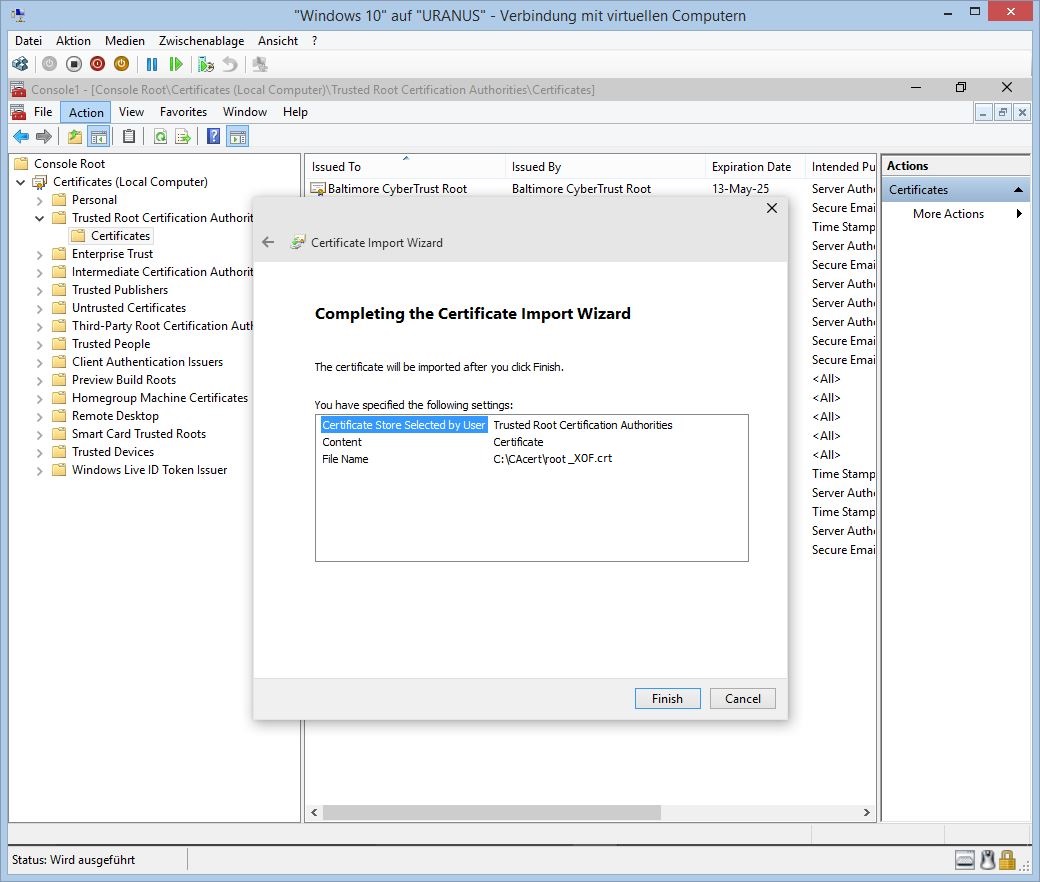
The next dialog may appear. Confirm that you want to import the root certificate, and that you trust the issuer. You can also check the fingerprints against the CAcert roots webpage (recommended).
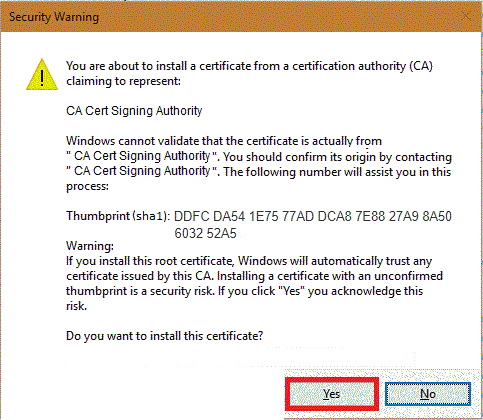
And be sure you trust it. Rightclick "root" as "CA cert Signing Authority" and select Properties.
Enable all purposes for this certificate.
Import "class3" into "Intermediate Certification Authorities"
The Import Wizard starts again.
Browse for file "class3_x14E228.crt"
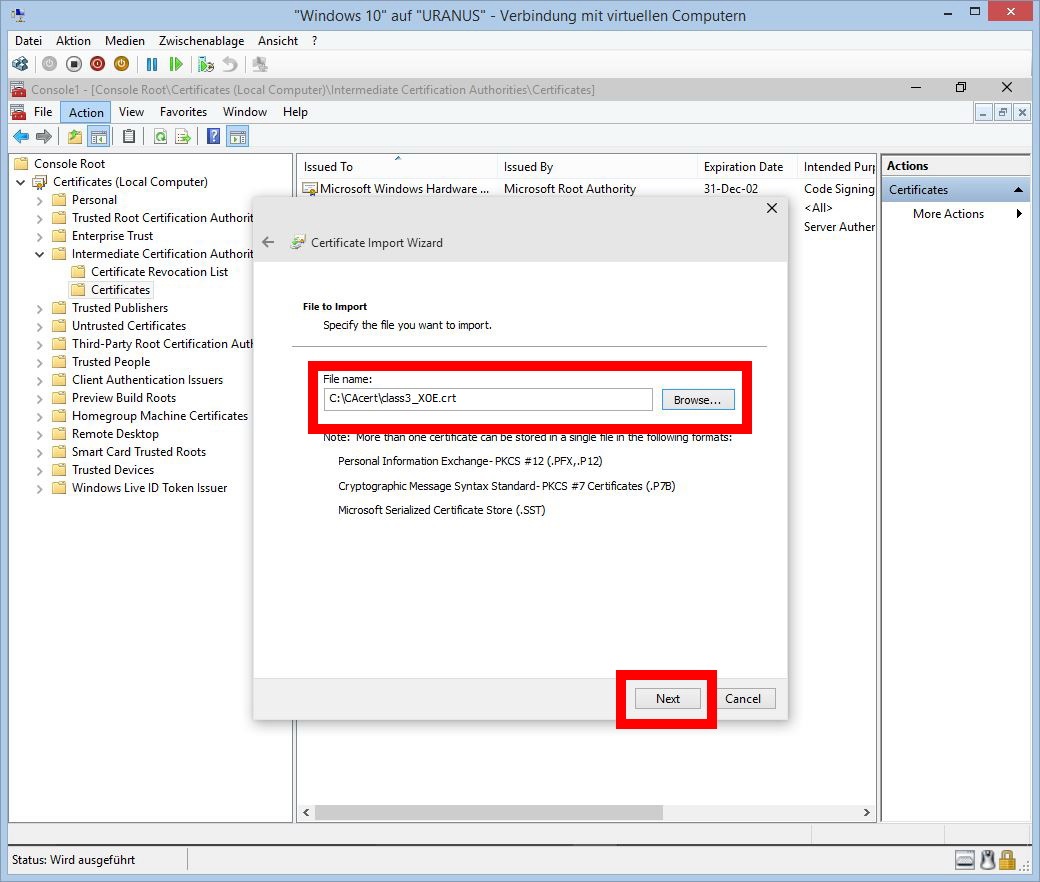
Browse for the correct Certificate Location for "class3" (Intermediate Certification Authorities)
Finish the import of "class3"
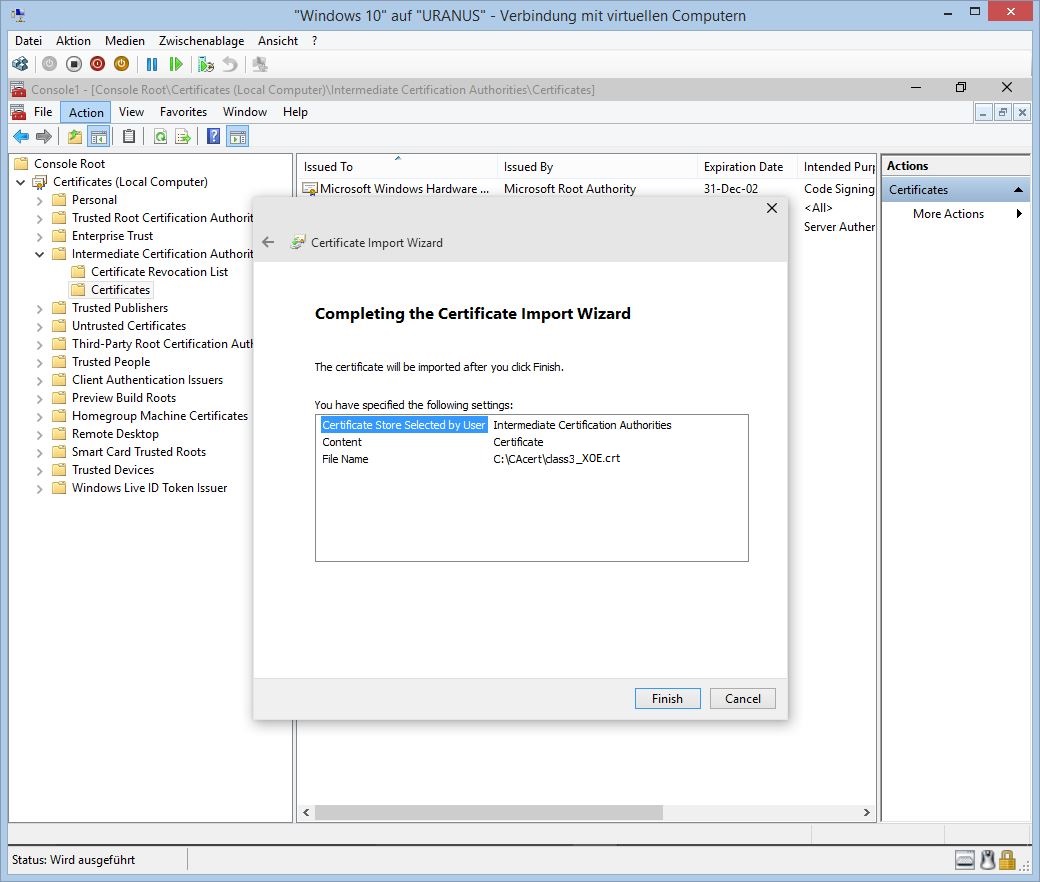
And again be sure you trust it. Rightclick "class3" as "CAcert Class 3 Root" and select Properties.
Enable all purpose for "class3"
The CAcert Public-Root-Certificates are successfully installed for products that uses the Windows Certificate Stores. Other Products as Firefox or Thunderbird have their own Certificate Stores, you have to import the Public-Roots into these Certificate Stores for using these products.
Installation in Windows Domain
It is possible to install certificates for all computers in a Windows Domain by using the Group Policy Editor (procedure tested on Server 2012 R2 with english language settings):
- Log in to a Domain Controller using an account in the Domain Admins group
- Start MMC
- Add the "Group Policy Management Editor" Snap-In
- Select the "Default Domain Policy" as Group Policy Object to be edited
In the policy tree find Default Domain Policy -> Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies -> Trusted Root Certification Authorities
Use the menu item "Action... -> Import" to import the CAcert root certificate.
- Now the CAcert root should be shown in the list window on the right side of the treeview
In the policy tree find Default Domain Policy -> Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies -> Intermediate Certification Authorities
- Import the Class 3 certificate here
- Allow some time for the group policy to distribute. A day should be enough, most time the distribution is considerably faster
Use the Certificates Snap-In as described above in #Add_Snap-In_for_Certificates on any domain computer to verify that the distribution is complete. The imported certificates should already be visible in the corresponding folders.
